Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: imageBROKER via Alamy Stock Photo Ivanti has finally begun patching a pair of zero-day...
Year: 2024
Looted RIPE Credentials for Sale on the Dark Web – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alicia Buller, Contributing Writer Source: Brian Jackson via Alamy Stock Photo Hundreds of network operator credentials stolen via compromised RIPE accounts were...
Dubai Cyber Force Names First Accredited Companies – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Andriy Popov via Alamy Stock Photo Eight companies have become the first accredited cybersecurity service providers to be...
AppOmni Harnesses Google Data Center in Australia to Address Regional Demand for Specialised SaaS Security Solutions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tamara Bailey, Content Marketing Specialist @ AppOmni San Francisco, CA – [January 31, 2024] – AppOmni, the pioneer of SaaS security posture...
News alert: Reken raises $10M from Greycroft to protect against generative AI-enabled fraud – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido San Francisco, Calif., Jan. 31, 2024 – Reken, an AI & cybersecurity company, today announced the close of its $10M oversubscribed...
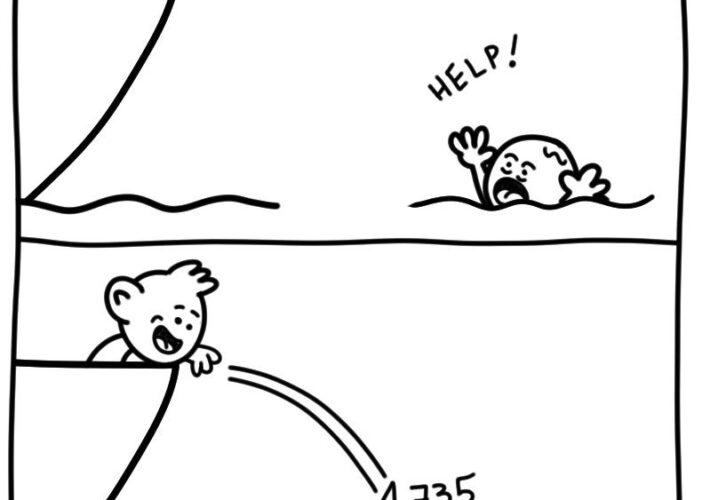
Daniel Stori’s ‘Help’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the webcomic talent of the inimitable Daniel Stori at Turnoff.US. Permalink *** This is a Security Bloggers Network syndicated...
Russian Internet Outage: DNSSEC Oops or Ukraine Hack? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Government ministry denies hackers hacked its network infrastructure. The Russian internet was down for hours yesterday: Everything under the .ru and...
Tax Season is Upon Us, and So Are the Scammers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt It’s still relatively early in the year, but bad actors are already targeting accounting and finance organizations as well as...
Guardians of IoT: Addressing IoT security vulnerabilities in electric vehicles and charging stations – Source: securityboulevard.com
Source: securityboulevard.com – Author: The Coalfire Blog The surge in electric vehicles (EVs) and expanding EV charging infrastructure represents a significant stride toward sustainable and environmentally...
Supply Chain Security and NIS2: What You Need to Know – Source: securityboulevard.com
Source: securityboulevard.com – Author: Flare The Network Information Systems Directive (NIS2) and its predecessor NIS focus on risk management for organizations. The EU states that the...
7 types of food delivery scams and how to stop them – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sift Trust and Safety Team Business is booming for online food delivery services and apps, meal kit providers, and grocery options. The...
USENIX Security ’23 – Black-box Adversarial Example Attack Towards FCG Based Android Malware Detection Under Incomplete Feature Information – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Author/Presenters: Heng Li, Zhang Cheng, Bang Wu, Liheng Yuan, Cuiying Gao, Wei Yuan, Xiapu Luo Many thanks to USENIX for...
A Recap of Cybersecurity in 2023 and What’s Ahead for 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Ratner With high-profile breaches in the news across the world and increasingly sophisticated threats, cybersecurity professionals face more challenges than ever...
Water Sector Leaders Urge Congress to Fund Cyber Mandates – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security The Water and Wastewater Sector Faces Growing Cybersecurity Risks, Officials Warn Chris Riotta (@chrisriotta) • January 31, 2024...
Top Tips to Avoid Corporate Social Media Account Hijacking – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Social Media Not a Good Look: Hijacked @SECgov Social Media Account Spews Bitcoin Rumors Mathew J....
Pushing the Healthcare Sector to Improve Cybersecurity – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Getting the health sector to vastly improve the state of its cybersecurity will take much more than the recent issuance of...
Protecting Your Cloud Assets with CIS Benchmarks & CIS Controls – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Ivanti Discloses Additional Zero-Day That Is Being Exploited – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Governance & Risk Management Company Starts Patch Rollout for Flaws Exploited...
Webinar | Navigating the Perils and the Promise of AI – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Sandra Joyce VP, Mandiant Intelligence Sandra Joyce is a cybersecurity leader, leading Mandiant Intelligence since 2017. She oversees threat research activities...
Proof of Concept: How Do We Ensure Ethical AI Systems? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 AI-Based Attacks , Artificial Intelligence & Machine Learning , Fraud Management & Cybercrime Also: Safeguarding AI Vulnerabilities From Cyber Adversaries Anna...
Here’s How the FBI Stopped a Major Chinese Hacking Campaign – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security FBI and CISA Detail Operation to Prevent China’s Attacks on Critical Infrastructure Chris Riotta (@chrisriotta) • January 31,...
Pawn Storm’s Stealthy Net-NTLMv2 Assault Revealed – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Pawn Storm, an advanced persistent threat (APT) actor also known as APT28, has been targeting high-value entities globally, employing a range...
EU Launches First Cybersecurity Certification for Digital Products – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The EU has adopted its first Cybersecurity Certification scheme as part of efforts to boost cybersecurity of IT products and services...
US Senators Propose Cybersecurity Agriculture Bill – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A new bipartisan bill proposed by two US Senators looks to bolster the cybersecurity of the food and agriculture sector. If...
Sysdig Report Exposes 91% Failure in Runtime Scans – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A substantial 91% of runtime scans are failing within organizations, signaling a significant reliance on identifying issues rather than preventing them,...
US Sanctions Egyptian IT Experts Aiding ISIS in Cybersecurity – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US government has announced sanctions against two Egyptian IT experts for providing cybersecurity support and training to the terrorist organization...
Citibank Sued For Failing to Protect Fraud Victims – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 New York’s attorney general, Letitia James, yesterday launched legal action against one of America’s biggest banks for allegedly failing to adequately protect...
City Cyber Taskforce Launches to Secure Corporate Finance – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Two of the UK’s leading accounting and security bodies are teaming up with others to launch a new taskforce today designed...
RunC Flaws Enable Container Escapes, Granting Attackers Host Access – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 31, 2024NewsroomSoftware Security / Linux Multiple security vulnerabilities have been disclosed in the runC command line tool that could be...
Alert: Ivanti Discloses 2 New Zero-Day Flaws, One Under Active Exploitation – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 31, 2024NewsroomVulnerability / Zero Day Ivanti is alerting of two new high-severity flaws in its Connect Secure and Policy Secure...