Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Artemis Diana via Alamy Passkeys gained momentum in 2023. In addition to the major three technology firms...
Year: 2024
Russian Agents Hack Webcams to Guide Missile Attacks on Kyiv – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: 99Art via Shutterstock The Security Service of Ukraine (SSU) has asked owners and operators of webcams in...
SonicWall Accelerates SASE Offerings; Acquires Proven Cloud Security Provider – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE MILPITAS, Calif. — January 3, 2024 — SonicWall, a global cybersecurity leader, today announced the acquisition of Banyan Security, a leading...
Ransomware Group Claims Cyber Breach of Xerox Subsidiary – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Michael Ventura via Alamy Stock Photo Xerox Business Solutions, a subsidiary of Xerox, experienced a “cyber security incident,”...
SentinelOne to Expand Cloud Security Capabilities With Acquisition of PingSafe – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE MOUNTAIN VIEW, CA – January 3, 2024 – SentinelOne (NYSE: S), a global leader in AI-powered security, today announced that it has...
iFlock Security Consulting Secures Private Funding – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE WAKARUSA, Ind., Jan. 3, 2024 /PRNewswire/ — iFlock Security Consulting, a leading boutique cybersecurity company specializing in penetration testing and ancillary services,...
Cybercriminals Flood Dark Web With X (Twitter) Gold Accounts – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: Pixel-shot via Alamy Stock Photo Cybercriminals are taking over verified “Gold” accounts on X,...
Courts service “PWNED” in Australia, as hackers steal sensitive recordings of hearings – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Hackers are believed to have successfully accessed several weeks’ worth of sensitive video and audio recordings of court hearings, including...
LastPass Hikes Password Requirements to 12 Characters – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading 2 Min Read Source: SOPA Images Limited via Alamy Stock Photo Password-manager purveyor LastPass has announced it’s...
Pilfered Data From Iranian Insurance and Food Delivery Firms Leaked Online – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Leyden Source: Hakan Gider via Alamy Stock Photo Cybercriminals broke into the systems of 23 leading Iranian insurance firms and SnappFood,...
Beware: 3 Malicious PyPI Packages Found Targeting Linux with Crypto Miners – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 04, 2024NewsroomCryptocurrency Miner / Malware Three new malicious packages have been discovered in the Python Package Index (PyPI) open-source repository...
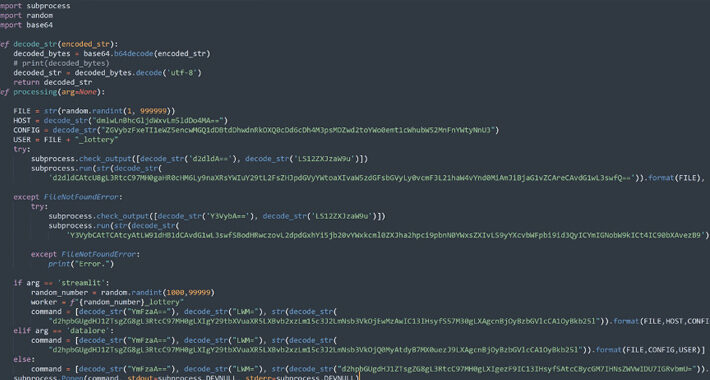
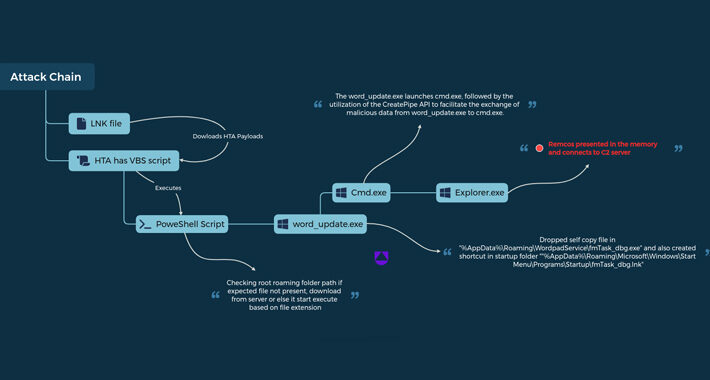
UAC-0050 Group Using New Phishing Tactics to Distribute Remcos RAT – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 04, 2024NewsroomSoftware Security / Malware The threat actor known as UAC-0050 is leveraging phishing attacks to distribute Remcos RAT using...
