Source: www.databreachtoday.com – Author: Managed Detection & Response (MDR) , Open XDR , Security Operations Security Operations Purchase Brings Cloud-Native XDR, MDR to IT Management Platform...
Day: November 21, 2024
Feds Seize PopeyeTools Marketplace, Charge Alleged Operators – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Cybercrime , Fraud Management & Cybercrime , ID Fraud Justice Department Dismantles Cybercrime Hub, Announces Charges and Seizes Crypto Chris Riotta (@chrisriotta)...
Nightwing CEO on Post-Raytheon Independence, Cyber Expertise – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Standards, Regulations & Compliance Nightwing’s John DeSimone Talks Growth, Threats,...
AI-nt Nothing Gonna Break My Defense: Securing Against Automated Attacks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: The Future of AI & Cybersecurity Presented by Palo Alto Networks x Google Cloud 60 minutes As AI...
Live Webinar | How to Build Cyber Resilience with Proactive Incident Response Strategies – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 3rd Party Risk Management , Governance & Risk Management Presented by ProcessUnity 60 minutes This webinar covers how...
Navigating the Unstructured Data Maze: Your Journey Starts Here – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Cloud Data Security & Resilience , Security Operations Presented by Rubrik 60 Minutes Organizations are grappling with massive...
Let’s Give Thanks for How Far We’ve Come – and Forge Ahead! – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Professional Certifications & Continuous Training , Training & Security Leadership Cybersecurity Training and Education Must Evolve to Keep Pace With the Profession...
N-able Strengthens Cybersecurity via $266M Adlumin Purchase – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Managed Detection & Response (MDR) , Open XDR , Security Operations Security Operations Purchase Brings Cloud-Native XDR, MDR to IT Management Platform...
Feds Seize PopeyeTools Marketplace, Charge Alleged Operators – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Cybercrime , Fraud Management & Cybercrime , ID Fraud Justice Department Dismantles Cybercrime Hub, Announces Charges and Seizes Crypto Chris Riotta (@chrisriotta)...
Nightwing CEO on Post-Raytheon Independence, Cyber Expertise – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Standards, Regulations & Compliance Nightwing’s John DeSimone Talks Growth, Threats,...
Coast Guard Warns of Continued Risks in Chinese Port Cranes – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Critical Infrastructure Security Military Says Ship-to-Shore Cranes Made in China Include Dangerous Security Flaws Chris Riotta (@chrisriotta) • November 20, 2024 ...
AI-nt Nothing Gonna Break My Defense: Securing Against Automated Attacks – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: The Future of AI & Cybersecurity Presented by Palo Alto Networks x Google Cloud 60 minutes As AI...
Live Webinar | How to Build Cyber Resilience with Proactive Incident Response Strategies – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 3rd Party Risk Management , Governance & Risk Management Presented by ProcessUnity 60 minutes This webinar covers how...
Navigating the Unstructured Data Maze: Your Journey Starts Here – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Cloud Data Security & Resilience , Security Operations Presented by Rubrik 60 Minutes Organizations are grappling with massive...
Let’s Give Thanks for How Far We’ve Come – and Forge Ahead! – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Professional Certifications & Continuous Training , Training & Security Leadership Cybersecurity Training and Education Must Evolve to Keep Pace With the Profession...
Affinity Group Spotlight: SWE’s Indigenous Women You Should Know
As part of their AG spotlight month, the Indigenous Peoples AG showcases their two co-chairs, two Indigenous women in engineering. Views: 0
SWENext Influencers: Meet Sophia Z.
Sophia is a SWENext Influencer who is passionate about showcasing STEM to young girls. Learn how she is advancing innovation in her community, including through an...
Respond to Fewer Alerts with Automated Grouping – Source: securityboulevard.com
Source: securityboulevard.com – Author: Pierre Noujeim Isn’t it annoying when multiple alerts are clearly related, but you can’t easily consolidate them into a single incident? This...
How to Motivate Employees and Stakeholders to Encourage a Culture of Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Courtney Chatterton Cybersecurity impacts us all. Third parties process and handle data every day, whether they’re tapping your phone to pay via...
Microsoft Adds Raft of Zero-Trust Tools and Platforms – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Microsoft this week launched a raft of cybersecurity initiatives that address everything from making Windows platforms more secure to adding...
Shift Left and Shift Up Workload Attack Surface Protection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Robert Levine Executive Summary: In today’s security landscape, the concept of a hardened perimeter is increasingly insufficient. With the rise of hybrid...
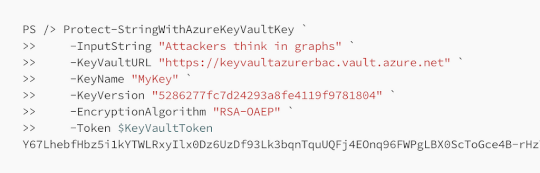
Azure Key Vault Tradecraft with BARK – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andy Robbins Brief This post details the existing and new functions in BARK that support adversarial tradecraft research relevant to the Azure...
Microsoft Veeps Ignite Fire Under CrowdStrike – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Redmond business leaders line up to say what’s new in Windows security. Microsoft vice presidents David “dwizzzle” Weston (pictured) and Pavan...
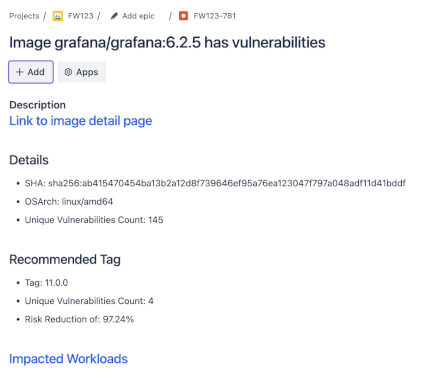
Fairwinds Insights Release Notes 16.1.11 – 16.2.4: CVE Mapping Updates – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dexter Garner Over the last few months, we’ve been working on making a number of meaningful updates to Fairwinds Insights. We’ve delivered...
CISOs Look to Establish Additional Leadership Roles – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy As cybersecurity challenges grow in complexity, chief information security officers (CISOs) are exploring new leadership roles to bolster their teams....