Source: www.securityweek.com – Author: Ionut Arghire Microsoft on Friday announced an expansion to its Copilot bug bounty program to include more consumer products and provide researchers...
Day: February 11, 2025
HPE Says Personal Information Stolen in 2023 Russian Hack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Hewlett Packard Enterprise has started notifying people that their personal information was likely compromised in a December 2023 hack attributed...
Indiana Man Sentenced to 20 Years in Prison for Hacking, $37 Million Crypto Theft – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire An Indiana man was sentenced to 20 years in federal prison for hacking into an investment holdings company’s servers and...
Information of 120,000 Stolen in Ransomware Attack on Georgia Hospital – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Memorial Hospital and Manor is notifying 120,000 individuals that their personal information was stolen in a November 2024 ransomware attack....
Can AI Early Warning Systems Reboot the Threat Intel Industry? – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine The cyber threat intelligence business has struggled to become a major market category, hampered by stale data, limited information sharing,...
Top 5 ways attackers use generative AI to exploit your systems – Source: www.csoonline.com
Source: www.csoonline.com – Author: Feature 11 Feb 20258 mins MalwarePhishingThreat and Vulnerability Management Cybercriminals are increasingly exploiting gen AI technologies to enhance the sophistication and efficiency...
WTF? Why the cybersecurity sector is overrun with acronyms – Source: www.csoonline.com
Source: www.csoonline.com – Author: Acronyms are an easy way to remember and reference long-winded technical terms, but sometimes too many can hinder understanding or even become...
Die besten DAST- & SAST-Tools – Source: www.csoonline.com
Source: www.csoonline.com – Author: Tools für Dynamic und Static Application Security Testing unterstützen Entwickler dabei, Code-Fehler und Sicherheitslücken schneller zu erkennen. Tools für Dynamic und Static...
Datenleck durch GenAI-Nutzung – Source: www.csoonline.com
Source: www.csoonline.com – Author: Eine aktuelle Studie zeigt: Fast zehn Prozent der KI-Eingabeaufforderungen von Mitarbeitern enthalten sensible Daten. Viele Mitarbeiter teilen sensible Unternehmensdaten, wenn sie generative...
Hackers breach Microsoft IIS services using Cityworks RCE bug – Source: www.csoonline.com
Source: www.csoonline.com – Author: The deserialization flaw allows attackers to remotely execute arbitrary codes on customers’ IIS web servers. Hackers are exploiting a high-severity remote code...
Why cyber hygiene remains critical in the era of AI-driven threats – Source: www.csoonline.com
Source: www.csoonline.com – Author: How IT leaders can build the foundations of a robust security strategy today Cyber-attacks are an assumed inevitable for businesses today. As...
Fortifying cyber security: What does secure look like in 2025? – Source: www.csoonline.com
Source: www.csoonline.com – Author: Subheading: How businesses can adapt to AI driven attacks, build cyber resilience and navigate the regulatory demands in 2025 The evolving cybersecurity...
CIO Cloud Summit: Best Practices von Anwendern für Anwender – Source: www.csoonline.com
Source: www.csoonline.com – Author: Erfahren Sie auf dem CIO Cloud Summit in Köln aus erster Hand, wie deutsche Unternehmen ihre Cloud-Transformation gemeistert haben. Dabei spielen KI-Projekte...
Nearly 10% of employee gen AI prompts include sensitive data – Source: www.csoonline.com
Source: www.csoonline.com – Author: Enterprise users are leaking sensitive corporate data through use of unauthorized and authorized generative AI apps at alarming rates. Plugging the leaks...
The Art of Human-AI Synergy: A Framework for Smart Collaboration – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author The integration of AI into professional workflows has transitioned from novelty to necessity, particularly in...
DEF CON 32 – Eradicating Hepatitis C with BioTerrorism – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Monday, February 10, 2025 Home » Security Bloggers Network » DEF CON 32 – Eradicating Hepatitis C with BioTerrorism Authors/Presenters:...
MY TAKE: Securing the Internet of Everything: why self-healing devices are the next frontier – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido By Byron V. Acohido We’re just getting started down the road to the Internet of Everything (IoE.) To get there –...
Chinese DeepSeek AI App: FULL of Security Holes Say Researchers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings iPhone app sends unencrypted data to China—and Android app appears even worse. DeepSeek has yet another privacy palaver. Researchers say its...
Randall Munroe’s XKCD ‘Suspension Bridge’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic humor & dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
Phishing Season 2025: The Latest Predictions Unveiled – Source: securityboulevard.com
Source: securityboulevard.com – Author: Diana Shtil Every year, cybercriminals sharpen their tools and refine their tactics to exploit network and security vulnerabilities. Gone are the days...
Attackers Use 2.8 Million Devices in Major Brute Force Attack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Threat actors are pounding edge security devices from the likes of Palo Alto Networks, Ivanti, and SonicWall in a massive...
Leveraging Microsoft Text Services Framework (TSF) for Red Team Operations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Harry Hayward The Praetorian Labs team was tasked with identifying novel and previously undocumented persistence mechanisms for use in red team engagements....
DEF CON 32 – Hunters And Gatherers A Deep Dive Into The World Of Bug Bounties – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Monday, February 10, 2025 Home » Security Bloggers Network » DEF CON 32 – Hunters And Gatherers A Deep Dive...
The Critical Role of CISOs in Managing IAM – Including Non-Human Identities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dwayne McDaniel Who should own IAM in the enterprise? Identity and access management (IAM) started as an IT function, with the entire...
Apple Patches Actively Exploited iOS Zero-Day CVE-2025-24200 in Emergency Update – Source:thehackernews.com
Source: thehackernews.com – Author: . Apple on Monday released out-of-band security updates to address a security flaw in iOS and iPadOS that it said has been...
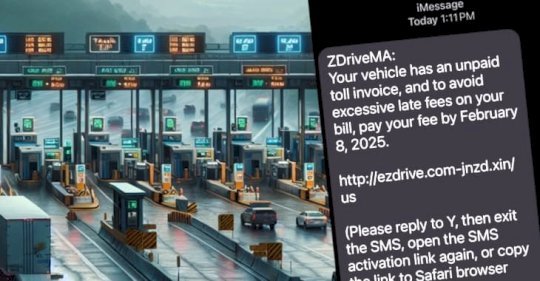
Toll booth bandits continue to scam via SMS messages – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley North American drivers are continuing to be barraged by waves of scam text messages, telling them that they owe money...