Source: www.techrepublic.com – Author: Megan Crouse We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
Day: January 8, 2025
A Day in the Life of a Prolific Voice Phishing Crew – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Besieged by scammers seeking to phish user accounts over the telephone, Apple and Google frequently caution that they will never reach...
US Launches Cyber Trust Mark for IoT Devices – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The US has launched a Cyber Trust Mark for Internet of Things (IoT) devices, enabling consumers to easily assess the cybersecurity standards...
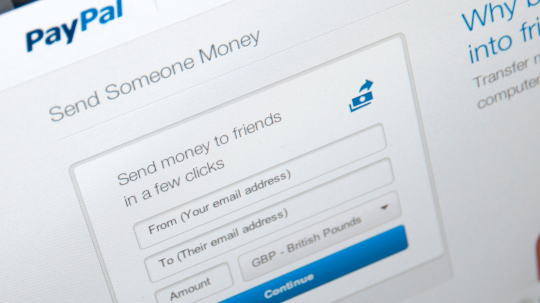
Scammers Exploit Microsoft 365 to Target PayPal Users – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A new phishing technique exploiting PayPal’s money request feature has been identified, using a legitimate PayPal money request that may appear genuine...
Casio Admits Security Failings as Attackers Leak Employee and Customer Data – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Electronics manufacturing giant Casio admitted that security failings resulted in the personal data of employees, customers and business partners have been leaked...
New Mirai Botnet Exploits Zero-Days in Routers and Smart Devices – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Security researchers have uncovered a new Mirai-based botnet that uses zero-day exploits for industrial routers and smart home devices to spread. The...
Fake Government Officials Use Remote Access Tools for Card Fraud – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Security researchers have uncovered a sophisticated, multi-stage fraud campaign designed to trick consumers into sharing their card details. Group-IB revealed that the...
Unconventional Cyberattacks Aim to Take Over PayPal Accounts – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Robert Wilkinson via Alamy Stock Photo An unconventional phishing campaign convincingly impersonates online payments service PayPal to...
Best Practices & Risks Considerations in LCNC and RPA Automation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jordan Bonagura Source: Igor Stevanovic via Alamy Stock Photo COMMENTARY Technologies such as low-code/no-code (LCNC) and robotic process automation (RPA) have become...
Ransomware Targeting Infrastructure Hits Telecom Namibia – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Golden Dayz via Shutterstock The telecommunications provider for the African nation of Namibia suffered a significant ransomware...
1Password Acquires SaaS Access Management Provider Trelica – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz Source: blickwinkel via Alamy Stock Photo NEWS BRIEF 1Password on Monday announced that it has acquired software-as-a-service (SaaS) access management...
Sharing of Telegram User Data Surges After CEO Arrest – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: Piotr Adamowicz via Alamy Stock Photo Before September 2024, policy of encrypted communications provider Telegram...
Telegram Shared Data of Thousands of Users After CEO’s Arrest – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Following the arrest of its CEO last summer, Telegram has been increasingly sharing user data at the request of authorities,...
Japan Links Chinese Hacker MirrorFace to Dozens of Cyberattacks Targeting Security and Tech Data – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Japan on Wednesday linked more than 200 cyberattacks over the past five years targeting the country’s national security and high...
Rationalizing the Stack: The Case for Security Vendor Consolidation – Source: www.securityweek.com
Source: www.securityweek.com – Author: Joshua Goldfarb In recent years, tighter security budgets and macroeconomic headwinds have created a need to optimize security spend. In this fiscal environment,...
Thousands Impacted by Casio Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Japanese electronics giant Casio has completed its investigation into the data breach caused by a recent ransomware attack and found...
Cybersecurity Funding Reached $9.5 Billion in 2024: Report – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Funding raised by cybersecurity firms increased to $9.5 billion last year amid a decrease in funding volume, a new report...
Insider Threat: Tackling the Complex Challenges of the Enemy Within – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The insider threat is a simple term for a mammoth and complex problem. It ranges from national security through theft...
New Labels Will Help People Pick Devices Less at Risk of Hacking – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press The federal government is rolling out a consumer labeling system designed to help Americans pick smart devices that are less...
CISA Warns of Mitel MiCollab Vulnerabilities Exploited in Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US cybersecurity agency CISA on Tuesday warned that two recently disclosed vulnerabilities affecting the Mitel MiCollab enterprise collaboration platform...
News Alert: Security Risk Advisors joins Microsoft Intelligent Security Association (MISA) – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire Philadelphia, Pa., Jan. 7, 2025, CyberNewswire — Security Risk Advisors today announced it has become a member of the Microsoft Intelligent...
News alert: CyTwist launches threat detection engine tuned to identify AI-driven malware in minutes – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire Ramat Gan, Israel, January 7th, 2025, CyberNewswire — CyTwist, a leader in advanced next-generation threat detection solutions, has launched its patented...
AT&T Breach 2024: Customer Data Exposed in Massive Cyber Attack – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In a shocking breach of customer privacy, AT&T said in April 2024 that almost all of the data of its...
The Fundamental Components to Achieving Shift-Left Success – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team “Shift-left” is a familiar concept to CISOs and security practitioners across the globe. A term coined to promote the integration...
The Role of AI in Evolving Cybersecurity Attacks – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In the ever-expanding digital landscape, cybersecurity remains a critical concern for individuals, businesses, and governments alike. As technology advances, so...
A Guide for SMB Defense Contractors to Achieve CMMC Compliance – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team The Department of Defense (DoD) created the Cybersecurity Maturity Model Certification (CMMC) program to defend the vast attack surface of the Defense...
Navigating the Security Risks and Efficiency Gains of GenAI in Healthcare – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team SaaS technology and artificial intelligence (AI) are revolutionizing patient care, drug development, and health and wellness practices. Today, AI processes...
Fight Fire with Fire: 3 Strategies to Defeat Deepfakes – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Generative AI deepfakes represent another skirmish in the ongoing clash between two forces that never stop innovating I was there...
The Common Goods and Shared Threats of the Software Supply Chain – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Perhaps the defining quality of the software supply chain is complexity. Amid the countless lines of code that the modern...
The AI Fix #32: Agentic AI, killer robot fridges, and the robosexual revolution – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content In episode 32 of The AI Fix, our hosts learn the meaning of “poronkusema”, Mark discovers his...