Source: www.securityweek.com – Author: Eduard Kovacs Israeli data loss prevention (DLP) startup MIND emerged from stealth mode on Wednesday with $11 million in seed funding. MIND...
Month: October 2024
Microsoft Warns of Russian Spear-Phishing Attacks Targeting Over 100 Organizations – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Microsoft has issued a warning over a recent large-scale spear-phishing campaign that has been attributed to the notorious Russian state-sponsored...
FakeCall Android Trojan Evolves with New Evasion Tactics and Expanded Espionage Capabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The FakeCall Android banking trojan has been enhanced with new functionality and improved evasion. The sophisticated vishing malware known as...
Colorado Accidentally Put Voting System Passwords Online, but Officials Say Election Is Secure – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Voting system passwords were mistakenly put on the Colorado Secretary of State’s website for several months before being spotted and...
Simson Garfinkel on Spooky Cryptographic Action at a Distance – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Excellent read. One example: Consider the case of basic public key cryptography, in which a person’s public and private key...
Why Did Snowflake Have a Target on It? Handling Data Warehouse Security Risks – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In early June, the Ticketmaster breach brought widespread attention to the fact that Snowflake accounts did not require multi-factor authentication...
Detection Engineering in Post SIEM and SOAR World – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team A few years back, my security team was tasked to create and maintain a green field environment for FEDRAMP compliance....
Operation Magnus: Joint Law Enforcement Operation Targets Major Infostealer Networks – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet In a sweeping international effort, the U.S. Department of Justice, Federal Bureau of Investigation, and multiple global law enforcement agencies...
Master IT Fundamentals With This CompTIA Certification Prep Bundle – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published October 30, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Best Antivirus Software for Small Businesses in 2024 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Kara Sherrer We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
Everything You Need to Know about the Malvertising Cybersecurity Threat – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Malvertising is a shortened mash-up of “malicious advertising.” In a nutshell, malvertising is a relatively new cyberattack method in which bad actors...
Filigran Expands AI-Driven Threat Intel With $35M Series B – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Threat Intelligence Insight Partners-Led Round Boosts US Growth, Fuels Threat...
CISA Opens Election War Room to Combat Escalating Threats – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Election Security , Fraud Management & Cybercrime United States’ Top Cyber Defense Agency Mobilizes Nationwide Election Support Hub Chris Riotta (@chrisriotta) •...
State Forces ENT Practice to Spend $2.25M on Better Security – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Healthcare , HIPAA/HITECH , Industry Specific NY AG Action and $1M Fine Follow Back-to-Back Hacks That Affected 224,500 in 2023 Marianne Kolbasuk...
Do Leading AI Models Comply With the EU AI Act? – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Video New Compliance Tool Say Many AI Firms Fail to...
Live Webinar | SD-WAN 3.0: APAC’s Next Phase of Network Transformation – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Cloud Next-Generation Firewall , Network Firewalls, Network Access Control , Security Operations Presented by Tata Communications 60mins The...
Career Advice: Cybersecurity Means Business – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Leadership & Executive Communication , Training & Security Leadership Understanding the Impact of Security on the Business Makes You More Effective Brandy...
Cloud Security Alliance Advocates Zero Trust for Critical Infrastructure – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Critical infrastructure, which historically have been isolated and unconnected from other networks, are becoming increasingly interconnected due to the ubiquity...
DEF CON 32 – AppSec Village – Maturing Your Application Security Program – SheHacksPurple – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, October 30, 2024 Home » Cybersecurity » Application Security » DEF CON 32 – AppSec Village – Maturing Your...
Citrix Boosts Security for Remote Application Accesses With “More Security Layers” – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sulagna Saha Connections on the internet are not secure by default, and bad actors frequently take advantage of users accessing organizations’ applications...
Survey Surfaces Fundamental Weaknesses in API Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Traceable AI today published a global survey of 1,548 IT and cybersecurity professionals that finds well over half (57%) work...
ATPC Cyber Forum to Focus on Next Generation Cybersecurity and Artificial Intelligence Issues – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Atlanta, Georgia, October 30th, 2024, CyberNewsWire White House National Cyber Director, CEOs, Key Financial Services Companies, Congressional and Executive Branch Experts...
Baby Reindeer—The dangers of real-life stalkers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avast Blog Hollywood loves a good thriller—and so do many of us. From Fatal Attraction to You, stalking is a recurring theme...
DEF CON 32 – AppSec Village – Navigating The Cyber Security Labyrinth Choose Your Own Security Adventure – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, October 31, 2024 Home » Cybersecurity » Application Security » DEF CON 32 – AppSec Village – Navigating The...
Salt Security and Dazz: A Powerful Partnership for API Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Eric Schwake As organizations adopt more modern application strategies, APIs are increasingly important for enabling seamless communication and data exchange. However, this...
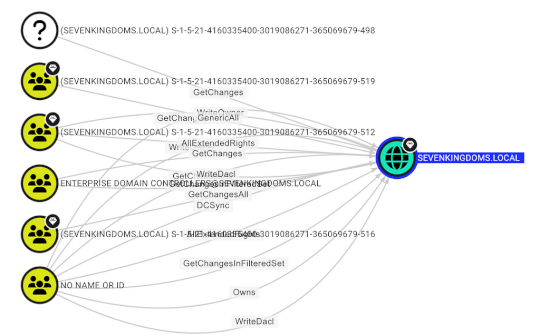
BOFHound: AD CS Integration – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matt Creel TL;DR: BOFHound can now parse Active Directory Certificate Services (AD CS) objects, manually queried from LDAP, for review and attack...
AI Cyberattacks Rise but Businesses Still Lack Insurance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Cybersecurity is a leading concern for risk managers as AI-related cyber risks surge, and despite growing investments, many businesses still...
LiteSpeed Cache Plugin Vulnerability Poses Admin Access Risk – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A vulnerability in the LiteSpeed Cache plugin for WordPress, which has over 6 million active installations, has been discovered allowing unauthenticated visitors...
Updated FakeCall Malware Targets Mobile Devices with Vishing – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A newly evolved form of malware called FakeCall, known for its advanced use of vishing (voice phishing), has been identified by cybersecurity researchers....
Apple Rolls Out Major Security Update to Patch macOS and iOS Vulnerabilities – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Apple has released security patches for 90 of its services and operating systems, fixing some critical vulnerabilities. This major security update, released...