The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Year: 2024
2023 Visa Merchant Fraud Report
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Insider Data Breach at Verizon Affects Over 63,000 Employees – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici An insider data breach at Verizon has compromised the personal information of more than 63,000 employees, nearly half of the...
Credentialess / Username
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
2023 Cybersecurity Regulation Recap (Part 4): Tech Development & Governance – Source: securityboulevard.com
Source: securityboulevard.com – Author: NSFOCUS In 2023, countries worldwide continued to strengthen their cybersecurity capabilities and systems in response to their national needs, using regulatory means...
Single Sign-On with Fortra IdP – Source: securityboulevard.com
Source: securityboulevard.com – Author: Digital Defense by Fortra What is Fortra IdP? Fortra Identity Provider (IdP) serves as a centralized solution that allows users to log...
USENIX Security ’23 – Internet Service Providers’ And Individuals’ Attitudes, Barriers, And Incentives To Secure IoT – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Nissy Sombatruang, Tristan Caulfield, Ingolf Becker, Akira Fujita, Takahiro Kasama, Koji Nakao, Daisuke Inoue Many thanks to USENIX for...
Cybersecurity and the Law: Taking Proactive Steps Before Needing Legal Action – Source: securityboulevard.com
Source: securityboulevard.com – Author: Digital Defense by Fortra How the justice system deals with cybercrime is still relatively new and finding its footing. How cybercriminals are...
Breaking Bitlocker – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rick It was only a matter of time before someone did this. Bitlocker is Microsoft’s technique for encrypting a desktop, laptop, or...
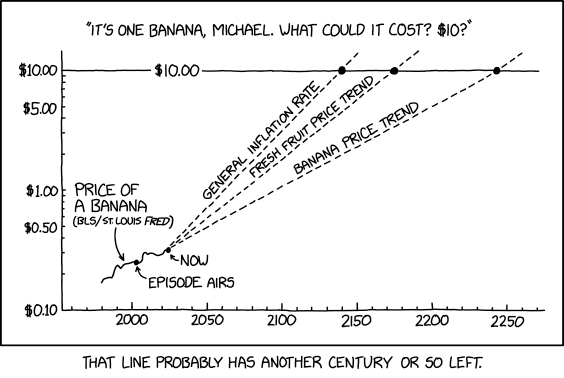
Randall Munroe’s XKCD ‘Banana Prices’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
Simplifying Cybersecurity from Confusion to Clarity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tony Bradley Cybersecurity is a dynamic and fast-paced industry. Staying ahead of threats requires constant innovation and a keen understanding of the...
LogonBox VPN 2.4.6 – Now Available – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lee Painter Introduction LogonBox is pleased to announce the immediate availability of LogonBox VPN 2.4.6.This release includes further performance improvements to some...
LogonBox SSPR 2.4.6 – Now Available – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lee Painter Introduction LogonBox is pleased to announce the immediate availability of LogonBox SSPR 2.4.6.This release includes further performance improvements to some...
Ransomware Disrupts Hospital Services in Romania and France – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific Emergency Services Are Suspended as Digital Systems Are Pulled Offline Mihir Bagwe...
Virtual Event I APAC Operational Technology Security Summit – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Operational Technology (OT) Presented by Fortinet 150 min As industrial organizations continue...
Bipartisan Senate Bill Requires HHS to Bolster Cyber Efforts – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Healthcare , Industry Specific Legislation Aims to Evaluate and Improve Agency’s Cybersecurity Posture Marianne Kolbasuk McGee...
Webinar | Combatting Rogue URL Tricks: How You Can Quickly Identify and Investigate the Latest Phishing Attacks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Roger Grimes Data-Driven Defense Evangelist, KnowBe4 Roger Grimes, KnowBe4’s Data-Driven Defense Evangelist, is a 30-year computer security consultant, instructor, holder of...
Data Insights Are Key to Fighting Synthetic ID Fraud – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Finance & Banking , Fraud Management & Cybercrime , ID Fraud Steve Lenderman on the Shift From Synthetic Identity to Synthetic...
Account Takeover Campaign Hits Execs in Microsoft Azure – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Business Email Compromise (BEC) , Fraud Management & Cybercrime Attackers Downloaded Files Containing Financial, Security and User Information Prajeet Nair (@prajeetspeaks)...
