Source: www.infosecurity-magazine.com – Author: 1 A surge of fake or stolen X (Twitter) Gold accounts has been flooding marketplaces and forums both on the surface web...
Year: 2024
Russia Spies on Kyiv Defenses via Hacked Cameras Before Missile Strikes – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Russian intelligence hacked online surveillance cameras to spy on air defense activities and critical infrastructure in Kyiv ahead of recent missile...
Xerox Business Solutions Reveals Security Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A subsidiary of imaging giant Xerox has revealed it was struck by a “security incident” at the end of 2023, with...
VoIP Firm XCast Agrees to Settle $10m Illegal Robocall Case – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A Californian VoIP provider has agreed to settle FTC charges that it facilitated hundreds of millions of illegal robocalls made over...
‘Black Basta Buster’ Exploits Ransomware Bug for File Recovery – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Researchers have exploited a weakness in a particular strain of the Black Basta ransomware to release a decryptor...
Name That Edge Toon: Frosty the Steel Man – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Klossner, Cartoonist Dark Reading is part of the Informa Tech Division of Informa PLC This site is operated by a business...
Qatar to Add Cybersecurity Curricula in Private Schools – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Olekcii Mach via Alamy Stock Photo Qatar’s National Cyber Security Agency (NCSA) plans to roll out a cybersecurity...
5 Steps for Preventing and Mitigating Corporate Espionage – Source: www.darkreading.com
Source: www.darkreading.com – Author: Evan Gibbs, Will Taylor Source: Andrii Yalanskyi via Alamy Stock Photo COMMENTARY There has been a steady increase in the volume of...
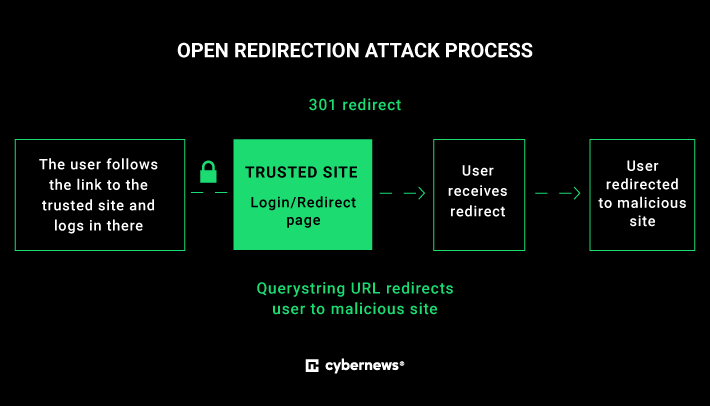
Don’t trust links with known domains: BMW affected by redirect vulnerability – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Don’t trust links with known domains: BMW affected by redirect vulnerability Sometimes, you can’t even trust links with your own...
Hackers stole more than $81 million worth of crypto assets from Orbit Chain – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Hackers stole more than $81 million worth of crypto assets from Orbit Chain Crypto platform Orbit Chain suffered a cyberattack,...
Ukraine’s SBU said that Russia’s intelligence hacked surveillance cameras to direct a missile strike on Kyiv – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Ukraine’s SBU said that Russia’s intelligence hacked surveillance cameras to direct a missile strike on Kyiv Ukraine’s SBU revealed that Russia-linked...
Researchers released a free decryptor for Black Basta ransomware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers released a free decryptor for Black Basta ransomware A team of researchers released a suite of tools that could...
5 Ways to Reduce SaaS Security Risks – Source:thehackernews.com
Source: thehackernews.com – Author: . As technology adoption has shifted to be employee-led, just in time, and from any location or device, IT and security teams...
