Source: securityboulevard.com – Author: Digital Defense by Fortra Any business that accepts credit card payments is subject to a set of security guidelines in the Payment...
Month: February 2024
Why SBOMs are essential for every organization – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens Wednesday, February 21, 2024 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
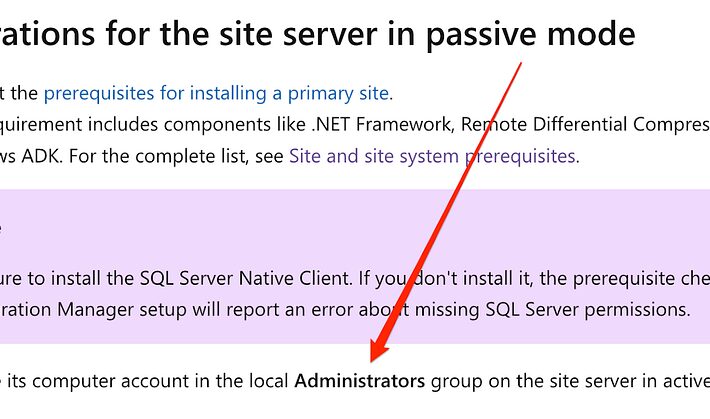
SCCM Hierarchy Takeover with High Availability – Source: securityboulevard.com
Source: securityboulevard.com – Author: Garrett Foster TL;DR: SCCM sites configured to support high availability can be abused to compromise the entire hierarchy I previously wrote about...
How is a Container Scan Done? – Source: securityboulevard.com
Source: securityboulevard.com – Author: AJ Starita Containers offer many benefits, including lightweight portability from one environment to another, but they add a layer of complexity to...
USENIX Security ’23 – William E. Bodell III, Sajad Meisami, Yue Duan – Proxy Hunting: Understanding and Characterizing Proxy-based Upgradeable Smart Contracts in Blockchains – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the organizations strong commitment to Open...
How Schools Can Comply with the Three Biggest Online Student Privacy Laws – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kevin Smith Keeping students’ data safe from prying eyes and malicious actors isn’t as simple as it used to be. Students are...
Threat Hunting Workshop 10: Hunting for Initial Access – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cyborg Security Get ready to elevate your threat hunting skills with Cyborg Security’s exhilarating and interactive workshop, focusing on the pivotal MITRE...
What to Look for in a Secrets Scanner – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tal Zacks Find out the key capabilities of secret scanners and what to consider when searching for a solution. Background In today’s...
CISA Mitigation Guide for Healthcare Organizations: Part Three – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wes Wright Identify and address at-risk assets to protect your healthcare enterprise On November 20, 2023, the Cybersecurity Infrastructure and Security Agency...
Experts Praise White House Port Cybersecurity Initiatives – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security , Governance & Risk Management , Operational Technology (OT) Cyber Actions Reflect ‘Positive Step’ in Addressing Overlooked Issues,...
Hack at Services Firm Hits 2.4 Million Eye Doctor Patients – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Cybercrime , Fraud Management & Cybercrime As Vendor Breaches Surge, Medical Practices Need 20/20 Visibility on Third Parties...
Live Webinar | Secrets Detection: Why Coverage Throughout the SDLC is Critical to Your Security Posture – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Joe Nicastro Field CTO, Legit Security Joe Nicastro is a seasoned cybersecurity expert with over a decade of experience in the...
Wyze Security Incident Exposes Private Cameras – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Internet of Things Security 13,000 Users Received Incorrect Thumbnails; 1,504 Tapped on Them, Risking Privacy Prajeet Nair (@prajeetspeaks)...
Joomla fixes XSS flaws that could expose sites to RCE attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Five vulnerabilities have been discovered in the Joomla content management system that could be leveraged to execute arbitrary code on...
Microsoft expands free logging capabilities after May breach – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has expanded free logging capabilities for all Purview Audit standard customers, including U.S. federal agencies, six months after disclosing...
Hackers abuse Google Cloud Run in massive banking trojan campaign – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Security researchers are warning of hackers abusing the Google Cloud Run service to distribute massive volumes of banking trojans like...
Fraudsters tried to scam Apple out of 5,000 iPhones worth over $3 million – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Two Chinese nationals face 20 years in prison after being caught and convicted of submitting over 5,000 fake iPhones worth...
New SSH-Snake malware steals SSH keys to spread across the network – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A threat actor is using an open-source network mapping tool named SSH-Snake to look for private keys undetected and move laterally...
US govt shares cyberattack defense tips for water utilities – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan CISA, the FBI, and the Environmental Protection Agency (EPA) shared a list of defense measures U.S. water utilities should implement...
ScreenConnect critical bug now under attack as exploit code emerges – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Both technical details and proof-of-concept exploits are available for the two vulnerabilities ConnectWise disclosed earlier this week for ScreenConnect, its...
US offers $15 million bounty for info on LockBit ransomware gang – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The U.S. State Department is now also offering rewards of up to $15 million to anyone who can provide information...
CISA Roadmap for Artificial Intelligence
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Bridging the Gap in Defence Against Phishing
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Automated Privilege Escalation
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ABC DE PROTECCION DE DATOS PERSONALES
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
A Detailed Guide on Medusa
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
A Detailed Guide on Crunch
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
A Detailed Guide on Cewl
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
A Deep Dive into Reconnaissance
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Should IT and Security Teams Play a Role in Crisis Communications? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Ben Abbott Outages and cyber incidents can have a direct impact on a company’s brand, share price and jobs, according to Louise...