Source: www.hackerone.com – Author: HackerOne. Curious about vulnerability disclosure? We explain what it is, why there may be friction between the researcher and the organization, and...
Day: February 5, 2025
Jedox’s Journey with HackerOne: A Q&A with CTO, Vladislav Maličević – Source:www.hackerone.com
Source: www.hackerone.com – Author: elizabeth@hackerone.com. Vladislav Maličević is the Chief Technology Officer at Jedox, a leading global provider of cloud-based enterprise performance management solutions for Financial...
How Trustpilot Manages Risk by Working with Ethical Hackers – Source:www.hackerone.com
Source: www.hackerone.com – Author: HackerOne. At our 2021 Security@ conference, we spoke with Stu Hirst, CISO at consumer review site Trustpilot. Trustpilot’s mission is to create...
International Day of Women and Girls in STEM Celebration
Join us on Feb. 11 for this free virtual event featuring Congresswoman Luz Rivas (D-CA 29th) and a panel of CEOs from nonprofit engineering organizations. Source...
Celebrate Black History Month With SWE
Browse through this compilation of some of our top blog posts, podcast episodes, magazine articles, and online courses highlighting Black women and STEM allies. Source Views:...
Deepfakes and the 2024 US Election – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Interesting analysis: We analyzed every instance of AI use in elections collected by the WIRED AI Elections Project (source for...
How Imperva Infused AI Throughout Research and Development – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Holmes The Age of AI Is Upon Us The current pace of technological change beggars’ belief. Generative Artificial Intelligence (GenAI), released...
Secure by Design and Secure by Default: Why you need both for AppSec – Source: securityboulevard.com
Source: securityboulevard.com – Author: John P. Mello Jr. The relationship between the two software security initiatives promoted by the U.S. Cybersecurity and Infrastructure Security Agency (CISA)...
DEF CON 32 – Hacker Vs. AI Perspectives From An Ex-Spy – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Tuesday, February 4, 2025 Home » Security Bloggers Network » DEF CON 32 – Hacker Vs. AI Perspectives From An...
Cyberhaven: A Wake-Up Call for Consent Phishing Risks | Grip – Source: securityboulevard.com
Source: securityboulevard.com – Author: Grip Security Blog The Cyberhaven breach is more than just an isolated incident—it’s a wake-up call for organizations everywhere. Attackers targeted extension...
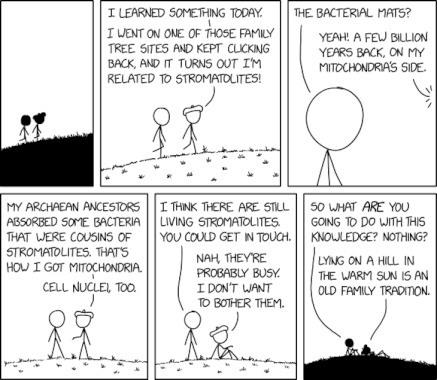
Randall Munroe’s XKCD ‘Stromatolites’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic humor & dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
Survey Sees Organizations Being Overwhelmed by Remediation Challenges – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard A survey of 150 security decision makers in the U.S., published today, finds that close to two thirds of cybersecurity...
Anomalies are not Enough – Source: securityboulevard.com
Source: securityboulevard.com – Author: Evan Powell Mitre Att&ck as Context Introduction: A common theme of science fiction authors, and these days policymakers and think tanks, is how...
AttackIQ Bolsters Cyber Defenses with DeepSurface’s Risk-Analysis Tech – Source: securityboulevard.com
Source: securityboulevard.com – Author: George V. Hulme This week, AttackIQ acquired DeepSurface to broaden its vulnerability and attack path management capabilities to help enterprises identify and...
How bots and fraudsters exploit free tiers in AI SaaS – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sebastian Wallin The latest wave of artificial intelligence (AI) improvements significantly improved the quality of models for image and text generation. Several...
When Stalking Looks Like Affection, Admiration, or Anger — The Challenge for EP Teams – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cynthia Marble Article How to strengthen your executive protection program to address and mitigate the impacts of stalking aimed at executives Related...
Online food ordering and delivery platform GrubHub discloses a data breach – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Pierluigi Paganini February 05, 2025 Online food ordering and delivery platform GrubHub suffered a data breach that exposed the personal...
Netgear urges users to upgrade two flaws impacting WiFi router models – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Pierluigi Paganini February 04, 2025 Netgear disclosed two critical flaws impacting multiple WiFi router models and urges customers to address...
AMD fixed a flaw that allowed to load malicious microcode – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Pierluigi Paganini February 04, 2025 AMD released security patches to fix a flaw that could bypass SEV protection, letting attackers...
Coyote Banking Trojan targets Brazilian users, stealing data from 70+ financial apps and websites – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Pierluigi Paganini February 04, 2025 Coyote Banking Trojan targets Brazilian users, stealing data from over 70 financial applications and websites....