Source: securityaffairs.com – Author: Pierluigi Paganini Canada Gov plans to ban the Flipper Zero to curb car thefts Pierluigi Paganini February 12, 2024 The Canadian government...
Month: February 2024
ExpressVPN leaked DNS requests due to a bug in the split tunneling feature – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini ExpressVPN leaked DNS requests due to a bug in the split tunneling feature Pierluigi Paganini February 12, 2024 A bug...
9 Possible Ways Hackers Can Use Public Wi-Fi to Steal Your Sensitive Data – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini 9 Possible Ways Hackers Can Use Public Wi-Fi to Steal Your Sensitive Data Pierluigi Paganini February 12, 2024 Exploring the...
US Feds arrested two men involved in the Warzone RAT operation – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini US Feds arrested two men involved in the Warzone RAT operation Pierluigi Paganini February 12, 2024 The U.S. Justice Department...
Raspberry Robin spotted using two new 1-day LPE exploits – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Raspberry Robin spotted using two new 1-day LPE exploits Pierluigi Paganini February 11, 2024 Raspberry Robin continues to evolve, it...
Security testing White Paper
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cloud Reassurance: A Framework To Enhance Resilience And Trust
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Reporting Cyber Risk to Boards
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
2023 Visa Merchant Fraud Report
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Insider Data Breach at Verizon Affects Over 63,000 Employees – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici An insider data breach at Verizon has compromised the personal information of more than 63,000 employees, nearly half of the...
Credentialess / Username
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
2023 Cybersecurity Regulation Recap (Part 4): Tech Development & Governance – Source: securityboulevard.com
Source: securityboulevard.com – Author: NSFOCUS In 2023, countries worldwide continued to strengthen their cybersecurity capabilities and systems in response to their national needs, using regulatory means...
Single Sign-On with Fortra IdP – Source: securityboulevard.com
Source: securityboulevard.com – Author: Digital Defense by Fortra What is Fortra IdP? Fortra Identity Provider (IdP) serves as a centralized solution that allows users to log...
USENIX Security ’23 – Internet Service Providers’ And Individuals’ Attitudes, Barriers, And Incentives To Secure IoT – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Nissy Sombatruang, Tristan Caulfield, Ingolf Becker, Akira Fujita, Takahiro Kasama, Koji Nakao, Daisuke Inoue Many thanks to USENIX for...
Cybersecurity and the Law: Taking Proactive Steps Before Needing Legal Action – Source: securityboulevard.com
Source: securityboulevard.com – Author: Digital Defense by Fortra How the justice system deals with cybercrime is still relatively new and finding its footing. How cybercriminals are...
Breaking Bitlocker – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rick It was only a matter of time before someone did this. Bitlocker is Microsoft’s technique for encrypting a desktop, laptop, or...
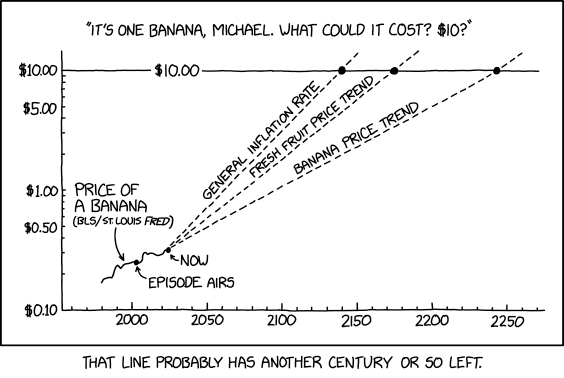
Randall Munroe’s XKCD ‘Banana Prices’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
Simplifying Cybersecurity from Confusion to Clarity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tony Bradley Cybersecurity is a dynamic and fast-paced industry. Staying ahead of threats requires constant innovation and a keen understanding of the...
LogonBox VPN 2.4.6 – Now Available – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lee Painter Introduction LogonBox is pleased to announce the immediate availability of LogonBox VPN 2.4.6.This release includes further performance improvements to some...
LogonBox SSPR 2.4.6 – Now Available – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lee Painter Introduction LogonBox is pleased to announce the immediate availability of LogonBox SSPR 2.4.6.This release includes further performance improvements to some...
Ransomware Disrupts Hospital Services in Romania and France – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific Emergency Services Are Suspended as Digital Systems Are Pulled Offline Mihir Bagwe...
Virtual Event I APAC Operational Technology Security Summit – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Operational Technology (OT) Presented by Fortinet 150 min As industrial organizations continue...
Bipartisan Senate Bill Requires HHS to Bolster Cyber Efforts – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Healthcare , Industry Specific Legislation Aims to Evaluate and Improve Agency’s Cybersecurity Posture Marianne Kolbasuk McGee...
Webinar | Combatting Rogue URL Tricks: How You Can Quickly Identify and Investigate the Latest Phishing Attacks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Roger Grimes Data-Driven Defense Evangelist, KnowBe4 Roger Grimes, KnowBe4’s Data-Driven Defense Evangelist, is a 30-year computer security consultant, instructor, holder of...
Data Insights Are Key to Fighting Synthetic ID Fraud – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Finance & Banking , Fraud Management & Cybercrime , ID Fraud Steve Lenderman on the Shift From Synthetic Identity to Synthetic...
Account Takeover Campaign Hits Execs in Microsoft Azure – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Business Email Compromise (BEC) , Fraud Management & Cybercrime Attackers Downloaded Files Containing Financial, Security and User Information Prajeet Nair (@prajeetspeaks)...
South Australian CyberSecurity Framework
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
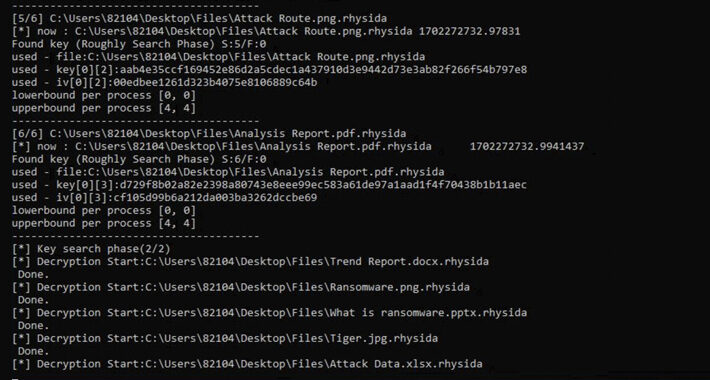
Rhysida Ransomware Cracked, Free Decryption Tool Released – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 12, 2024NewsroomVulnerability / Data Recovery Cybersecurity researchers have uncovered an “implementation vulnerability” that has made it possible to reconstruct encryption...
4 Ways Hackers use Social Engineering to Bypass MFA – Source:thehackernews.com
Source: thehackernews.com – Author: . When it comes to access security, one recommendation stands out above the rest: multi-factor authentication (MFA). With passwords alone being simple...