Source: www.bleepingcomputer.com – Author: Bill Toulas A joint police operation between the Australian Federal Police (AFP) and the FBI has led to the arrest and charging...
Day: April 13, 2024
Hacker claims Giant Tiger data breach, leaks 2.8M records online – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Canadian retail chain Giant Tiger disclosed a data breach in March 2024. A threat actor has now publicly claimed responsibility for...
Palo Alto Networks zero-day exploited since March to backdoor firewalls – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Suspected state-sponsored hackers have been exploiting a zero-day vulnerability in Palo Alto Networks firewalls tracked as CVE-2024-3400 since March 26,...
UK flooded with forged stamps despite using barcodes — to prevent just that – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Royal Mail, the British postal and courier service began switching all snail mail stamps to barcoded stamps last year. The...
Threat Hunter’s Handbook – Using Log Analytics to Find and Neutralize Hidden Threats in Your Environment
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Hunters Handbook Endgame’s Guide to Adversary Hunting
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
THE EU’S MOST THREATENING by EUROPOL
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Responding to a cyber incident – a guide for CEOs
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CREDENTIAL DUMPING
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Pwning the Domain Lateral Movement
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Implementing the Health Insurance Portability and Accountability Act(HIPAA) Security Rule
This publication aims to help educate readers about the security standards included in the Health Insurance Portability and Accountability Act (HIPAA) Security Rule [Sec. Rule], as...
Data Confidentiality: Identifying and Protecting Assets Against Data Breaches
NIST SPECIAL PUBLICATION 1800-28 CHALLENGE An organization must protect its information from unauthorized access and disclosure. Data breaches large and small can have far-reaching operational, financial,...
PING Basic IP Network Troubleshooting
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
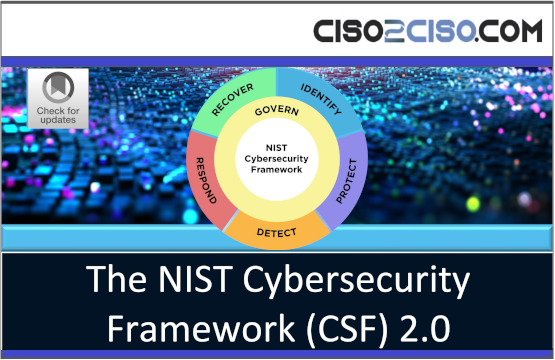
The NIST Cybersecurity Framework (CSF) 2.0
The NIST Cybersecurity Framework (CSF) 2.0 provides guidance to industry, government agencies, and organizations of all sizes and sectors to manage cybersecurity risks effectively. It offers...
Apple Alerts iPhone Users in 92 Countries to Mercenary Spyware Attacks – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson Apple sent a threat notification to iPhone users in 92 countries on April 10 informing them that their device was...
Sophos Study: 94% of Ransomware Victims Have Their Backups Targeted By Attackers – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson Organisations that have backed up their sensitive data may believe they are relatively safe from ransomware attacks; however, this is...
Friday Squid Blogging: The Awfulness of Squid Fishing Boats – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments vas pup • April 12, 2024 5:15 PM Fourteen Israeli professors awarded top EU research grants h ttps://www.timesofisrael.com/three-hebrew-university-professors-awarded-top-eu-research-grants/...
Smuggling Gold by Disguising it as Machine Parts – Source: www.schneier.com
Source: www.schneier.com – Author: B. Schneier HomeBlog Smuggling Gold by Disguising it as Machine Parts Someone got caught trying to smuggle 322 pounds of gold (that’s...
Layer 7 Visibility What are the Benefits?
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Introduction to Kubernetes Networking and Security
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Defense Industrial Base Cybersecurity Strategy 2024
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CISA Warns of Compromised Microsoft Accounts – Source: securityboulevard.com
Source: securityboulevard.com – Author: Enzoic CISA issued a fresh CISA emergency directive in early April instructing U.S. federal agencies to mitigate risks stemming from the breach...
Balbix Guide to XZ Utils Backdoor – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dragos Josanu XZ Utils is a collection of open-source command-line tools for lossless data compression, including XZ and LZMA. It is an...
USENIX Security ’23 – Fast IDentity Online with Anonymous Credentials (FIDO-AC) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
NVD’s Backlog Triggers Public Response from Cybersec Leaders – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeff Martin Just a few weeks ago, we wrote about how the National Vulnerability Database (NVD) is seriously behind in enriching CVEs....
How to Reduce the Risk of Using External AI Models in Your SDLC – Source: securityboulevard.com
Source: securityboulevard.com – Author: Roy Blit Understand how AI models add risk and how to address it. In the rapidly evolving landscape of artificial intelligence (AI),...
The XZ backdoor: What security managers can learn – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ryan Healey-Ogden In the case of the XZ breach, this backdoor could give the attacker access to anything from login information to...
Why you need an SBOM (Software Bill Of Materials) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Greg Bulmash There’s been a lot of talk about SBOMs in tech media. This blog post will help answer three crucial questions...
Shadow AI: The Murky Threat to Enterprise Adoption of Generative AI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Fulkerson Generative AI (GenAI) technologies, especially large language models like OpenAI’s GPT-4, continue to generate interest among enterprises eager to gain...
Sisense Hacked: CISA Warns Customers at Risk – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings The analytics firm kept big organizations’ secrets in an insecure AWS bucket. The government says victims include the “critical infrastructure...