South Australian CyberSecurity Framework
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
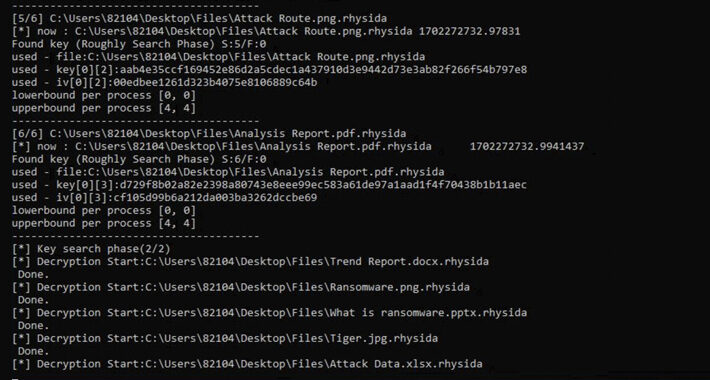
Rhysida Ransomware Cracked, Free Decryption Tool Released – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 12, 2024NewsroomVulnerability / Data Recovery Cybersecurity researchers have uncovered an “implementation vulnerability” that has made it possible to reconstruct encryption...
4 Ways Hackers use Social Engineering to Bypass MFA – Source:thehackernews.com
Source: thehackernews.com – Author: . When it comes to access security, one recommendation stands out above the rest: multi-factor authentication (MFA). With passwords alone being simple...
CISA and OpenSSF Release Framework for Package Repository Security – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 12, 2024The Hacker NewsInfrastructure Security / Software Supply Chain The U.S. Cybersecurity and Infrastructure Security Agency (CISA) announced that it’s...
Why Are Compromised Identities the Nightmare to IR Speed and Efficiency? – Source:thehackernews.com
Source: thehackernews.com – Author: . Incident response (IR) is a race against time. You engage your internal or external team because there’s enough evidence that something...
Microsoft Introduces Linux-Like ‘sudo’ Command to Windows 11 – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 12, 2024NewsroomOperating System / Technology Microsoft said it’s introducing Sudo for Windows 11 as part of an early preview version...
U.S. Offers $10 Million Bounty for Info Leading to Arrest of Hive Ransomware Leaders – Source:thehackernews.com
Source: thehackernews.com – Author: . The U.S. Department of State has announced monetary rewards of up to $10 million for information about individuals holding key positions...
U.S. DoJ Dismantles Warzone RAT Infrastructure, Arrests Key Operators – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 11, 2024NewsroomMalware / Cybercrime The U.S. Justice Department (DoJ) on Friday announced the seizure of online infrastructure that was used...
Alert: New Stealthy “RustDoor” Backdoor Targeting Apple macOS Devices – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 10, 2024NewsroommacOS Malware / Cyber Threat Apple macOS users are the target of a new Rust-based backdoor that has been...
MoqHao Android Malware Evolves with Auto-Execution Capability – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 09, 2024NewsroomMobile Security / Cyber Threat Threat hunters have identified a new variant of Android malware called MoqHao that automatically...
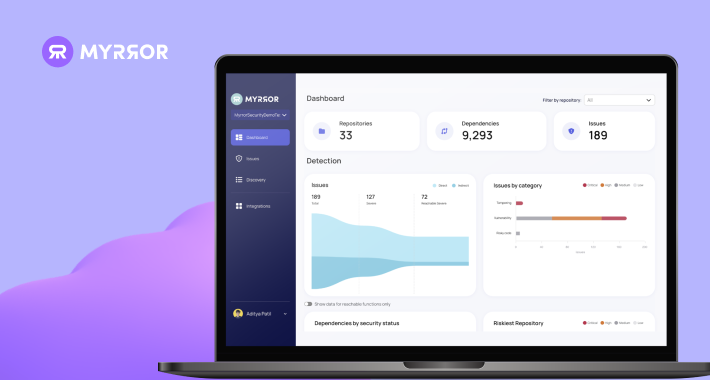
Hands-on Review: Myrror Security Code-Aware and Attack-Aware SCA – Source:thehackernews.com
Source: thehackernews.com – Author: . Introduction The modern software supply chain represents an ever-evolving threat landscape, with each package added to the manifest introducing new attack...