Source: www.hackerone.com – Author: HackerOne. We explain how a bug bounty program identifies vulnerabilities, discuss the program’s benefits, and detail its challenges. What Are the Benefits...
Day: February 5, 2025
Navigating a Safe, Successful Return to Office: 5 Tips for Security Leaders – Source:www.hackerone.com
Source: www.hackerone.com – Author: Guest. A Reprint From Diligent Insights Security leaders have a lot on their plates in these later stages of the continuing COVID-19...
Vulnerability Remediation | A Step-by-Step Guide – Source:www.hackerone.com
Source: www.hackerone.com – Author: HackerOne. Are you wondering about vulnerability remediation? We give you a step-by-step guide to addressing vulnerabilities in your system. Vulnerability remediation is...
How Hackers—the Best Kept Secret in Cybersecurity—Can Help Your Organization Protect its Assets and Improve Security – Source:www.hackerone.com
Source: www.hackerone.com – Author: HackerOne. Last week, HackerOne held its fifth annual one-of-a-kind global Security@ conference featuring the best-kept secret in cybersecurity—hackers. HackerOne CEO, Marten Mikos,...
The Top 5 Cloud Security Risks: How Hacker-Powered Security Can Help – Source:www.hackerone.com
Source: www.hackerone.com – Author: jkanevsky@hackerone.com. Widespread digital transformation means increased cloud security risk. Learn how human intelligence—hacker-powered security—can help your organization defend against new attack vectors,...
Investors, Trump and the Illuminati: What the “Nigerian prince” scams became in 2024 – Source: securelist.com
Source: securelist.com – Author: Anna Lazaricheva Spam and phishing Spam and phishing 05 Feb 2025 minute read “Nigerian” spam is a collective term for messages designed...
Take my money: OCR crypto stealers in Google Play and App Store – Source: securelist.com
Source: securelist.com – Author: Dmitry Kalinin, Sergey Puzan In March 2023, researchers at ESET discovered malware implants embedded into various messaging app mods. Some of these...
Credential Theft Becomes Cybercriminals’ Favorite Target – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: Artur Marciniec via Alamy Stock Photo NEWS BRIEF After analyzing more than a million pieces...
Ferret Malware Added to ‘Contagious Interview’ Campaign – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: imageBROKER.com GmbH & Co. KG via Alamy Stock Photo NEWS BRIEF In a new patch...
Cybercriminals Court Traitorous Insiders via Ransom Notes – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: Mayam studio via Shutterstock Ransomware actors are utilizing a previously unseen tactic in their ransomware...
Chinese ‘Infrastructure Laundering’ Abuses AWS, Microsoft Cloud – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Aleksia via Alamy Stock Photo Researchers have linked the China-based Funnull content delivery network (CDN) to a...
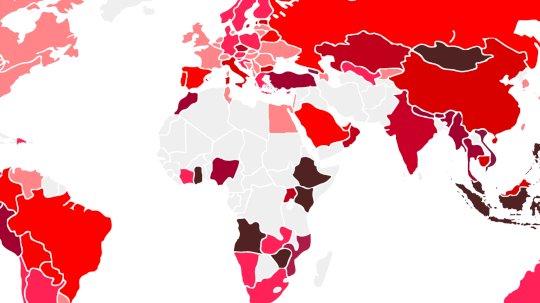
Nigeria Touts Cyber Success, Even as Cybercrime Rises in Africa – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Threat Index global mapSource: Check Point Software Technologies Nigeria’s government has taken a tougher stance against financial fraud...
Black Hat USA – Source: www.darkreading.com
Source: www.darkreading.com – Author: TechTarget and Informa Tech’s Digital Business Combine.TechTarget and Informa TechTarget and Informa Tech’s Digital Business Combine. Together, we power an unparalleled network...
Google: How to make any AMD Zen CPU always generate 4 as a random number – Source: go.theregister.com
Source: go.theregister.com – Author: Iain Thomson Googlers have not only figured out how to break AMD’s security – allowing them to load unofficial microcode into its...