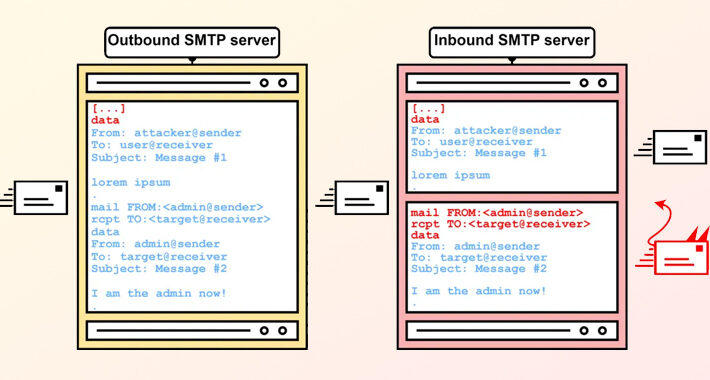
SMTP Smuggling: New Flaw Lets Attackers Bypass Security and Spoof Emails – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 03, 2024NewsroomCyber Threat / Email Security A new exploitation technique called Simple Mail Transfer Protocol (SMTP) smuggling can be weaponized...
DOJ Slams XCast with $10 Million Fine Over Massive Illegal Robocall Operation – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 03, 2024NewsroomVoIP Service / Regulatory Compliance The U.S. Department of Justice (DoJ) on Tuesday said it reached a settlement with...
States and Congress Wrestle With Cybersecurity After Iran Attacks Small Town Water Utilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press The hacking of a municipal water plant is prompting new warnings from U.S. security officials at a time when governments...
Are Security Appliances fit for Purpose in a Decentralized Workplace? – Source: www.securityweek.com
Source: www.securityweek.com – Author: Etay Maor Security appliances are amongst the most riskiest enterprise devices and are a often method for threat actors to infiltrate a...
Free Decryptor Released for Black Basta Ransomware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A vulnerability in Black Basta ransomware’s encryption algorithm allows researchers to create a free decryptor. The post Free Decryptor Released...
New DLL Search Order Hijacking Technique Targets WinSxS Folder – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Attackers can abuse a new DLL search order hijacking technique to execute code in applications within the WinSxS folder. The...
Steam drops support for Windows 7 and 8.1 to boost security – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Steam is no longer supported on Windows 7, Windows 8, and Windows 8.1 as of January 1, with the company...
Orbit Chain loses $86 million in the last fintech hack of 2023 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Orbit Chain has experienced a security breach that has resulted in a loss of $86 million in cryptocurrency, particularly Ether,...
Online museum collections down after cyberattack on service provider – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Museum software solutions provider Gallery Systems has disclosed that its ongoing IT outages were caused by a ransomware attack last...
Xerox says subsidiary XBS U.S. breached after ransomware gang leaks data – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The U.S. division of Xerox Business Solutions (XBS) has been compromised by hackers with a limited amount of personal information...
Google Groups is ending support for Usenet to combat spam – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Google has officially announced it’s ceasing support for Usenet groups on its Google Groups platform, a move partly attributed to...
Victoria court recordings exposed in reported ransomware attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Australia’s Court Services Victoria (CSV) is warning that video recordings of court hearings were exposed after suffering a reported Qilin...
The law enforcement operations targeting cybercrime in 2023 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams In 2023, we saw numerous law enforcement operations targeting cybercrime operations, including cryptocurrency scams, phishing attacks, credential theft, malware development,...
The biggest cybersecurity and cyberattack stories of 2023 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams 2023 was a big year for cybersecurity, with significant cyberattacks, data breaches, new threat groups emerging, and, of course, zero-day...
TikTok Editorial Analysis – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier TikTok seems to be skewing things in the interests of the Chinese Communist Party. (This is a serious analysis, and...
New SEC Cybersecurity Reporting Rules Take Effect – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tova Osofsky In July 2023 the US Security and Exchange Commission (SEC) issued new rules on “Cybersecurity Risk Management, Strategy, Governance, and...
USENIX Security ’23 – Cong Zhang, Yu Chen, Weiran Liu, Min Zhang, Dongdai Lin – ‘Linear Private Set Union From Multi-Query Reverse Private Membership Test’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...