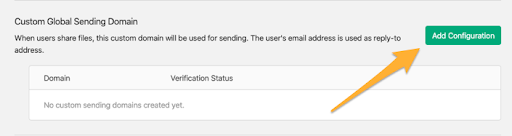
Source: securityboulevard.com – Author: EasyDmarc This instructional article will demonstrate the Survalyzer configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure...
Day: May 2, 2024
Vtiger SPF & DKIM Setup: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc Vtiger is a cloud-based CRM that enables businesses to deliver outstanding customer experiences by breaking barriers between their marketing, sales, and...
Spamhero SPF and DKIM configuration: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc This instructional article will demonstrate the Spamhero configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure...
How to Protect Against Phishing Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Leah Hopper Introduction Phishing attacks are an increasingly frequent problem and a grave threat that can cripple businesses and ruin lives. These...
Simply SPF and DKIM configuration: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc This instructional article will demonstrate the Simply configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure...
Showpad SPF and DKIM configuration: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc This instructional article will demonstrate the Showpad configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure...
Rocketseed SPF and DKIM configuration: Step By Step Guideline – Source: securityboulevard.com
Source: securityboulevard.com – Author: EasyDmarc This instructional article will demonstrate the Rocketseed configuration process of Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) Signatures to ensure...
Hyperbole, Misinformation, and CyberMonsters Under the Bed – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin By Ken Westin, Field CISO, Panther Labs This week at the World Economic Forum, there was a panel titled “Are Banks...