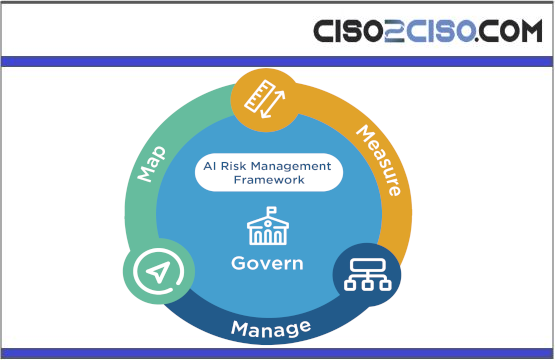
Generative Artificial Intelligence Profile The document “NIST AI 600-1, Artificial Intelligence Risk Management Framework: Generative Artificial Intelligence Profile” outlines a comprehensive framework for managing risks associated...
Day: June 17, 2024
National Cyber Strategy 2022
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Ley Marco de Ciberseguridad e Infraestructura Crítica de la Información
La Ley Marco de Ciberseguridad tiene como objetivo principal establecer un marco normativo que regule y coordine la ciberseguridad entre organismos estatales y privados. Esta ley...
MALWARE DEVELOPMENT PROCESS DIARIES
IN THIS COMPREHENSIVE GUIDE, WE DELVE INTO THE WORLD OF ANDROID SECURITY FROM AN OFFENSIVE PERSPECTIVE, SHEDDING LIGHT ON THE VARIOUS TECHNIQUES AND METHODOLOGIES USED BY...
MALWARE DEVELOPMENT EVADING DIARIES
IN THE INTRICATE LANDSCAPE OF CYBERSECURITY, MALWARE STANDS AS A PERVASIVE AND EVER-EVOLVING THREAT, CONTINUALLY ADAPTING TO CIRCUMVENT DETECTION AND EXPLOIT VULNERABILITIES IN DIGITAL SYSTEMS. ITS...
NSA Network Infrastructure Security Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
NIST SP 800 Incident Response Recommendations and Considerations for Cybersecurity Risk Management
Incident response is a critical part of cybersecurity risk management and should be integrated across organizational operations. The six CSF 2.0 Functions play vital roles in...
NIST Policy Template Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
NIST AI_Risk Management Framework Playbook
The Playbook provides suggested actions for achieving the outcomes laid out inthe AI Risk Management Framework (AI RMF) Core (Tables 1 – 4 in AI RMF1.0)....
Malware prevention tips for businesses
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Mail Server Attacks Cheat Sheet
A cheat sheet that contains common enumeration and attack methods for Mail Server. The document provides a comprehensive overview of various attacks and information gathering techniques...
MERGERS AND ACQUISITIONS
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Loaders Unleashed
The technical summary delves into loaders in various programming languages, emphasizing their functionalities and mechanisms. C/C++ loaders are vital for linking external resources, enhancing application efficiency...
Linux Privilege Escalation
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Artificial Intelligence and Cybersecurity
The Centre for European Policy Studies (CEPS) launched a Task Force on Artificial Intelligence (AI) and Cybersecurity in the autumn of 2019. The goal of this...
National Cybersecurity Strategy
The National Cybersecurity Strategy in Saudi Arabia aims to enhance cybersecurity measures in alignment with the Kingdom’s Vision 2030 and the evolving digital landscape. Developed with...
How to build a SOC with limited resources
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Kubernetes and Cloud Native Associate (KCNA) Study Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Management structures and responsibilities
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Remember: Compliance is a checkbox, Real Cybersecurity is a journey.
The Cybersecurity Misconception: Compliance ≠ Security In the complex digital landscape of modern business, robust cybersecurity is paramount. However, a pervasive misconception persists: the belief that...