Source: www.bleepingcomputer.com – Author: Bill Toulas The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has released a new version of “Malware Next-Gen,” now allowing the public...
Month: April 2024
OpenTable is adding your first name to previously anonymous reviews – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Restaurant reservation platform OpenTable says that all reviews on the platform will no longer be fully anonymous starting May 22nd...
LastPass: Hackers targeted employee in failed deepfake CEO call – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan LastPass revealed this week that threat actors targeted one of its employees in a voice phishing attack, using deepfake audio...
Optics giant Hoya hit with $10 million ransomware demand – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A recent cyberattack on Hoya Corporation was conducted by the ‘Hunters International’ ransomware operation, which demanded a $10 million ransom...
CISA orders agencies impacted by Microsoft hack to mitigate risks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan CISA has issued a new emergency directive ordering U.S. federal agencies to address risks resulting from the breach of multiple...
Intel and Lenovo servers impacted by 6-year-old BMC flaw – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas An almost 6-year-old vulnerability in the Lighttpd web server used in Baseboard Management Controllers has been overlooked by many device...
CISA says Sisense hack impacts critical infrastructure orgs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is investigating the recent breach of data analytics company Sisense, an incident...
Apple: Mercenary spyware attacks target iPhone users in 92 countries – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Apple has been notifying iPhone users in 92 countries about a “mercenary spyware attack” attempting to remotely compromise their device. In...
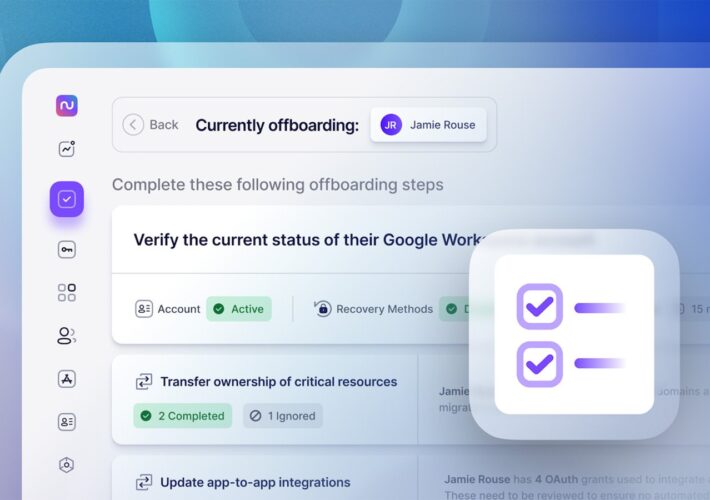
How to automate up to 90% of IT offboarding tasks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Nudge Security Employee offboarding isn’t anybody’s favorite task—but it’s a critical IT process that needs to be executed diligently and...
DuckDuckGo launches a premium Privacy Pro VPN service – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas DuckDuckGo has launched a new paid-for 3-in-1 subscription service called ‘Privacy Pro,’ which includes a virtual private network (VPN), a...
Met police failed to act on Commons ‘honeytrap’ sexting reports last year – Source: www.theguardian.com
Source: www.theguardian.com – Author: Aletha Adu The Metropolitan police first had reports of unsolicited messages targeting a number of MPs, staff and journalists in Westminster last...
Why CISA is Warning CISOs About a Breach at Sisense – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The U.S. Cybersecurity and Infrastructure Security Agency (CISA) said today it is investigating a breach at business intelligence company Sisense, whose...
Apple Boosts Spyware Alerts For Mercenary Attacks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Apple has updated its documentation related to its warning system for mercenary spyware threats, now specifying that it alerts users when...
Data Breach Exposes 300k Taxi Passengers’ Information – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity researchers have uncovered a significant data exposure concerning nearly 300,000 taxi passengers in the UK and Ireland. Jeremiah Fowler, in...
New Android Espionage Campaign Spotted in India and Pakistan – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Researchers from cybersecurity firm ESET found that a recent cyber espionage campaign using the open-source malware XploitSPY targeted Android users in...
Raspberry Robin Distributed Through Windows Script Files – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Threat actors distributing Raspberry Robin now use Windows Script Files (WSF) to spread the worm alongside other methods, such as USB...
Threat Actors Game GitHub Search to Spread Malware – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Threat actors are going to great lengths to ensure that malicious code hidden in legitimate-looking GitHub repositories is used by as...
US Data Breach Reports Surge 90% Annually in Q1 – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The first three months of 2024 saw 841 publicly reported “data compromises” – up 90% on the same period last year,...
4 Best Open Source Password Managers for Teams in 2024 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
Cybersecurity: Benefits and Best Practices – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cybercriminal activity is increasing. It is no longer a matter of if an attack will happen, but of when. From small companies...
Japan, Philippines, & US Forge Cyber Threat Intel-Sharing Alliance – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Viacheslav Lopatin via Shutterstock The US, Japan, and the Philippines reportedly will join forces in cybersecurity defense...
XZ Utils Scare Exposes Hard Truths About Software Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Juliana_haris via Shutterstock The recent discovery of a backdoor in the XZ Utils data compression utility —...
National Security Agency Announces Dave Luber As Director of Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE FORT MEADE, Md. – Dave Luber began as the National Security Agency’s (NSA) new Director of Cybersecurity on April 1....
MedSec Launches Cybersecurity Program For Resource-Constrained Hospitals – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE MIAMI, April 8, 2024/PRNewswire/ — MedSec, a leading medical device security services firm, announced today it is expanding its service...
Wiz Acquires Gem Security to Expand Cloud Detection and Response Offering – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE NEW YORK, April 10, 2024 – Cloud security leader Wiz has announced the acquisition of New York-based startup Gem Security. With a valuation...
Selecting the Right Authentication Protocol for Your Business – Source: www.darkreading.com
Source: www.darkreading.com – Author: Meir Wahnon, Co-Founder, Descope Source: Tomasz Zajda via Alamy Stock Photo Authentication protocols serve as the backbone of online security, enabling users...
NSA Updates Zero-Trust Advice to Reduce Attack Surfaces – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Brain Light via Alamy Stock Photo The National Security Agency has published its latest guidance...
TA547 Uses an LLM-Generated Dropper to Infect German Orgs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Ole.CNX via Shutterstock Researchers from Proofpoint recently observed a malicious campaign targeting dozens of organizations across various...
NIST CSF 2.0: What has changed?
The NIST Cybersecurity Framework (CSF) 2.0 introduces desired outcomes to address cybersecurity risks alongside other business risks. These outcomes are sector-specific, technology-neutral, and can be mapped...
Industrial Control Systems: Engineering Foundations and Cyber-Physical Attack Lifecycle
Advances in computing and networking have added new capabilities to physical systems that could not be feasibly added before. This has led to the emergence of...