Source: securelist.com – Author: GReAT Grandoreiro is a well-known Brazilian banking trojan — part of the Tetrade umbrella — that enables threat actors to perform fraudulent...
Day: October 22, 2024
SEC Charges Four Companies Over Misleading Disclosures on SolarWinds Hack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine The US Securities and Exchange Commission (SEC) on Tuesday announced charges and million-dollar penalties against four prominent companies for “making...
US Police Detective Charged With Purchasing Stolen Credentials – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US Department of Justice has announced charges against a Buffalo police detective who allegedly bought stolen credentials and on...
Stream.Security Secures $30 Million Series B – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Israeli early-stage startup Stream.Security has banked $30 million in a new round of venture capital funding to continue work on...
SecurityWeek’s 2024 ICS Cybersecurity Conference Kicks Off in Atlanta – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek’s 2024 ICS Cybersecurity Conference kicks off today at the InterContinental Hotel Buckhead Atlanta. With 80+ sessions over three days, the conference...
Google Warns of Samsung Zero-Day Exploited in the Wild – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A zero-day vulnerability in Samsung’s mobile processors has been leveraged as part of an exploit chain for arbitrary code execution,...
Critical Vulnerabilities Expose mbNET.mini, Helmholz Industrial Routers to Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Germany’s CERT@VDE has alerted organizations to several critical and high-severity vulnerabilities discovered recently in industrial routers. Impacted vendors have released...
BlackCat Ransomware Successor Cicada3301 Emerges – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Alphv/BlackCat ransomware gang might have pulled an exit scam in early March, but the threat appears to have resurfaced...
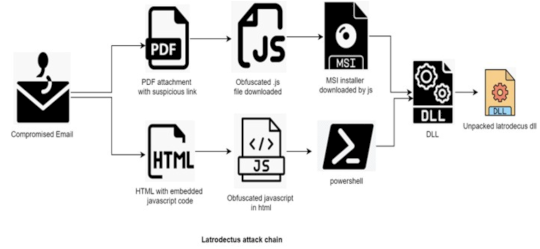
Latrodectus Malware Increasingly Used by Cybercriminals – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The Latrodectus malware has been increasingly used by cybercriminals, with recent campaigns targeting the financial, automotive and healthcare sectors, according...
Securing the Supply Chain by Working With Ethical Hackers – Source:www.hackerone.com
Source: www.hackerone.com – Author: HackerOne. Software supply chain attacks increasingly create concern among cybersecurity experts as these exploits are becoming more common. But solving the problem...
Socket Accelerates Open-Source Security With $40M Series B – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Application Security , Application Security & Online Fraud , Fraud Management & Cybercrime Socket Plans to Triple Headcount After Big Growth, Deliver...
Researchers Debut AI Tool That Helps Detect Zero-Days – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Artificial Intelligence & Machine Learning , Governance & Risk Management , Next-Generation Technologies & Secure Development Vulnerability Tool Detected Flaws in OpenAI...
CISA Ramping Up Election Security Warnings as Voting Begins – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Election Security , Fraud Management & Cybercrime , Government US Cyber Defense Agency Says Election Is Secure Despite Intensifying Threats Chris Riotta...
Dental Center Chain Settles Data Breach Lawsuit for $2.7M – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Legislation & Litigation , Standards, Regulations & Compliance 2023 Hacking Incident Affected 1.9 Million Patients, Employees Marianne Kolbasuk McGee (HealthInfoSec) • October...
What Today’s SOC Teams Can Learn From Baseball – Source: www.darkreading.com
Source: www.darkreading.com – Author: Mike Mitchell Mike Mitchell, VP, Threat Hunt Intelligence, Intel 471 October 22, 2024 5 Min Read Source: Augustas Cetkauskas via Alamy Stock...
Name That Toon: The Big Jump – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Klossner, Cartoonist Need a push? A day for a cybersecurity professional can be full of adrenaline-pumping moments. Come up with a...
Russia-Linked Hackers Attack Japan’s Govt, Ports – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: StudioProX via Shutterstock Two Russian hacking groups leveled distributed denial-of-service (DDoS) attacks at Japanese logistics and shipbuilding...
Unmanaged Cloud Credentials Pose Risk to Half of Orgs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Artur Marciniec via Alamy Stock Photo Almost half of organizations have users with “long-lived” credentials in cloud services,...
Cisco Disables DevHub Access After Security Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Sergiy Palamarchuk via Shutterstock Cisco has disabled public access to one of its DevHub environments after threat...
Internet Archive Gets Pummeled in Round 2 Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Postmodern Studio via Alamy Stock Photo Just a few days after the Internet Archive told the public it...
Socket Accelerates Open-Source Security With $40M Series B – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Application Security , Application Security & Online Fraud , Fraud Management & Cybercrime Socket Plans to Triple Headcount After Big Growth, Deliver...
Researchers Debut AI Tool That Helps Detect Zero-Days – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Artificial Intelligence & Machine Learning , Governance & Risk Management , Next-Generation Technologies & Secure Development Vulnerability Tool Detected Flaws in OpenAI...
CISA Ramping Up Election Security Warnings as Voting Begins – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Election Security , Fraud Management & Cybercrime , Government US Cyber Defense Agency Says Election Is Secure Despite Intensifying Threats Chris Riotta...
Dental Center Chain Settles Data Breach Lawsuit for $2.7M – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Legislation & Litigation , Standards, Regulations & Compliance 2023 Hacking Incident Affected 1.9 Million Patients, Employees Marianne Kolbasuk McGee (HealthInfoSec) • October...
Live Webinar | SOC Monitoring: Around-the-Clock Threat Protection for Government Agencies – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: Presented by Center for Information Security (CIS) 60 Minutes If you’re like other U.S. State, Local, Tribal, and...
AI and the SEC Whistleblower Program – Source: www.schneier.com
Source: www.schneier.com – Author: B. Schneier Tax farming is the practice of licensing tax collection to private contractors. Used heavily in ancient Rome, it’s largely fallen...
Microsoft geht jetzt unter die Phish-Fänger – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 21 Oktober 20244 Minuten CyberkriminalitätPhishing Der Tech-Riese erstellt gefälschte Azure-Tenants, um Phisher in Honeypots zu locken und ihr Verhalten zu analysieren....
Internet Archive breached twice within days – Source: www.csoonline.com
Source: www.csoonline.com – Author: The second breach used stolen tokens from the first attack that remained un-rotated even days later. Internet Archive continues to be in...
Cisco bestätigt Datenklau – Source: www.csoonline.com
Source: www.csoonline.com – Author: Hacker haben Daten von Cisco gestohlen. JRdes – Shutterstock.com In der vergangenen Woche sorgte ein Darknet-Post mit angeblich gestohlenen Cisco-Daten für Aufregung....
Detect Brute Force and Credential Access Activity Linked to Iranian Hackers: The FBI, CISA, and Partners Warn Defenders of Growing Attacks Against Critical Infrastructure Organizations – Source: socprime.com
Source: socprime.com – Author: Daryna Olyniychuk WRITTEN BY Daryna Olyniychuk Team Lead of Marketing [post-views] October 21, 2024 · 5 min read At the end of...