Source: www.cyberdefensemagazine.com – Author: Gary (featuring Alice and Bob) by Rajvi Shroff It’s an age-old question. Alice wants to send a message to Bob. But how...
Day: April 5, 2024
Smart Traffic Signals Security in the Era of AI and Smart Cars – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary Analyzing the Trade-off Between Efficiency and Security in Smart Traffic Signal Technology Integration. by Samridhi Agarwal, Masters Student, CMU Once a...
Impact of IoT Security for 5G Technology – Source: securityboulevard.com
Source: securityboulevard.com – Author: Riddika Grover 5G technology impacts not just our daily lifestyle but the Internet of Things (IoT) as well. The world of 5G...
HTTP/2 CONTINUATION Flood Vulnerability – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nadav Avital HTTP/2, a widely adopted web communication protocol, organizes data transmission through a binary framing layer, wherein all communication is divided...
Smart SOAR’s Innovative Approach to Error-Handling Explained – Source: securityboulevard.com
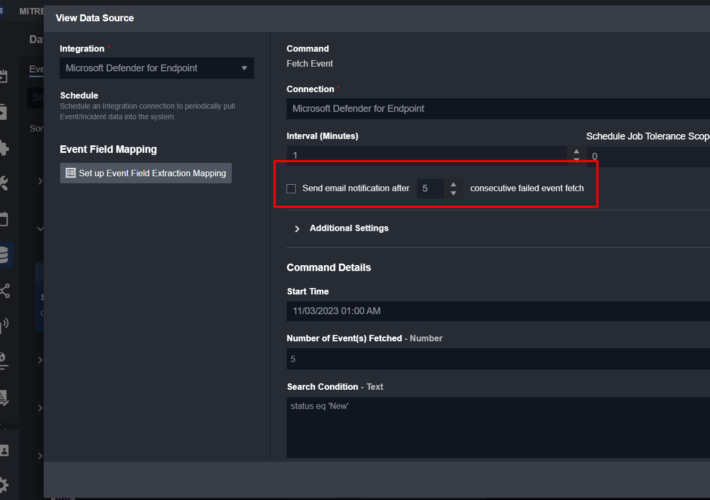
Source: securityboulevard.com – Author: Shriram Sharma Our commitment to innovation is deeply rooted in the feedback we receive from those who use our Smart SOAR platform...
How to Correctly Use Client IP Addresses in Okta Audit Logs to Improve Identity Security – Source: securityboulevard.com
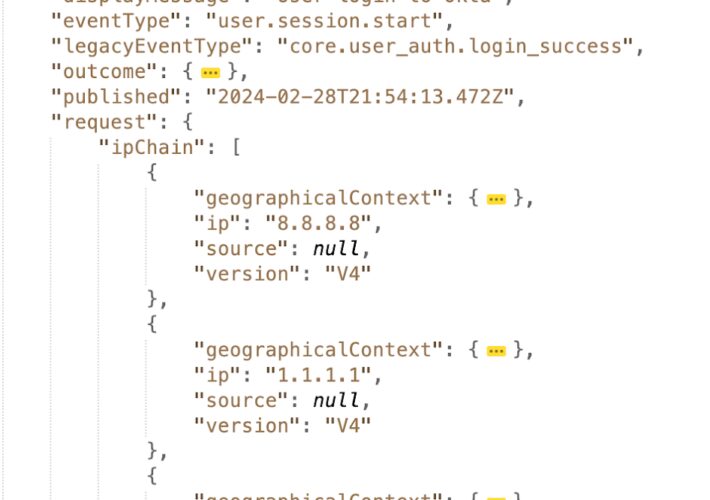
Source: securityboulevard.com – Author: Farah Iyer Being able to identify client IP addresses is essential for detecting and preventing identity-related threats. These IP addresses help establish...
Testing in Detection Engineering (Part 8) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Anton Chuvakin This blog series was written jointly with Amine Besson, Principal Cyber Engineer, Behemoth CyberDefence and one more anonymous collaborator. This...
Google Chrome Enlists Emerging DBSC Standard to Fight Cookie Theft – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Google is prototyping a new technology in Chrome that is designed to thwart the growing trend among cybercriminals of stealing...
