Source: www.securityweek.com – Author: Eduard Kovacs Palo Alto Networks informed customers late last week that it has patched a zero-day vulnerability that has been exploited to...
Day: December 30, 2024
Four-Faith Industrial Router Vulnerability Exploited in Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Threat actors have been observed exploiting a vulnerability in Four-Faith industrial routers to deploy a reverse shell, vulnerability intelligence company...
US Issues Final Rule for Protecting Personal Data Against Foreign Adversaries – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US Department of Justice has issued a final rule carrying out Executive Order (EO) 14117, which addresses the risk...
Several Chrome Extensions Compromised in Supply Chain Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Malicious versions of Cyberhaven and other Chrome extensions were published to the Google Chrome Web Store as part of a...
Cisco Confirms Authenticity of Data After Second Leak – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A hacker has leaked more data stolen from a Cisco DevHub instance and the tech giant has confirmed its authenticity...
Blown the cybersecurity budget? Here are 7 ways cyber pros can save money – Source: www.csoonline.com
Source: www.csoonline.com – Author: It’s a given that threats to enterprise are going to keep rising, stretching the resources of cybersecurity chiefs who must make their...
Brauchen Sie einen vCISO? – Source: www.csoonline.com
Source: www.csoonline.com – Author: Kommentar 29 Dezember 20243 Minuten Das Konzept des Virtual CISO sorgt für Furore. Insbesondere Mittelständler können davon profitieren – auch monetär. In...
Third Party Risk Management: So vermeiden Sie Compliance-Unheil – Source: www.csoonline.com
Source: www.csoonline.com – Author: Analyse 29 Dezember 20244 Minuten Wenn Drittanbieter gegen Vorschriften verstoßen, setzen sie ihre Auftraggeber einem Compliance-Risiko aus. Third Party Risk Management (TPRM)...
rare Сommand in Splunk – Source: socprime.com
Source: socprime.com – Author: Justin Erb The rare command in Splunk helps you find the least common values in a specific field of your data. This is useful...
coalesce Function in Splunk – Source: socprime.com
Source: socprime.com – Author: Justin Erb WRITTEN BY Justin Erb Threat Hunter [post-views] December 30, 2024 · 1 min read The Splunk coalesce function returns the first non-null...
The Traditional Advocates of the Security Perimeter Don’t Want You to Know about Data-Centric Security – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In an era defined by continuous media announcements of organizations that have suffered both government and private data breaches and...
Windows 11 Media Update Bug Stops Security Updates – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Published December 30, 2024 Microsoft advises users not to install recent security updates using physical media. The company is working...
VyprVPN Review (2025): Can It Still Perform This Year and Beyond? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Madeline Clarke We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
How to Get the Most Out of Cyber Insurance – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rita Gurevich Source: Mungkhood Studio via Shutterstock COMMENTARY Cybersecurity insurance is the fastest-growing segment of the global insurance market, and there’s a good...
What Security Lessons Did We Learn in 2024? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Joan Goodchild Source: Artur Szczybylo via Alamy Stock Photo From the growing sophistication of zero-day exploits to the entrenchment of nation-state and...
Deepfakes, Quantum Attacks Loom Over APAC in 2025 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Tero Vesalainen via Shutterstock If incidents this year are any indication, deepfakes and “harvest now, decrypt later”...
Happy 15th Anniversary, KrebsOnSecurity! – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Image: Shutterstock, Dreamansions. KrebsOnSecurity.com turns 15 years old today! Maybe it’s indelicate to celebrate the birthday of a cybercrime blog that...
Majority of UK SMEs Lack Cybersecurity Policy – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: More than two-thirds (69%) of UK small and medium enterprises (SMEs) lack a cybersecurity policy, according to figures from specialist insurance firm...
Achieve Satisfaction with Streamlined Secrets Rotation Processes – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are Secrets Rotation Processes a Keystone in Your Cybersecurity Strategy? The digital business landscape has evolved with technologies enabling organizations...
Empowering Security: Mastering Least Privilege – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why is Mastering Least Privilege Essential? The least privilege principle remains a cornerstone for securing machine identities and their secrets....
DEF CON 32 – How State Laws Meant to Protect Children Raise Other Risks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Sunday, December 29, 2024 Home » Security Bloggers Network » DEF CON 32 – How State Laws Meant to Protect...
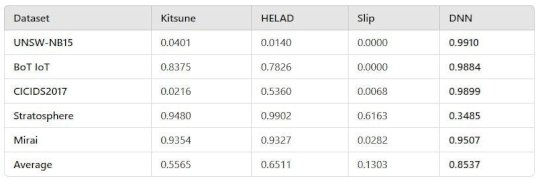
Anomaly Detection for Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Evan Powell A long promising approach comes of age I won’t revisit the arguments for anomaly detection as a crucial piece of cybersecurity....