Source: www.infosecurity-magazine.com – Author: A growing wave of arbitrage betting fraud, driven by automation and advanced money laundering techniques, has been forcing bookmakers to adopt stricter...
Day: January 24, 2025
The Power of Many: Crowdsourcing as A Game-Changer for Modern Cyber Defense – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team With the rapid technological advancement and the world entering the AI era, the cyber threat landscape has significantly evolved in...
Operational Security: The Backbone of Effective Police Communication – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In the fast-paced and dynamic world of law enforcement, effective communication is essential for ensuring public safety and successful operations....
A K-12 Guide to the Digital Classroom – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alexa Sander Digital tools have transformed how teachers and students engage in classroom activities, creating opportunities to enhance learning, communication, and organization....
Understanding the 3-Layers of Non-Human Identity (NHI) Security in TrustFour’s Posture and Attack Surface Management Framework – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jim Curtin In today’s interconnected digital ecosystems, securing Non-Human Identities (NHIs) has become a critical focus. NHIs—representing machines, applications, containers, and microservices—outnumber...
Safe Secrets Rotation: A Must for Modern Clouds – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why is Secrets Rotation Crucial for Cloud Security? Are you familiar with the concept of secrets rotation? Does it sound...
Boosting Confidence in Cloud-Native Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are You Confident in Your Cloud-Native Security? Navigating cybersecurity can be like walking through a maze filled with lurking threats....
Unlocking Innovation with Protected Machine Identities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Is Your Organization Paying Enough Attention to Non-Human Identities? Organizations extensively utilize cloud services and automated systems. In doing so,...
How to Stop Layer 7 DDoS Attacks in 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andrew Hendry Imagine your website humming with activity, traffic soaring, and your brand capturing the attention it deserves. But what if that...
6 Ways IT Can Help You Modernize Case Management Software – Source: securityboulevard.com
Source: securityboulevard.com – Author: Manish Mehta Article Your IT department can be a valuable ally in overcoming inevitable resistance to change Related Resources Modern and effective...
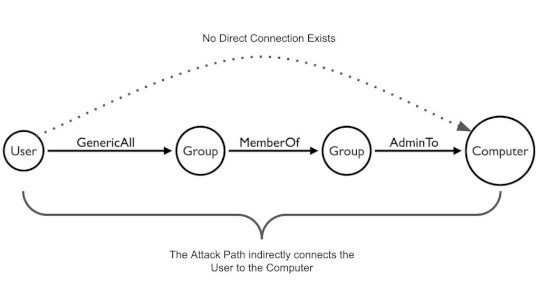
Insurance companies can reduce risk with Attack Path Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kirsten Gibson TL;DR Insurance companies host large amounts of sensitive data (PII, PHI, etc.) and often have complex environments due to M&A...
DEF CON 32 – The Wild And Wonderful World Of Early Microprocessors With A Focus On 6502 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, January 23, 2025 Home » Security Bloggers Network » DEF CON 32 – The Wild And Wonderful World Of...
SOC vs MSSP: Which is Right for Your Business? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rebecca Kappel One of the most pivotal decisions an organization faces is whether to build an in-house Security Operations Center (SOC) or...