Source: thehackernews.com – Author: . Each New Year introduces a new set of challenges and opportunities for strengthening our cybersecurity posture. It’s the nature of the...
Year: 2024
Italian Data Protection Watchdog Accuses ChatGPT of Privacy Violations – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 30, 2024NewsroomGenerative AI / Data Privacy Italy’s data protection authority (DPA) has notified ChatGPT-maker OpenAI of supposedly violating privacy laws...
New ZLoader Malware Variant Surfaces with 64-bit Windows Compatibility – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 30, 2024NewsroomMalware / Cyber Threat Threat hunters have identified a new campaign that delivers the ZLoader malware, resurfacing nearly two...
Juniper Networks Releases Urgent Junos OS Updates for High-Severity Flaws – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 30, 2024NewsroomVulnerability / Network Security Juniper Networks has released out-of-band updates to address high-severity flaws in SRX Series and EX...
45k Jenkins servers exposed to RCE attacks using public exploits – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Researchers found roughly 45,000 Jenkins instances exposed online that are vulnerable to CVE-2023-23897, a critical remote code execution (RCE) flaw...
Energy giant Schneider Electric hit by Cactus ransomware attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Energy management and automation giant Schneider Electric suffered a Cactus ransomware attack leading to the theft of corporate data, according...
Microsoft says Outlook apps can’t connect to Outlook.com – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft is investigating an issue that prevents Outlook and other email clients from connecting when using an Outlook.com account. “Since...
FBI: Tech support scams now use couriers to collect victims’ money – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Today, the FBI warned about courier services being used to collect money and valuables from victims of tech support and...
Ransomware payments drop to record low as victims refuse to pay – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The number of ransomware victims paying ransom demands has dropped to a record low of 29% in the final quarter...
DHS employees jailed for stealing data of 200K U.S. govt workers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Three former Department of Homeland Security (DHS) employees were sentenced to prison for stealing proprietary U.S. government software and databases...
Microsoft Teams hit by second outage in three days – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft is investigating a second outage affecting Microsoft Teams users across North and South America in the last three days....
Microsoft Executives Hacked – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Microsoft is reporting that a Russian intelligence agency—the same one responsible for SolarWinds—accessed the email system of the company’s executives....
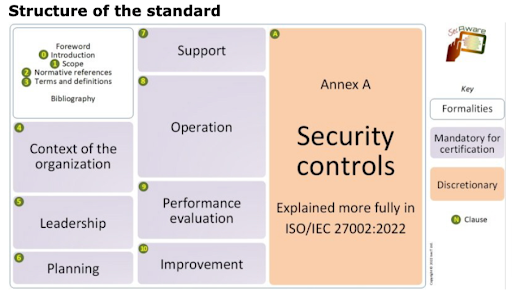
An In-Depth Guide to the 11 New ISO 27001 Controls – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nitzan Gursky From the crudest low-effort phishing attempts to the most sophisticated high-tech hacks, the hits never stop coming. An effective defense...
Control D Launches Control D for Organizations: Democratizing Cybersecurity for Organizations of All Sizes – Source: securityboulevard.com
Source: securityboulevard.com – Author: cyberwire Toronto, Canada, January 29th, 2024, Cyberwire In an era where online threats no longer discriminate by business size, Control D, powered...
Datadog Report Surfaces Pair of Sophisticated AWS Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard A report published by Datadog suggests that cybercriminal activity aimed specifically at cloud infrastructure services provided by Amazon Web Services...
Public Trust Certificates: A 2023 Recap and Projections for 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Morton Looking Back at 2023 2023 was a year of change for Public Trust Certificates – discussions on reduced validity periods,...
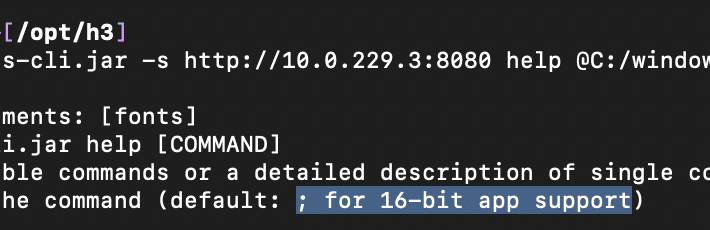
CVE-2024-23897: Assessing the Impact of the Jenkins Arbitrary File Leak Vulnerability – Source: securityboulevard.com
Source: securityboulevard.com – Author: Naveen Sunkavally Last Wednesday, on January 24, 2024, the Jenkins team issued a security advisory disclosing a critical vulnerability, CVE-2024-23897, affecting the...