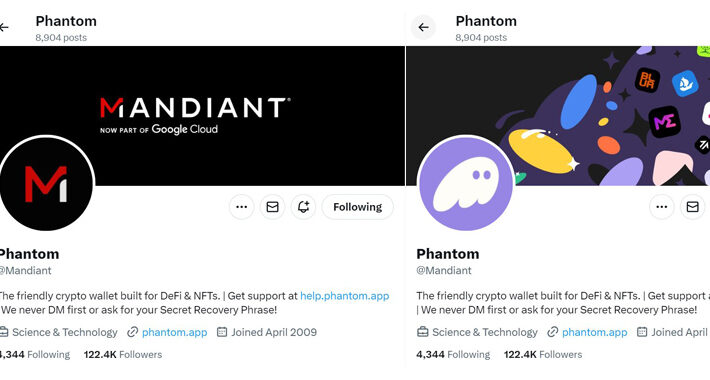
Mandiant’s Twitter Account Restored After Six-Hour Crypto Scam Hack – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 04, 2024NewsroomCryptocurrency / Social Media American cybersecurity firm and Google Cloud subsidiary Mandiant had its X (formerly Twitter) account compromised...
Facial Recognition Systems in the US – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier A helpful summary of which US retail stores are using facial recognition, thinking about using it, or currently not planning...
Live Webinar | Dancing with Shadows: Vendor Risk Management in the Age of AI and Cyber Intrigue – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Nate Smolenski Head of Cyber Intelligence Strategy, Netskope Nate Smolenski is an experienced CISO, Advisor, and technology leader with over two...
Aqua Security Scores $60M Series E Funding – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Late-stage player in the CNAPP space secures a $60 million extended Series E funding round at a valuation north of...
SentinelOne Snaps up Seed-Stage CNAPP Startup PingSafe – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine SentinelOne plans to acquire PingSafe in a cash-and-stock deal that adds cloud native application protection platform (CNAPP) technologies. The post...
SonicWall Buys Banyan Security For ZTNA Technology – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine SonicWall announces the acquisition of Banyan Security, a deal that adds zero-trust network access tooling to its product portfolio. The...
Over 900k Impacted by Data Breach at Defunct Boston Ambulance Service – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The personal information of more than 900,000 individuals was stolen in a data breach at Fallon Ambulance Service. The post...
Several Infostealers Using Persistent Cookies to Hijack Google Accounts – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A vulnerability in Google’s authentication process allows malware to restore cookies and hijack user sessions. The post Several Infostealers Using...
Hacker Conversations: Runa Sandvik – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend SecurityWeek interviews Runa Sandvik, a cybersecurity researcher focused on protecting journalists, defenders of human rights and lawyers, The post Hacker...
Uncertainty Is the Biggest Challenge to Australia’s Cyber Security Strategy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Matthew Sainsbury Just the highlights Australia’s cyber security vision extends to 2030, with two federal elections occurring in that time frame. A...
Cybersecurity M&A Roundup: 25 Deals Announced in December 2023 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Twenty-five cybersecurity-related merger and acquisition (M&A) deals were announced in December 2023. The post Cybersecurity M&A Roundup: 25 Deals Announced...
Palestinian Hackers Hit 100 Israeli Organizations in Destructive Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A group of claimed Palestinian state cyber warriors has hit over 100 Israeli organizations with wipers and data theft. The...
21 New Mac Malware Families Emerged in 2023 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A total of 21 new malware families targeting macOS systems were discovered in 2023, a 50% increase compared to 2022. ...
Xerox Confirms Data Breach at US Subsidiary Following Ransomware Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Xerox says personal information was stolen in a cyberattack at US subsidiary Xerox Business Solutions. The post Xerox Confirms Data...
Massive Fallon Ambulance Data Breach Impacts Nearly One Million People – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Transformative Healthcare announces Fallon Ambulance data breach exposed sensitive information of 911,757 customers. Fallon ceased operations in December 2022 but...
Democracy 2024: Stakes vs. Horses – Source: securityboulevard.com
Source: securityboulevard.com – Author: hrbrmstr The 2024 U.S. Presidential election isn’t just another tick on the political timeline. It’s a crucial juncture for — quite literally...
Top 3 SEC Cyber Rule Misconceptions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joe Breen Cloud Security, Governance and Skills in 2024 Step 1 of 6 16% Who in your organization is responsible for cloud...
The state of container security: 5 key steps to locking down your releases – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jai Vijayan Container technologies are rapidly transforming application development and deployment practices at many organizations. But they also present a minefield of...