Poisoned Go programming language package lay undetected for 3 years – Source: go.theregister.com
Source: go.theregister.com – Author: Connor Jones A security researcher says a backdoor masquerading as a legitimate Go programming language package used by thousands of organizations was...
Grubhub serves up security incident with a side of needing to change your password – Source: go.theregister.com
Source: go.theregister.com – Author: Connor Jones US food and grocery delivery platform Grubhub says a security incident at a third-party service provider is to blame after...
US accuses Canadian math prodigy of $65M crypto scheme – Source: go.theregister.com
Source: go.theregister.com – Author: Jude Karabus New York feds today unsealed a five-count criminal indictment charging a 22-year-old Canadian math prodigy with exploiting vulnerabilities in two...
New LevelBlue Threat Trends Report gives critical insights into threats – Source:levelblue.com
Source: levelblue.com – Author: hello@alienvault.com. LevelBlue is pleased to announce the launch of the LevelBlue Threat Trends Report! This biannual report, which is a collaboration between...
Cisco Secure Client Software Denial of Service Vulnerability – Source:sec.cloudapps.cisco.com
Source: sec.cloudapps.cisco.com – Author: . Cisco Secure Client Software Denial of Service Vulnerability Medium CVE-2024-20474 CWE-191 Download CSAF Email Summary A vulnerability in Internet Key Exchange...
Cisco Adaptive Security Appliance and Firepower Threat Defense Software TLS Denial of Service Vulnerability – Source:sec.cloudapps.cisco.com
Source: sec.cloudapps.cisco.com – Author: . Cisco Adaptive Security Appliance and Firepower Threat Defense Software TLS Denial of Service Vulnerability High CVE-2024-20494 CWE-1287 Download CSAF Email Summary...
How Do I Protect Myself When Using Wi-Fi? – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. Wi-Fi is everywhere. Whether you travel for business or simply need Internet access while out and about, your options are...
Does Antivirus Software Slow You Down? – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. “Antivirus software slows down my PC.” This is a comment that is often heard when talking about antivirus and malware protection....
How a VPN Can Make Your Time Online More Private and Secure – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. What is a VPN (virtual private network)? And how can it make your time online more secure—and a little more...
The Scam Strikes Back: Exploiting the CrowdStrike Outage – Source:www.mcafee.com
Source: www.mcafee.com – Author: McAfee Labs. Authored by Lakshya Mathur, Vallabh Chole & Abhishek Karnik Recently we witnessed one of the most significant IT disruptions in...
Are Mobile Devices Less Secure than PCs? – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. Are smartphones less secure than PCs? The answer to that is, they’re different. They face different security threats. Yet they...
Olympics Has Fallen – A Misinformation Campaign Featuring a Voice Cloned Elon Musk – Source:www.mcafee.com
Source: www.mcafee.com – Author: McAfee Labs. Authored by Lakshya Mathur and Abhishek Karnik As the world gears up for the 2024 Paris Olympics, excitement is building,...
Does Windows 10 or 11 Need Antivirus Software? – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. Does Windows 10 or 11 need antivirus software? Absolutely. Every computer needs protection against viruses and other malware. The next...
What Does “Connection is Not Private” Mean? – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. Have you ever visited a site that triggers a “your connection is not private” or “your connection is not secure”...
CWE (Common Weakness Enumeration) and the CWE Top 25 Explained – Source:www.hackerone.com
Source: www.hackerone.com – Author: HackerOne. Updated September 1, 2023 Are you wondering about CWE? We explain CWE (Common Weakness Enumeration) and why this community-based initiative is...
Log4j Vulnerability Activity on the HackerOne Platform – Source:www.hackerone.com
Source: www.hackerone.com – Author: HackerOne. This post is about the severe and widespread Log4j vulnerability, known as Log4Shell. It gives a technical overview of the vulnerability,...