Source: securityboulevard.com – Author: Jeffrey Burt The takedown this week of a massive phishing-as-a-service (PhaaS) operation spanned law enforcement agencies from both sides of the Atlantic...
Day: April 20, 2024
Choosing SOC Tools? Read This First [2024 Guide] – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shriram Sharma Security operations centers (SOCs) are the front lines in the battle against cyber threats. They use a diverse array of...
USENIX Security ’23 – GAP: Differentially Private Graph Neural Networks with Aggregation Perturbation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: *Sina Sajadmanesh, Ali Shahin Shamsabadi, Aurélien Bellet, Daniel Gatica-Perez* Many thanks to USENIX for publishing their outstanding USENIX Security...
SafeBreach Coverage for AA24-109A (Akira Ransomware) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kaustubh Jagtap Author: Kaustubh Jagtap, Product Marketing Director, SafeBreach On April 18th, the United States’ Federal Bureau of Investigation (FBI), Cybersecurity and...
Taking Time to Understand NIS2 Reporting Requirements – Source: securityboulevard.com
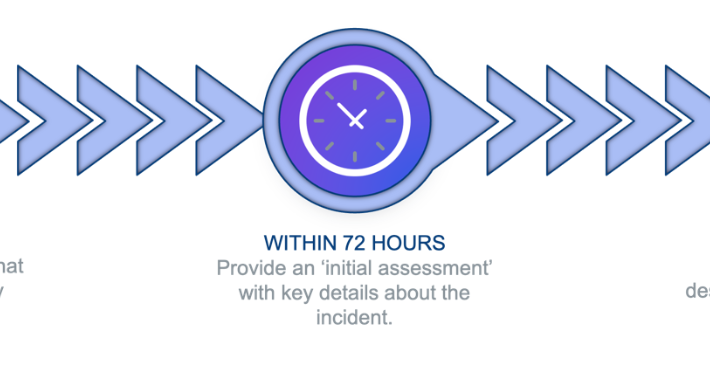
Source: securityboulevard.com – Author: Brian Robertson The newest version of the European Union Network and Information Systems directive, or NIS2, came into force in January 2023....
Daniel Stori’s ‘WC’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the inimitable Daniel Stori at Turnoff.US! Permalink *** This is a Security Bloggers Network syndicated blog from Infosecurity.US authored...
USENIX Security ’23 – Inductive Graph Unlearning – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Inductive Graph Unlearning by Marc Handelman on...
From DAST to dawn: why fuzzing is better solution | Code Intelligence – Source: securityboulevard.com
Source: securityboulevard.com – Author: Natalia Kazankova Security testing allows you to evaluate the robustness of applications and systems and identify potential weaknesses that attackers may exploit....
Cybersecurity Insights with Contrast CISO David Lindner | 4/19/24 – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Lindner, Director, Application Security Insight #1 One of the most significant errors an organization can make is assuming they are not...
UK ICO Weighs Role of ‘Accuracy’ in Generative AI – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Governance & Risk Management , Next-Generation Technologies & Secure Development But Accurate Data Doesn’t Always...
Live Webinar | Modernizing Identity Management: From Legacy Systems to Cutting-Edge Security – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Hacker Threatens to Expose Sensitive World-Check Database – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime ‘GhostR’ Claims to Have 5.3 Million Records from Major Screening Database Chris Riotta (@chrisriotta) •...
Mitre Says Hackers Breached Unclassified R&D Network – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Incident & Breach Response , Patch Management Threat Actor Exploited Ivanti Zero-Day Vulnerabilities in Cyberattack Chris...
CEO Andre Durand on Why Ping, ForgeRock Are Better Together – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Identity & Access Management , Security Operations , Video How Ping-ForgeRock Merger Provides Enhanced Deployment Flexibility, More Services Michael Novinson (MichaelNovinson)...
Friday Squid Blogging: Squid Trackers – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Jerome • April 19, 2024 8:20 PM @Clive Robinson RE Bondi Junction incident. I guess its an internationally...
The Importance of Cyber Hygiene for Businesses – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin By Rigo Van den Broeck, Executive Vice President, Cyber Security Product Innovation at Mastercard Cybercrime is set to cost $10.3 trillion...


![choosing-soc-tools?-read-this-first-[2024-guide]-–-source:-securityboulevard.com](https://ciso2ciso.com/wp-content/uploads/2024/04/128699/choosing-soc-tools-read-this-first-2024-guide-source-securityboulevard-com-710x500.jpg)