Source: www.infosecurity-magazine.com – Author: 1 Court cases and tribunals in Australia have been impacted by a cybersecurity incident, with attackers potentially accessing recordings of hearings, according...
Year: 2024
Teen Found Alive After “Cyber-Kidnapping” Incident – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A Chinese foreign exchange student has been found alive and well by Utah police after being caught up in what authorities...
Black Basta Ransomware Decryptor Published – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have published a new suite of tools designed to help victims of the prolific Black Basta ransomware recover their...
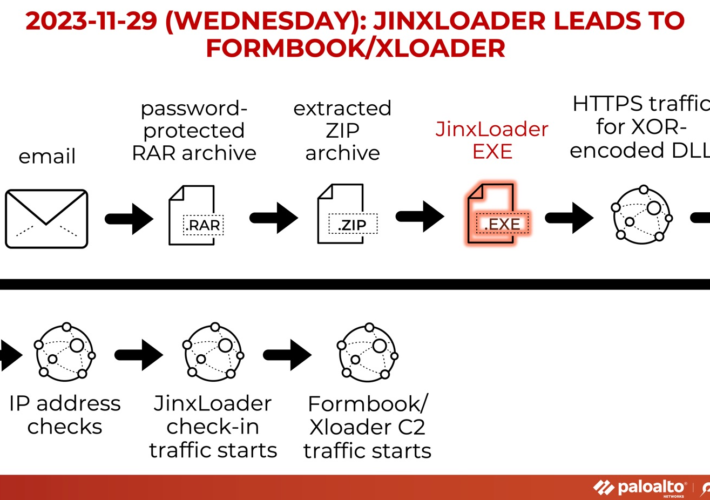
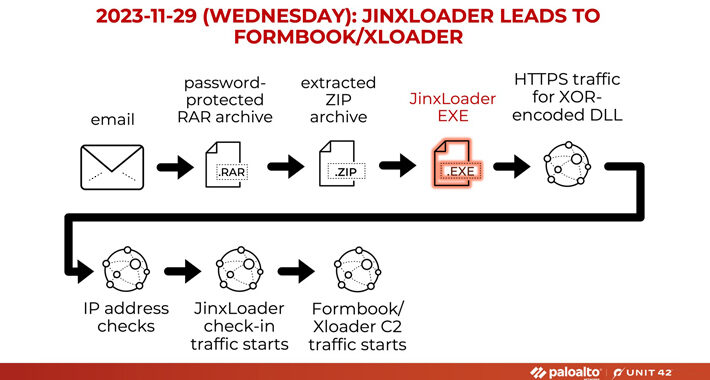
Experts warn of JinxLoader loader used to spread Formbook and XLoader – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn of JinxLoader loader used to spread Formbook and XLoader JinxLoader is a new Go-based loader that was spotted...
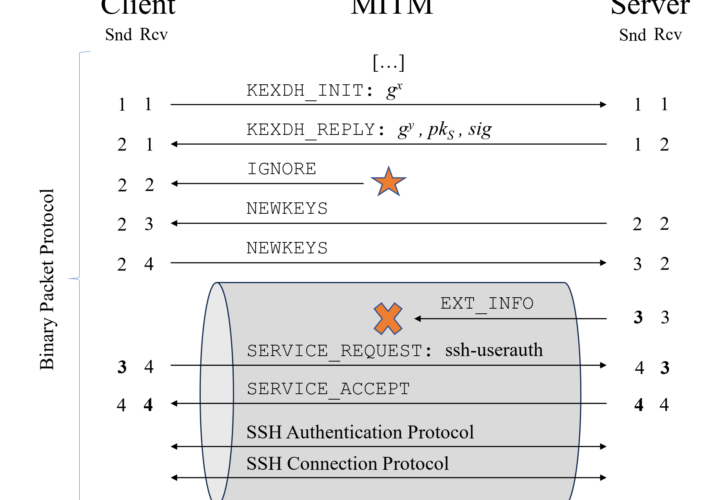
Terrapin attack allows to downgrade SSH protocol security – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Terrapin attack allows to downgrade SSH protocol security Researchers discovered an SSH vulnerability, called Terrapin, that could allow an attacker...
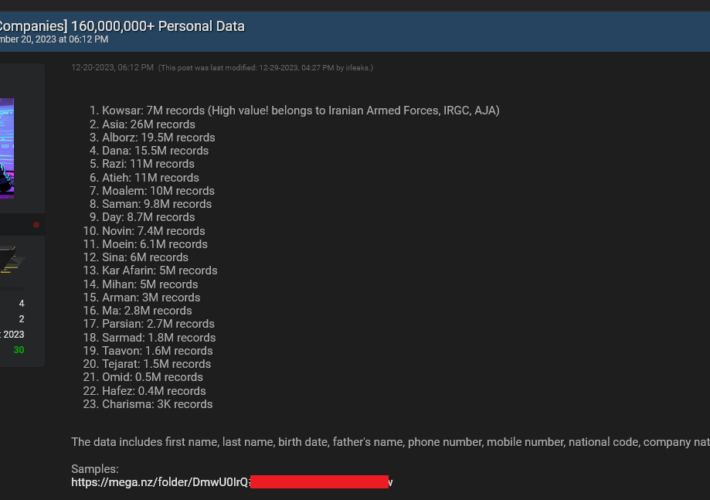
Multiple organizations in Iran were breached by a mysterious hacker – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Multiple organizations in Iran were breached by a mysterious hacker Hudson Researchers reported that a mysterious hacker launched a series...
