The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Year: 2024
Australian Court Service Hacked, Hearing Recordings at Risk – Source: www.infosecurity-magazine.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Teen Found Alive After “Cyber-Kidnapping” Incident – Source: www.infosecurity-magazine.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Black Basta Ransomware Decryptor Published – Source: www.infosecurity-magazine.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
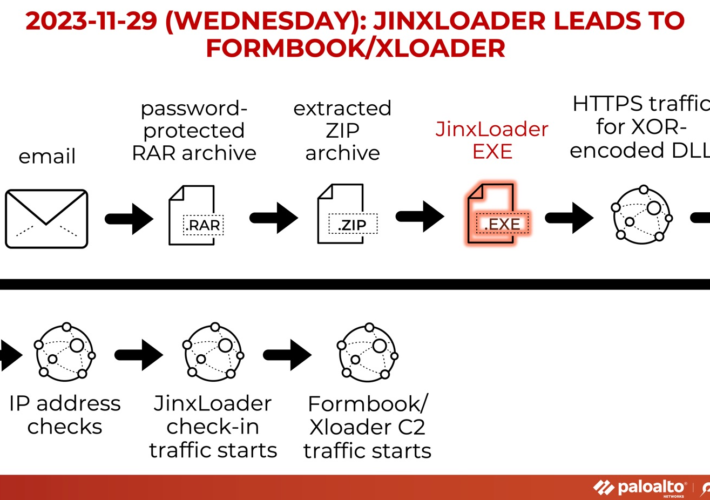
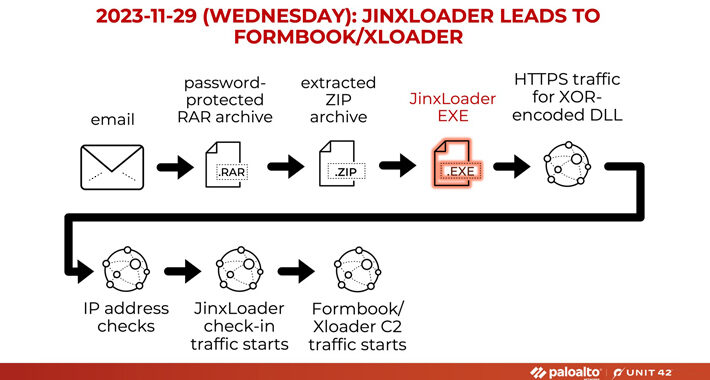
Experts warn of JinxLoader loader used to spread Formbook and XLoader – Source: securityaffairs.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
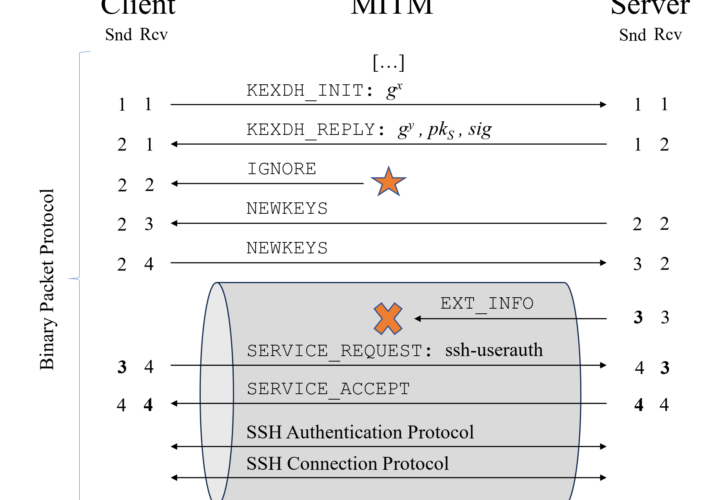
Terrapin attack allows to downgrade SSH protocol security – Source: securityaffairs.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
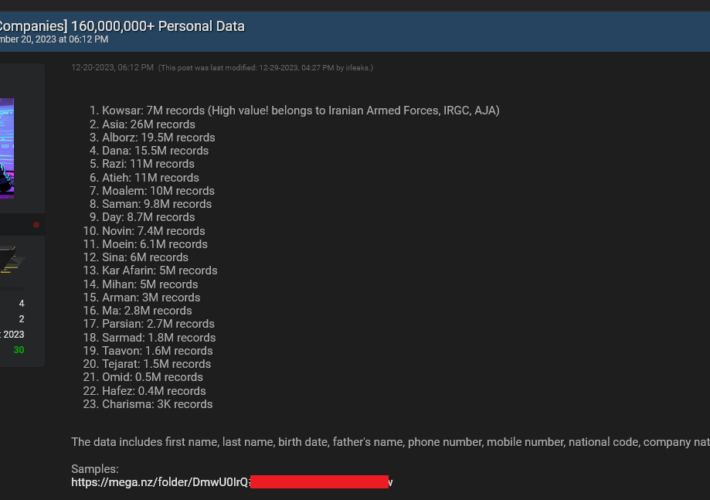
Multiple organizations in Iran were breached by a mysterious hacker – Source: securityaffairs.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Top 2023 Security Affairs cybersecurity stories – Source: securityaffairs.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
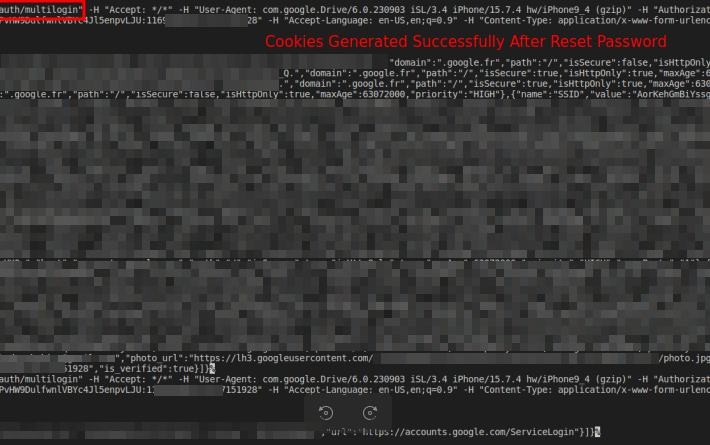
Malware exploits undocumented Google OAuth endpoint to regenerate Google cookies – Source: securityaffairs.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Definitive Enterprise Browser Buyer’s Guide – Source:thehackernews.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Google Settles $5 Billion Privacy Lawsuit Over Tracking Users in ‘Incognito Mode’ – Source:thehackernews.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Welcome To 2024 – Source: securityboulevard.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
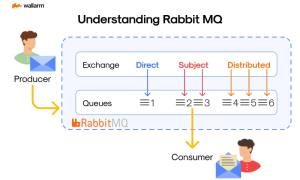
What is RabbitMQ? – Source: securityboulevard.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Benefits of Employing AI in GRC – Source: securityboulevard.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Insights from CISA HPH Sector Risk and Vulnerability Assessment – Source: securityboulevard.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
