Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author The integration of AI into professional workflows has transitioned from novelty to necessity, particularly in...
Day: February 11, 2025
DEF CON 32 – Eradicating Hepatitis C with BioTerrorism – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Monday, February 10, 2025 Home » Security Bloggers Network » DEF CON 32 – Eradicating Hepatitis C with BioTerrorism Authors/Presenters:...
MY TAKE: Securing the Internet of Everything: why self-healing devices are the next frontier – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido By Byron V. Acohido We’re just getting started down the road to the Internet of Everything (IoE.) To get there –...
Chinese DeepSeek AI App: FULL of Security Holes Say Researchers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings iPhone app sends unencrypted data to China—and Android app appears even worse. DeepSeek has yet another privacy palaver. Researchers say its...
Randall Munroe’s XKCD ‘Suspension Bridge’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic humor & dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
Phishing Season 2025: The Latest Predictions Unveiled – Source: securityboulevard.com
Source: securityboulevard.com – Author: Diana Shtil Every year, cybercriminals sharpen their tools and refine their tactics to exploit network and security vulnerabilities. Gone are the days...
Attackers Use 2.8 Million Devices in Major Brute Force Attack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Threat actors are pounding edge security devices from the likes of Palo Alto Networks, Ivanti, and SonicWall in a massive...
Leveraging Microsoft Text Services Framework (TSF) for Red Team Operations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Harry Hayward The Praetorian Labs team was tasked with identifying novel and previously undocumented persistence mechanisms for use in red team engagements....
DEF CON 32 – Hunters And Gatherers A Deep Dive Into The World Of Bug Bounties – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Monday, February 10, 2025 Home » Security Bloggers Network » DEF CON 32 – Hunters And Gatherers A Deep Dive...
The Critical Role of CISOs in Managing IAM – Including Non-Human Identities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dwayne McDaniel Who should own IAM in the enterprise? Identity and access management (IAM) started as an IT function, with the entire...
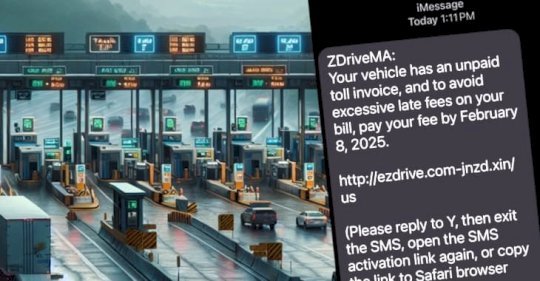
Toll booth bandits continue to scam via SMS messages – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley North American drivers are continuing to be barraged by waves of scam text messages, telling them that they owe money...