Source: www.bleepingcomputer.com – Author: Bill Toulas AT&T is notifying 51 million former and current customers, warning them of a data breach that exposed their personal information...
Day: April 10, 2024
Reusing passwords: The hidden cost of convenience – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Specops Software Password reuse might seem like a small problem — a bad end-user habit that can be fixed with...
Malicious Visual Studio projects on GitHub push Keyzetsu malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Threat actors are abusing GitHub automation features and malicious Visual Studio projects to push a new variant of the “Keyzetsu” clipboard-hijacking...
Microsoft fixes two Windows zero-days exploited in malware attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has fixed two actively exploited zero-day vulnerabilities during the April 2024 Patch Tuesday, although the company failed to initially...
Critical Rust flaw enables Windows command injection attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Threat actors can exploit a security vulnerability in the Rust standard library to target Windows systems in command injection attacks....
Threat Intel Roundup Phar SEO Poisoning ScreenConnect
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Threat Intel Roundup Outlook, QNAP, Okta
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Threat Intel Roundup Outlook SmartScreen Lockbit
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Threat Intel Roundup FortiOS Super Bowl Chrome APT15
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Network Security Groups
The document provides detailed guidance on managing Network Security Groups (NSGs) in Azure for effective network traffic control. It covers creating new NSGs in the Azure...
Complete Guide to ISA/IEC 62443-3-2: Risk Assessments for Industrial Automation and Control Systems – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sectrio ISA/IEC 62443-3-2 is a globally recognized standard designed specifically to address the unique cybersecurity challenges faced by industrial control systems and...
Navigating Third-Party Cyber Risks in Healthcare: Insights from Recent Events – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joe Breen Looking at billing services’ impact on healthcare organizations Last week’s blog talked about the events that nearly brought Change Healthcare’s...
Patch Tuesday Update – April 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Digital Defense by Fortra CVE/Advisory Title Tag Microsoft Severity Rating Base Score Microsoft Impact Exploited Publicly Disclosed CVE-2024-20669 Secure Boot Security Feature...
FCC Mulls Rules to Protect Abuse Survivors from Stalking Through Cars – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt In January, the U.S. Federal Communications Commission (FCC) sent letters to automakers and wireless service providers to hear what they...
USENIX Security ’23 – Qifan Xiao, Xudong Pan, Yifan Lu, Mi Zhang, Jiarun Dai, Min Yang,- xorcising “Wraith”: Protecting LiDAR-based Object Detector In Automated Driving System From Appearing Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Qifan Xiao, Xudong Pan, Yifan Lu, Mi...
Should You Pay a Ransomware Attacker? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kevin Smith For many businesses, it’s a worst-case scenario. You open your laptop and try to access your latest presentation, report, or...
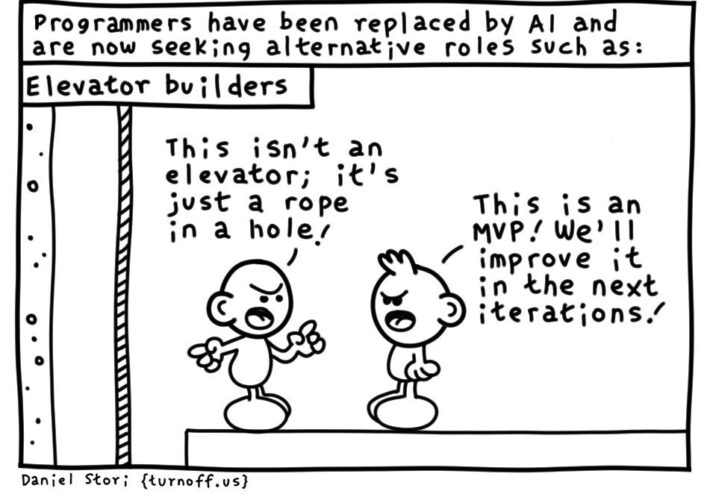
Daniel Stori’s ‘Minimum Viable Elevator’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the inimitable Daniel Stori at Turnoff.US! Permalink *** This is a Security Bloggers Network syndicated blog from Infosecurity.US authored...
MDR for Better Office 365 Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Team Nuspire Microsoft Office 365 is a stalwart suite of apps that powers collaboration, communication and productivity for companies of all sizes....
Breaking APIs with Naughty Strings – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dana Epp We all know poor input validation is a critical attack vector for exploiting software. But did you know that a...
US Bipartisan Privacy Bill Contains Cybersecurity Mandates – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Government , Industry Specific American Privacy Rights Act Has Genuine Chance of Becoming Law Chris Riotta...
Employees Are ‘Quiet Quitting’ – What Can Employers Do? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Recruitment & Reskilling Strategy , Training & Security Leadership How Employers and Employees Can Create an Engaging, Satisfying Workplace Culture Brandy...
Why Claroty Is Considering Going Public at a $3.5B Valuation – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Governance & Risk Management , Internet of Things Security Rubrik Began the IPO Process. Will Cyber-Physical Systems Vendor...
Evolving Threats Facing Robotic and Other Medical Gear – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Governance & Risk Management , Internet of Things Security Kevin Fu of Northeastern University on Latest Medical Device...
Cyera Gets $300M at $1.4B Valuation to Fuel Safe AI Adoption – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Endpoint Security , Next-Generation Technologies & Secure Development Series C Funding Round Aims to Transform...
Webinar | Enhancing Security for Government Agencies & Educational Institutions with Advanced MDR Strategies – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Bruce Johnson Senior Director, Enterprise Security, TekStream Bruce Johnson has over 38 years of experience in the information technology industry, including...
Aged D-Link NAS Devices Are Being Exploited by Hackers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security D-Link Tells Owners to Buy a Newer Model Prajeet Nair (@prajeetspeaks) • April 9, 2024 D-Link says...
Firm Says Medicare Info Obtained From DOJ Breached in Attack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Healthcare Nearly 342,000 Affected; Health Data Incident Isn’t Covered by HIPAA Rules Marianne Kolbasuk...
US Cyber Safety Review Board on the 2023 Microsoft Exchange Hack – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier US Cyber Safety Review Board released a report on the summer 2023 hack of Microsoft Exchange by China. It was...