8 Essential Steps to Recover a Hacked Website – Source: securityboulevard.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Happy New Year 2024 – Source: securityboulevard.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
MS Excel Vulnerability Exploited To Distribute Agent Tesla – Source: securityboulevard.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Three Keys to Success in Cybersecurity – Source: securityboulevard.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity Trends to Watch in 2024 – Source: www.databreachtoday.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
New Variant of DLL Search Order Hijacking Bypasses Windows 10 and 11 Protections – Source:thehackernews.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cactus RANSOMWARE gang hit the Swedish retail and grocery provider Coop – Source: securityaffairs.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Google agreed to settle a $5 billion privacy lawsuit – Source: securityaffairs.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Android game dev’s Google Drive misconfig highlights cloud security risks – Source: www.bleepingcomputer.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
New Terrapin Flaw Could Let Attackers Downgrade SSH Protocol Security – Source:thehackernews.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
New JinxLoader Targeting Users with Formbook and XLoader Malware – Source:thehackernews.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
USENIX Security ’23 – Alexander Bienstock, Sarvar Patel, Joon Young Seo, Kevin Yeo ‘Near-Optimal Oblivious Key-Value Stores For Efficient PSI, PSU And Volume-Hiding Multi-Maps’ – Source: securityboulevard.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Tech Security Year in Review – Source: securityboulevard.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Vietnam’s Massive CAPTCHA crackers vs. Microsoft DCU – Source: securityboulevard.com
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...