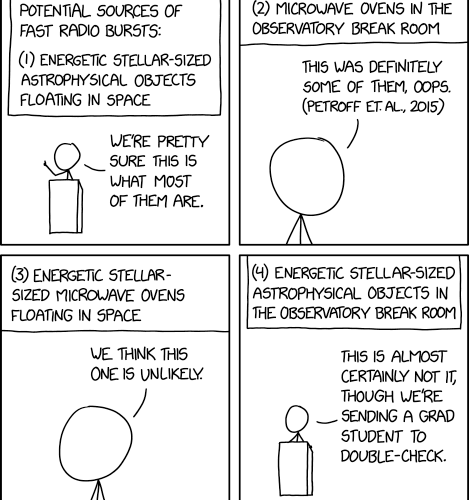
Randall Munroe’s XKCD ‘Fast Radio Bursts’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
USENIX Security ’23 – Rishabh Khandelwal, Asmit Nayak, Hamza Harkous, Kassem Fawaz – Automated Cookie Notice Analysis and Enforcement – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Rishabh Khandelwal, Asmit Nayak, Hamza Harkous, Kassem...
Protecting Business from the Inside Out: A Layered Approach to Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author In the ever-evolving world of cyber threats, protecting a business is akin to fortifying a...
Decoding the Maze: A Guide to Cyber Security Risk Assessment Models – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cameron Delfin In today’s digital age, organizations face the constant threat of cyber attacks. Safeguarding critical data and infrastructure requires a proactive...
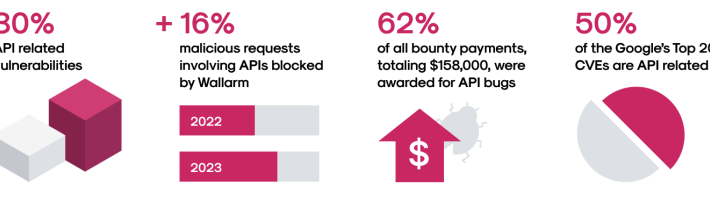
Introducing the Wallarm 2024 API ThreatStatsTM Report – Source: securityboulevard.com
Source: securityboulevard.com – Author: girishwallarm The Wallarm Security Research team is pleased to share the latest version of our API ThreatStats report. This report serves as...
Cybersecurity Incident Shuts Down New Jersey Schools – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime Thousands of Students Forced to Stay Home Amid Cybersecurity Incident Chris Riotta (@chrisriotta) • January...
Insurance Broker Notifying 1.5 Million of Health Info Hack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Healthcare , Incident & Breach Response , Industry Specific California Firm Said August Attack Affected Clients’ Data Marianne Kolbasuk McGee (HealthInfoSec)...
Securing Your Workforce with Datto RMM: Automating Patching, Hardening, and Backups – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
How An Ex-IRS Contractor Covertly Leaked Trump’s Tax Returns – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime Prosecutors Say Charles Littlejohn Developed ‘Detailed Plan’ to Evade Detection Chris Riotta (@chrisriotta) • January...
Italian Regulator Again Finds Privacy Problems in OpenAI – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development ChatGPT Maker Has 30 Days to Respond Akshaya Asokan (asokan_akshaya)...
Keenan & Associates Reports Data Breach Exposing Social Security Numbers of More Than 1.5M – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE MARLTON, N.J., Jan. 29, 2024 /PRNewswire/ — Approximately 1.5 million consumers are being notified that their Social Security numbers and other confidential information were compromised...
PoC Exploits Heighten Risks Around Critical New Jenkins Vuln – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: TippaPatt via Shutterstock Some 45,000 Internet-exposed Jenkins servers remain unpatched against a critical, recently disclosed arbitrary file-read...
SolarWinds Files Motion to Dismiss SEC Lawsuit – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading 2 Min Read Source: Maurice Norbert via Alamy Stock Photo In a new filing with the US...