Mastering MITRE: Enhancing Cybersecurity with Device Log Mapping – Source: securityboulevard.com
Source: securityboulevard.com – Author: Team Nuspire In the dynamic realm of cybersecurity, the MITRE ATT&CK framework has become a pivotal tool for organizations striving to fortify...
XZ and the Threats to the Digital Supply Chain – Source: securityboulevard.com
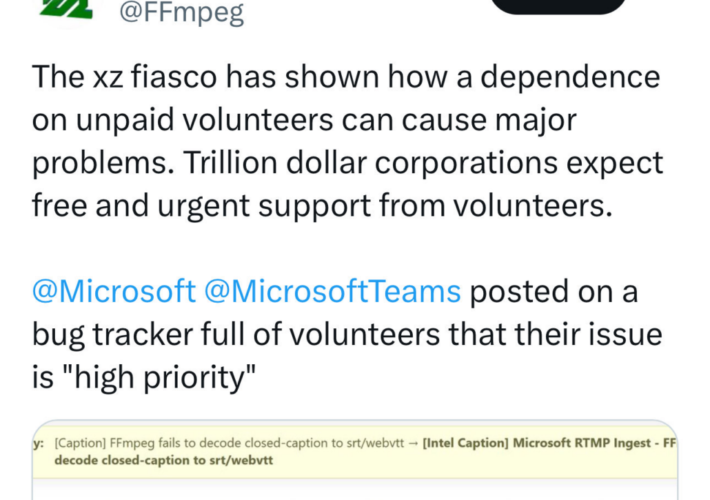
Source: securityboulevard.com – Author: Chris Garland The discovery of the backdoor in xz utils compression software last week has shone a spotlight on the threats to...
Safeguarding Data Security and Privacy on IBM Mainframe: A Comprehensive Approach – Source: securityboulevard.com
Source: securityboulevard.com – Author: Thomas Gloerfeld In today’s digitally driven world, data security and privacy are paramount concerns for organizations across all industries. With the increasing...
Google Fixes Two Pixel Zero-Days Exploited by Forensic Firms – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Bugs Allowed Device Unlocking and Memory Access Mihir Bagwe (MihirBagwe) • April 4, 2024 Google addressed two zero-day vulnerabilities...
Phishing Attacks Targeting Political Parties, Germany Warns – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Social Engineering Escalation of Cyberespionage Likely Tied to Upcoming European Elections Akshaya Asokan (asokan_akshaya) • April...
Code to Cloud Roadshow – Minneapolis In-Person Event hosted by Palo Alto Networks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Data Security & Resilience , Cloud Security , Cloud-Native Application Protection Platform (CNAPP) In-Person Event Join...
Breach Roundup: Omni Hotels Acknowledges Cyber Incident – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Incident & Breach Response Also: Insurer Predicts Ransomware for Cars, Offers to Cover Towing...
AI Deepfakes Rising as Risk for APAC Organisations – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Ben Abbott AI deepfakes were not on the risk radar of organisations just a short time ago, but in 2024, they are...
Asia-Pacific Ransomware Threats Depend on Country and Sector, Says Rapid7 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Ben Abbott Raj Samani, Chief Scientist. Image: Rapid7 New research from cyber security firm Rapid7 has shown the ransomware attacks that IT...
Get a Lifetime of VPN Protection for Just $16 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published April 4, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
5 Best Password Managers for Android in 2024 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Best overall password manager for Android: Bitwarden Best for smaller teams: NordPass Best for remote workers: 1Password Best for large...
Google Cloud/Cloud Security Alliance Report: IT and Security Pros Are ‘Cautiously Optimistic’ About AI – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse The C-suite is more familiar with AI technologies than their IT and security staff, according to a report from the...
9 Must-Do Tips to Secure Ubuntu Server – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: In today’s world, if you’re not constantly working to secure your servers, you’re already 10 steps behind every hacker on the planet....
Authy vs Google Authenticator: Two-Factor Authenticator Comparison – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares The number of businesses affected by data breaches has risen over the years, showcasing that passwords alone fail to provide...
This IT Career Kickstarter Bundle is An Extra 20% Off Through April 7th – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published April 3, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...