Top 2023 Security Affairs cybersecurity stories – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Top 2023 Security Affairs cybersecurity stories These are the Top 2023 Security Affairs cybersecurity stories … enjoy it. CYBERCRIMINALS LAUNCHED...
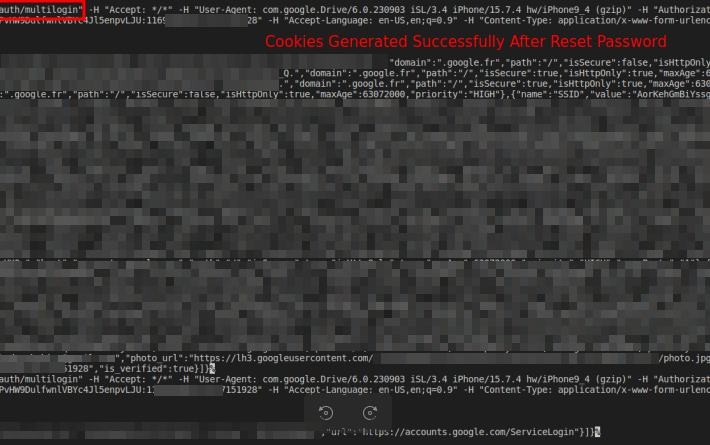
Malware exploits undocumented Google OAuth endpoint to regenerate Google cookies – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Malware exploits undocumented Google OAuth endpoint to regenerate Google cookies CloudSEK researchers analyzed a zero-day exploit that can allow the...
The Definitive Enterprise Browser Buyer’s Guide – Source:thehackernews.com
Source: thehackernews.com – Author: . Security stakeholders have come to realize that the prominent role the browser has in the modern corporate environment requires a re-evaluation...
Google Settles $5 Billion Privacy Lawsuit Over Tracking Users in ‘Incognito Mode’ – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 02, 2024NewsroomData Privacy / Online Tracking Google has agreed to settle a lawsuit filed in June 2020 that alleged that...
Welcome To 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: hrbrmstr Hey folks, This is likely our last shot at preserving liberal democracy in the U.S., or at least avoiding 20–40 years...
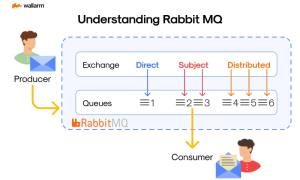
What is RabbitMQ? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ivan Novikov Grasping the Basics: What is RabbitMQ? Take a step into the realm of software development, where efficient and smooth interaction...
The Benefits of Employing AI in GRC – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michelle Ofir Geveye The narrative of technology surpassing human intelligence and altering the course of humanity is a recurring theme in science...
Insights from CISA HPH Sector Risk and Vulnerability Assessment – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rohan Timalsina In an ever-evolving digital landscape, the healthcare and public health (HPH) sector faces increasing cybersecurity challenges. The United States Cybersecurity...
8 Essential Steps to Recover a Hacked Website – Source: securityboulevard.com
Source: securityboulevard.com – Author: TuxCare Team When you find out your website is hacked, it’s understandable that you’d begin to panic. But it’s much better to...
Happy New Year 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
MS Excel Vulnerability Exploited To Distribute Agent Tesla – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wajahat Raja Threat actors with malicious intent have now been exploiting an old MS Excel vulnerability as part of their phishing campaign....
The Three Keys to Success in Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tom Eston In this episode, host Tom Eston shares the three key lessons he’s learned over his 18-year career in cybersecurity: effective...
Cybersecurity Trends to Watch in 2024 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , AI-Based Attacks , API Security Expert Panelists Debate Impact of AI, Geopolitics and New Tactics in...
New Variant of DLL Search Order Hijacking Bypasses Windows 10 and 11 Protections – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 01, 2024NewsroomWindows Security / Vulnerability Security researchers have detailed a new variant of a dynamic link library (DLL) search order...
Cactus RANSOMWARE gang hit the Swedish retail and grocery provider Coop – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cactus RANSOMWARE gang hit the Swedish retail and grocery provider Coop The Cactus ransomware group claims to have hacked Coop,...
Google agreed to settle a $5 billion privacy lawsuit – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Google agreed to settle a $5 billion privacy lawsuit Pierluigi Paganini December 31, 2023 Google has agreed to settle a...
Android game dev’s Google Drive misconfig highlights cloud security risks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Japanese game developer Ateam has proven that a simple Google Drive configuration mistake can result in the potential but unlikely...
New Terrapin Flaw Could Let Attackers Downgrade SSH Protocol Security – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 01, 2024NewsroomEncryption / Network Security Security researchers from Ruhr University Bochum have discovered a vulnerability in the Secure Shell (SSH)...
New JinxLoader Targeting Users with Formbook and XLoader Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 01, 2024NewsroomMalware / Dark Web A new Go-based malware loader called JinxLoader is being used by threat actors to deliver...
USENIX Security ’23 – Alexander Bienstock, Sarvar Patel, Joon Young Seo, Kevin Yeo ‘Near-Optimal Oblivious Key-Value Stores For Efficient PSI, PSU And Volume-Hiding Multi-Maps’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
Tech Security Year in Review – Source: securityboulevard.com
Source: securityboulevard.com – Author: Emma Kelly As we say goodbye to 2023, let’s look back on a year that has become a battleground in cybersecurity. The...
Vietnam’s Massive CAPTCHA crackers vs. Microsoft DCU – Source: securityboulevard.com
Source: securityboulevard.com – Author: Gary Warner Earlier this month, Microsoft’s Digital Crimes Unit was featured in a WIRED article by Lily Hay Newman – Microsoft’s Digital Crime...