Source: www.securityweek.com – Author: Ryan Naraine Japanese device maker I-O Data this week confirmed zero-day exploitation of critical flaws in multiple routers and warned that full...
Day: December 5, 2024
Watch Now: Cyber AI & Automation Summit- All Sessions Available On Demand – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek’s Cyber AI & Automation Summit took place on December 4th as a fully immersive online experience. All sessions are...
‘DroidBot’ Android Trojan Targets Banking, Cryptocurrency Applications – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A newly discovered Android remote access trojan (RAT) is targeting 77 banks, cryptocurrency exchanges, and national entities, fraud prevention firm...
50 Servers Linked to Cybercrime Marketplace and Phishing Sites Seized by Law Enforcement – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Europol announced on Thursday that law enforcement in Germany and other European countries have dismantled infrastructure associated with a cybercrime...
Bootloader Vulnerability Impacts Over 100 Cisco Switches – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cisco on Wednesday announced patches for a vulnerability in the NX-OS software’s bootloader that could allow attackers to bypass image...
Chemonics International Data Breach Impacts 260,000 Individuals – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Chemonics International is notifying over 260,000 individuals that their personal information was compromised in a year-old data breach. Chemonics is...
System Two Security Emerges From Stealth With Detection Engineering Solution – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs System Two Security this week emerged from stealth mode with a threat detection engineering solution and $7 million in seed...
White House Says at Least 8 US Telecom Firms, Dozens of Nations Impacted by China Hacking Campaign – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press A top White House official on Wednesday said at least eight U.S. telecom firms and dozens of nations have been...
UK Cyber Risks Are ‘Widely Underestimated,’ Warns Country’s Security Chief – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson In his first speech on Tuesday, the new head of the U.K.’s National Cyber Security Centre warned that the country’s...
This Secure Software Could Help Business Owners Go Remote Full Time – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published December 5, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Library of Congress Offers AI Legal Guidance to Researchers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Vitalii Vodolazskyi via Shutterstock In a net positive for researchers testing the security and safety of AI...
Russia’s ‘BlueAlpha’ APT Hides in Cloudflare Tunnels – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: Classic Image via Alamy Stock Photo NEWS BRIEF BlueAlpha, a Russian state-sponsored advanced persistent...
Bypass Bug Revives Critical N-Day in Mitel MiCollab – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Kristoffer Tripplaar via Alamy Stock Photo Two new vulnerabilities in Mitel’s MiCollab unified communications and collaboration (UCC)...
Trojan-as-a-Service Hits Euro Banks, Crypto Exchanges – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: baosheng feng via Alamy Stock Photo NEWS BRIEF A fierce Android remote access Trojan (RAT),...
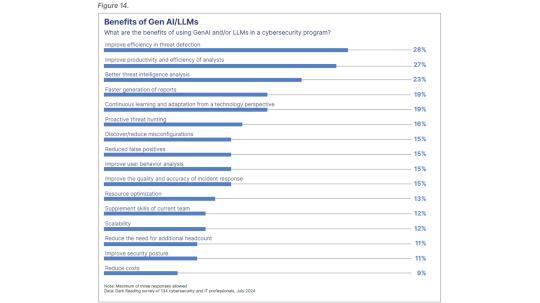
LLMs Raise Efficiency, Productivity of Cybersecurity Teams – Source: www.darkreading.com
Source: www.darkreading.com – Author: Karen Spiegelman, Features Editor Security professionals say adding LLM/GenAI capabilities to security programs improves efficiency in threat detection and increases productivity of...
‘Earth Minotaur’ Exploits WeChat Bugs, Sends Spyware to Uyghurs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: BeeBright via Shutterstock A newly identified cyber-threat operation is using a known exploit kit to target security...
Vulnerability Management Challenges in IoT & OT Environments – Source: www.darkreading.com
Source: www.darkreading.com – Author: Malleswar Reddy Yerabolu Malleswar Reddy Yerabolu, Senior Security Engineer, North Carolina Department of Health and Human Services December 5, 2024 4 Min...
African Law Enforcement Nabs 1,000+ Cybercrime Suspects – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Golden Dayz via Shutterstock A combined effort among Interpol, Afripol, cybersecurity firms, and authorities in 19 different...
Russian FSB Hackers Breach Pakistani APT Storm-0156 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: ArcadeImages via Alamy Stock Photo Hackers operating on behalf of Russian state intelligence have breached hackers operating...
Russian money-laundering network linked to drugs and ransomware disrupted, 84 arrests – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley The UK’s National Crime Agency (NCA) has revealed details of Operation Destabilise, a years-long international law enforcement investigation into a...
Smashing Security podcast #396: Dishy DDoS dramas, and mining our minds for data – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content A CEO is arrested for turning satellite receivers into DDoS attack weapons, and we journey into the...
AI chatbot startup WotNot leaks 346,000 files, including passports and medical records – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley An Indian AI startup that helps businesses build custom chatbots has leaked almost 350,000 sensitive files after the data was...
Tenable’s Amit Yoran Takes Medical Leave; Interim CEOs Named – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Cloud Security , Governance & Risk Management , Security Operations CFO Stephen Vintz, COO Mark Thurmond to Run Tenable as CEO Yoran...
Mitel MiCollab VoIP Software: Zero-Day Vulnerability Alert – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Security Operations No Patch Yet Available for Second Zero Day to Be...
AI and ‘Customer Zero’ Practices for Enhanced Usability – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Email Security & Protection , Fraud Management & Cybercrime , Open XDR Barracuda’s Siroui Mushegian on Building Resilient Solutions Through Collaboration Tom...
Russian Money Laundering Services Busted in UK-Led Operation – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Finance & Banking , Fraud Management & Cybercrime , Industry Specific French Police Reportedly Detain Accused Ryuk Money Launderer Ekaterina Zhdanova Akshaya...
Russian Money Laundering Services Busted in UK-Led Operation – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Finance & Banking , Fraud Management & Cybercrime , Industry Specific French Police Reportedly Detain Accused Ryuk Money Launderer Ekaterina Zhdanova Akshaya...
Experts Warn DHS Surveillance Tech Lacks Privacy Protections – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Artificial Intelligence & Machine Learning , Governance & Risk Management , Government Privacy Advocates Warn of Risks from Expanding DHS Use of...
US FTC Cracks Down Geolocation Data Brokers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Governance & Risk Management , Privacy , Standards, Regulations & Compliance Gravy Analytics and Mobilewalla Ordered to Implement Stronger Consent Measures Anviksha...
Police Shutter Largest German-Speaking Criminal Marketplace – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Cybercrime , Fraud Management & Cybercrime Crimenetwork Served as a Platform for Illegal Goods and Services Akshaya Asokan (asokan_akshaya) • December 4,...