Source: www.hackerone.com – Author: HackerOne. This blog post was contributed by Slack Staff Technical Program Manager Branden Jordan. Given the success of Slack’s previous promotion and...
Day: December 9, 2024
Live Hacking Goes Virtual – Source:www.hackerone.com
Source: www.hackerone.com – Author: Jessica Sexton. At a time when security must be managed remotely, HackerOne and Verizon Media called on the naturally remote and global...
Hack for Good: Easily Donate Bounties to WHO’s COVID-19 Response Fund – Source:www.hackerone.com
Source: www.hackerone.com – Author: HackerOne. The community has come together in some amazing ways to support COVID-19 relief efforts from Marc Rogers’ CTI League, the US...
Six years of the GitHub Security Bug Bounty program – Source:www.hackerone.com
Source: www.hackerone.com – Author: HackerOne. This guest blog post was authored by Brian Anglin, Application Security Engineer at GitHub and originally published on the GitHub company...
Live hacking the U.S. Air Force, UK Ministry of Defence and Verizon Media in Los Angeles at h1-213 – Source:www.hackerone.com
Source: www.hackerone.com – Author: Jessica Sexton. On November 6th, over 60 hackers descended on the City of Angels for the final HackerOne flagship live hacking event...
My Career Just Got Hacked: Rana Robillard Joins HackerOne – Source:www.hackerone.com
Source: www.hackerone.com – Author: Anonymous. My career just got hacked.. and I couldn’t be more excited about it. Turns out, getting your career hacked* can be...
Live Hacking Events | 2019 Recap and the Road Ahead – Source:www.hackerone.com
Source: www.hackerone.com – Author: Jessica Sexton. November 25, 2021 Event: Webinar Améliorer la sécurité en acceptant ses vulnérabilités Il y aura toujours des vulnérabilités mais elles...
Confessions of European CISOs – Source:www.hackerone.com
Source: www.hackerone.com – Author: HackerOne. Ever wondered what’s been keeping your CISO up at night? Well, wonder no more. We did some research to find out...
LINE Security Bug Bounty Program Report 2019 – Source:www.hackerone.com
Source: www.hackerone.com – Author: johnk. This guest blog post was authored by Robin Lunde from the LINE Security team and originally published on the LINE company...
Congratulations, Cosmin! The world’s seventh million-dollar bug bounty hacker – Source:www.hackerone.com
Source: www.hackerone.com – Author: HackerOne. The entire HackerOne team is beyond excited that the ranks of seven-figure-earning hackers have risen to eight this month. Cosmin (@inhibitor181)...
Hyatt Celebrates its First Anniversary on HackerOne – Source:www.hackerone.com
Source: www.hackerone.com – Author: johnk. After becoming the first hospitality brand to launch a public bug bounty program, Hyatt recently celebrated its first anniversary of the...
#AndroidHackingMonth: Introduction to Android Hacking by @0xteknogeek – Source:www.hackerone.com
Source: www.hackerone.com – Author: Joel Margolis. When I first started mobile hacking, it felt a lot like the wild west. There were very few public resources,...
Why Compliance in Cloud Security Can’t Be Ignored – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn How Does Compliance Impact Cloud Security? Are we fully conscious of the significant correlation between compliance and cloud security? With...
Compliance in Cloud Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Is Your Cloud Security Compliant? With increasing reliance on cloud systems across industries, it’s time to ask hard-hitting questions. Is...
Ensuring Calm with Effective Secrets Scanning Techniques – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are You on the Safe Side with Your Secrets Scanning? In the realm of cybersecurity, there’s a formidable challenge to...
Transform IAM From Technology Burden To Business Advantage – Source: securityboulevard.com
Source: securityboulevard.com – Author: identient The next wave of digital transformation has most enterprises racing to strengthen their IAM capabilities. Yet despite pouring millions into IAM...
DEF CON 32 – Clash, Burn And Exploit Manipulate Filters To Pwn kernelCTF – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – Clash, Burn And Exploit Manipulate Filters To Pwn kernelCTF Authors/Presenters:...
From Europe to South Africa: Where Is the World on Cyber Defense? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lohrmann on Cybersecurity Lohrmann on Cybersecurity As we wrap up 2024, two new reports suggest that Europe and leading African nations share...
What You Need to Know About Election Security – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. As election season approaches, the importance of safeguarding our democratic processes has never been more critical. Ensuring election security is...
The Top 10 Riskiest Online Destinations Revealed – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. As Americans make their travel plans, scammers lie in wait. We’ve uncovered the top ten “riskiest” destinations for travel scams...
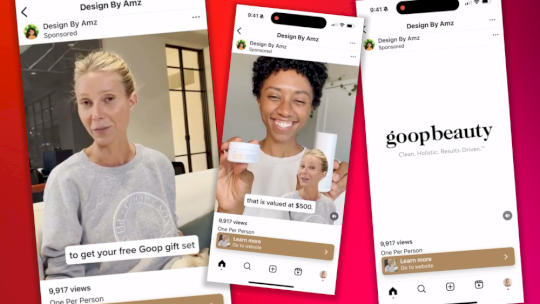
Deepfake Drama: How Gwyneth Paltrow Became the Latest Target in AI Deception – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. As technology advances, so do the methods used by cybercriminals to spread misinformation and scams. One of the most concerning...
What to Do If Your Email Is Hacked – Source:www.mcafee.com
Source: www.mcafee.com – Author: Alex Merton-McCann. I think I could count on my hand the people I know who have NOT had their email hacked. Maybe...
How to Safely Date Online – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. According to Pew, three-in-ten U.S. adults say they have used a dating site or app. That number climbs to 53%...
How To Spot A Fake Facebook Account – Source:www.mcafee.com
Source: www.mcafee.com – Author: Alex Merton-McCann. How do you manage your Facebook friends? Do you keep your list really tight and only include ‘active’ pals? Or...
How Scammers Hijack Your Instagram – Source:www.mcafee.com
Source: www.mcafee.com – Author: McAfee Labs. Authored by Vignesh Dhatchanamoorthy, Rachana S Instagram, with its vast user base and dynamic platform, has become a hotbed for...
How Do Hackers Hack Phones and How Can I Prevent It? – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. How do hackers hack phones? Several ways. Just as there are several ways you can prevent it from happening to...