Source: www.csoonline.com – Author: Die OWASP-Checkliste für AI Cybersecurity und -Governance verspricht schnelle Unterstützung für Unternehmen, um generative KI sicher einzusetzen. Das Open Web Application Security...
Day: November 15, 2024
Overcome fragmented cloud security operations with unified XDR and SIEM – Source: www.csoonline.com
Source: www.csoonline.com – Author: From fragmentation to focus: Optimizing hybrid cloud security with a unified security operations center. As any security practitioner can attest, it takes...
Hacker brüsten sich mit gestohlenen Destatis-Daten – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 14 November 20243 Minuten Artificial Intelligence Im Darknet sind gestohlene Daten von zahlreichen deutschen Firmen aufgetaucht. Diese stammen vermutlich vom Statistischen...
Implementing zero trust in AI and LLM architectures: A practitioner’s guide to secure and responsible AI systems – Source: www.csoonline.com
Source: www.csoonline.com – Author: Implementing zero trust in AI and LLM architectures: A practitioner’s guide to secure and responsible AI systems Opinion 14 Nov 20248 mins...
US says China conducted massive espionage through breached telcos – Source: www.csoonline.com
Source: www.csoonline.com – Author: FBI and CISA have warned that some US telecommunication companies have been breached by China-backed Salt Typhoon to snoop on US secrets...
SWE Diverse Podcast Ep 288: CHIPS Act Update With Dr. Laurie E. Locascio of the U.S. Department of Commerce
Learn about the implementation of the bipartisan CHIPS and Science Act and its workforce development initiatives in this episode of Diverse: a SWE podcast! Views: 0
Society of Women Engineers (SWE) Executive Director Attends Congressional Gold Medal Ceremony Honoring NASA’s Hidden Figures
The 2024 event recognized women who served as computer scientists, mathematicians, and engineers for their service in advancing America’s space exploration efforts. Views: 0
Palo Alto Networks Issues AI Red Alert – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jon Swartz SANTA CLARA, Calif. — With great promise comes potential peril. And while artificial intelligence (AI) is looked upon as a...
DEF CON 32 – Redefining V2G: How To Use Your Vehicle As Game Controller – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, November 14, 2024 Home » Security Bloggers Network » DEF CON 32 – Redefining V2G: How To Use Your...
Blinded by Silence – Source: securityboulevard.com
Source: securityboulevard.com – Author: Raven Tait Blinded by Silence: How Attackers Disable EDR Overview Endpoint Detection and Response systems (EDRs) are an essential part of modern cybersecurity...
Randall Munroe’s XKCD ‘Geometriphylogenetics’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic humor & dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
Busting Ransomware’s Billion-Dollar Boom with Network Observability and Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mal Fitzgerald Busting Ransomware’s Billion-Dollar Boom with Network Observability and Security by Mal Fitzgerald Ransomware-as-a-service (RaaS) is the first example of a...
Who’s Afraid of a Toxic Cloud Trilogy? – Source: securityboulevard.com
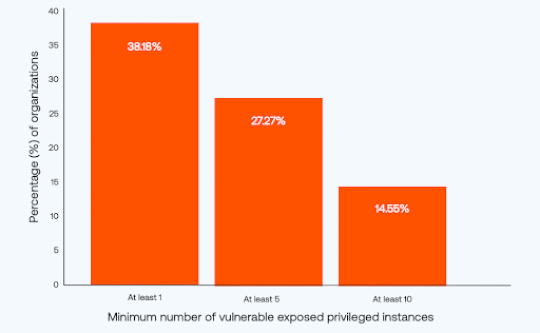
Source: securityboulevard.com – Author: Shai Morag The Tenable Cloud Risk Report 2024 reveals that nearly four in 10 organizations have workloads that are publicly exposed, contain...
Black Friday bots are coming—is your e-commerce site prepared? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kira Lempereur Commerce of all kinds surges around the end-of-year holidays—but e-commerce has been steadily growing year over year. Retail sites are...
NIST Clears Backlog of Known Security Flaws but Not All Vulnerabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The federal agency that for much of the year has struggled to keep up-to-date a detailed database of vulnerabilities has...