Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Panther Media GmbH via Alamy Stock Photo Amid a steep rise in politically motivated deepfakes, South Korea’s...
Day: March 9, 2024
Russia-Sponsored Cyberattackers Infiltrate Microsoft’s Code Base – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: ArtesiaWells via Alamy Stock Photo The Russian state-sponsored advanced persistent threat (APT) group known...
Stealth Bomber: Atlassian Confluence Exploits Drop Web Shells In-Memory – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer Source: NG Images via Alamy Stock Photo Fresh proof-of-concept (PoC) exploits are circulating in the wild for a...
Safeguarding the Code That Drives Modern Vehicles – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Soujanya Ain is a Product Marketing Manager at GitGuardian The automotive landscape has evolved dramatically, from mechanical marvels to...
Creating Security Through Randomness – Source: www.darkreading.com
Source: www.darkreading.com – Author: Andrada Fiscutean When you step inside Cloudflare’s San Francisco office, the first thing you notice is a wall of lava lamps. Visitors...
How to Ensure Open Source Packages Are Not Landmines – Source: www.darkreading.com
Source: www.darkreading.com – Author: Agam Shah, Contributing Writer Source: Steven Morris via Alamy Stock Photo Open source repositories are critical to running and writing modern applications,...
Bipartisan Members of Congress Introduce Enhanced Cybersecurity for SNAP Act to Secure Food Benefits Against Hackers and Thieves – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE Washington, D.C. – U.S. Senator Ron Wyden, D-Ore., with Sens. John Fetterman, D-Penn., and Bill Cassidy, R-La., today introduced the Enhanced...
‘The Weirdest Trend in Cybersecurity’: Nation-States Returning to USBs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Nation-state cyber threat groups are once again turning to USBs to compromise highly guarded government organizations and critical...
Cyber Insurance Strategy Requires CISO-CFO Collaboration – Source: www.darkreading.com
Source: www.darkreading.com – Author: Fahmida Y. Rashid, Managing Editor, Features, Dark Reading Source: Egor Kotenko via Alamy Stock Photo The continually growing volume of cyberattacks and...
Friday Squid Blogging: New Plant Looks Like a Squid – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Newly discovered plant looks like a squid. And it’s super weird: The plant, which grows to 3 centimetres tall and...
Essays from the Second IWORD – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier The Ash Center has posted a series of twelve essays stemming from the Second Interdisciplinary Workshop on Reimagining Democracy (IWORD...
How Public AI Can Strengthen Democracy – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier With the world’s focus turning to misinformation, manipulation, and outright propaganda ahead of the 2024 U.S. presidential election, we know...
5 Best VPNs for Social Media in 2024 (Free & Paid VPNs) – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Best for bypassing censorship: NordVPN Best for TikTok’s location-based algorithm: ExpressVPN Best for remote social media teams: Surfshark Best for...
Google Engineer Steals AI Trade Secrets for Chinese Companies – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: kenary820 via Shutterstock The US Justice Department has charged a former Google software engineer with stealing artificial...
Sam Altman Reinstated to OpenAI Board – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Company Concludes His Ouster Stemmed from ‘Breakdown In Trust’ David...
Webinar | Top SaaS Security Threat Trends in 2024 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Salah Nassar Sr. Director Product Marketing, Zscaler Salah is a passionate and customer-centric marketer with a diverse background in networking and...
Banning Ransom Payments: Calls Grow to ‘Figure Out’ Approach – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware As Ransomware Disruption Mounts, More Experts Seek Path to Banning Payments Mathew J. Schwartz (euroinfosec)...
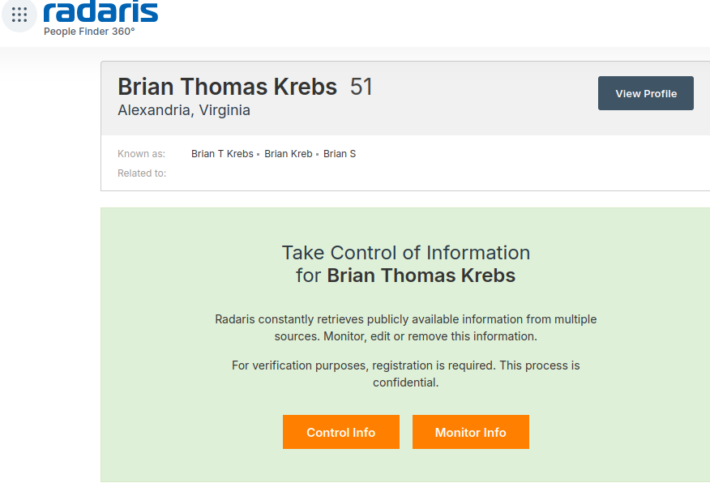
A Close Up Look at the Consumer Data Broker Radaris – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs If you live in the United States, the data broker Radaris likely knows a great deal about you, and they are...