Source: www.schneier.com – Author: Bruce Schneier This is an old piece of malware—the Chameleon Android banking Trojan—that now disables biometric authentication in order to steal the...
Year: 2024
Midwives clinic takes nine months to deliver news of data breach – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley CBC News in Canada is reporting that clients of a pregnancy care clinic in Ontario have had their personal information...
Sexual assault in the metaverse investigated by British police – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley The Daily Mail reports on what may be the first time UK police have investigated a sexual assault in cyberspace:...
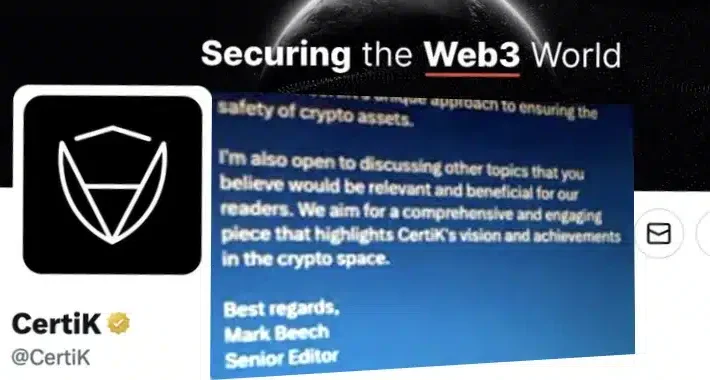
CertiK Twitter account hijacked by cryptocurrency scammer posing as Forbes journalist – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Web3 security outfit CertiK has fallen foul of scammers, who managed to hijack its Twitter account to share a malicious...
Cybersecurity firm Mandiant has its Twitter account hacked to promote cryptocurrency scam – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Google-owned cybersecurity company Mandiant has found itself in the awkward position of having to wrestle back control of its Twitter...
2023 NSA CYBERSECURITY Year In Review
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Data Confidentiality: Identifying and Protecting Assets Against Data Breaches
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
NIST CSF 2.0
Draft & Implementation Examples The NIST Cybersecurity Framework is a technical guide for organisations to improve their cybersecurity. It outlines steps to govern, identify, protect, detect,...
NETWORK PENETRATION TESTING
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
NCSC Cyber Security Framework
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
National Computer Security Day
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Microsoft Office and Windows HTML Remote Code Execution
Looking at the reason that triggers the Alert, it has been found out that the system is trying to exploit the CVE-2023-36884 vulnerability which is a...
Microsoft Cybersecurity Reference Architectures
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Microsoft AzureWell – Architected Framework -Security Pillar
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
BUENAS PRÁCTICAS – Medidas de ciberseguridad en vacaciones
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
DEEP LATERAL MOVEMENT IN OT NETWORKS: When Is a Perimeter Not a Perimeter?
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Information Security Management System Gap Analysis Checklist
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
10 Ways to Detect a Phishing Email
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Mastering Impact with Sharpening Techniques (RTC0026)
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
5ghoul
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Bangladesh Election App Crashes Amid Suspected Cyberattack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: sleepyfellow via Alamy Stock Photo Ukraine and Germany have been accused of waging a cyberattack to crash an...
Beware Weaponized YouTube Channels Spreading Lumma Stealer – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Linaiimages via Shutterstock Attackers have been spreading a variant of the Lumma Stealer via YouTube channels that...
It’s Time to Close the Curtain on Security Theater – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jason Rebholz Source: Brownstock via Alamy Stock Photo COMMENTARY Another day, another ransomware attack or security breach at a brand-name company. And that’s just...
TitanHQ Launches PhishTitan to Combat Advanced Phishing Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE GALWAY, Ireland & SHELTON, Conn., Jan. 09, 2024 (NEWSWIRE) — TitanHQ, the leading cloud-based email security solutions provider for over...
Chertoff Group Affiliate Completes Trustwave Acquisition – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Srabin via iStock MC2 Security Fund, a growth equity fund and affiliate of The Chertoff Group, has completed...
Executing Zero Trust in the Cloud Takes Strategy – Source: www.darkreading.com
Source: www.darkreading.com – Author: Glen Pendley Source: ArtemisDiana via Alamy Stock Photo Zero trust is a high-level strategy that assumes that individuals, devices, and services attempting...
Award Winning Antivirus, On Sale for $25, Offers Elite Protection from Malware – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published January 9, 2024 Updated January 8, 2024 We may earn from vendors via affiliate links or sponsorships. This might...
The best Windows 11 features added in 2023 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar The year 2023 marks a significant milestone for Windows 11 with the introduction of several new features and improvements. This...
Toronto Zoo: Ransomware attack had no impact on animal wellbeing – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Toronto Zoo, the largest zoo in Canada, says that a ransomware attack that hit its systems on early Friday had...
Netgear, Hyundai latest X accounts hacked to push crypto drainers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The official Netgear and Hyundai MEA Twitter/X accounts (together with over 160,000 followers) are the latest hijacked to push scams...