Source: www.darkreading.com – Author: Dark Reading Staff Source: Robert K. Chin Storefronts via Alamy Stock Photo Microsoft has updated a zero-day exploit in its AppLocker application...
Day: February 29, 2024
FBI, CISA Release IoCs for Phobos Ransomware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer 3 Min Read Source: Rawpixel.com via Shutterstock The FBI and the US Cybersecurity and Infrastructure Security Agency (CISA)...
Chinese APT Developing Exploits to Defeat Already Patched Ivanti Users – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Alexander Tolstykh via Shutterstock A Chinese espionage group is on the verge of developing malware that can...
Biden Administration Unveils Data Privacy Executive Order – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: Andrea Izzotti via Shutterstock On Feb. 28, President Joe Biden issued an executive order with...
Troutman Pepper Forms Incidents and Investigations Team – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE ORANGE COUNTY, Calif. and RICHMOND, Va., Feb. 28, 2024 /PRNewswire/ — Troutman Pepper has formalized an Incidents + Investigations Team that caters to a growing need for comprehensive...
Healthcare sector warned of ALPHV BlackCat ransomware after surge in targeted attacks – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley What’s happened? The US government warned healthcare organizations about the risk of being targeted by the ALPHV BlackCat ransomware after...
Tenable Introduces Visibility Across IT, OT, and IoT Domains – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE COLUMBIA, Md. (February 29, 2024) — Tenable®, the Exposure Management company, today announced the release of Tenable One for OT/IoT. It is the...
Cybersecurity Startup Morphisec Appoints Ron Reinfeld As CEO – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE BOSTON, Feb. 29, 2024 /PRNewswire-PRWeb/ — Morphisec endpoint security system (MTD) has announced the appointment of Ron Reinfeld as the new CEO of the...
MITRE Rolls Out 4 Brand-New CWEs for Microprocessor Security Bugs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer 3 Min Read Source: Alexey Boldin via Shutterstock The MITRE-led Common Weakness Enumeration (CWE) program added four new...
A DETAILED GUIDE ON HONEYPOTS
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Identifying and Mitigating Living Off the Land Techniques
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Nmap for Pentester PACKET TRACE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
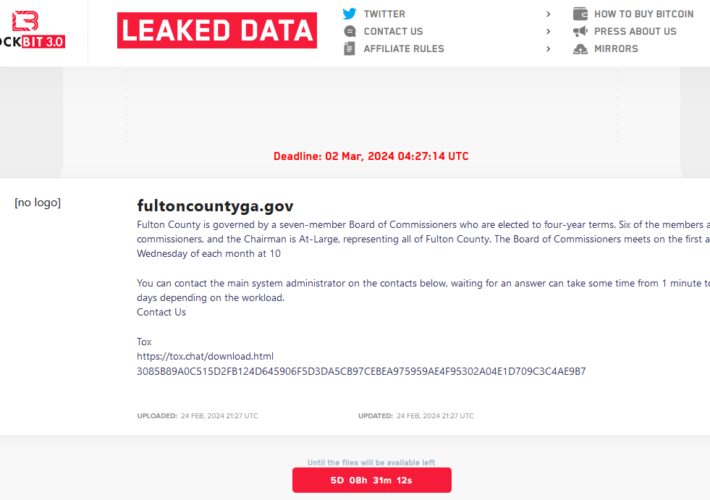
Fulton County, Security Experts Call LockBit’s Bluff – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The ransomware group LockBit told officials with Fulton County, Ga. they could expect to see their internal documents published online this...
DIRECTOR’S HANDBOOK ON CYBER-RISK OVERSIGHT
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
MULTIPLE METHOD TO SETUP KALI LINUX
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
THREAT REPORT 2024
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Pentest Best Practices Checklist
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
NMAP FOR PENTESTER
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
NTLM Abuse Methods
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
NETCAT FOR PENTESTER COMPREHENSIVE GUIDE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Why Higher Education Is So Vulnerable to Cyber Attacks — And What to Do – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin By Zac Amos, Features Editor, ReHack Cyberattacks are a growing problem worldwide as they can cause significant damage to any organization,...
Why Companies Are Still Investing in Tech During an Economic Slowdown – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin By Luke Wallace, VP of Engineering at Bottle Rocket With rising oil prices, higher interest rates, and an economic downturn plaguing...
Anycubic 3D printers hacked worldwide to expose security flaw – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Image: Midjourney According to a wave of online reports from Anycubic customers, someone hacked their 3D printers to warn that...
Malicious AI models on Hugging Face backdoor users’ machines – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas At least 100 instances of malicious AI ML models were found on the Hugging Face platform, some of which can...
New executive order bans mass sale of personal data to China, Russia – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan U.S. President Joe Biden has signed an executive order that aims to ban the bulk sale and transfer of Americans’...
Rhysida ransomware wants $3.6 million for children’s stolen data – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Rhysida ransomware gang has claimed the cyberattack on Lurie Children’s Hospital in Chicago at the start of the month....
Kali Linux 2024.1 released with 4 new tools, UI refresh – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Kali Linux has released version 2024.1, the first version of 2024, with four new tools, a theme refresh, and desktop...
Ransomware gang claims they stole 6TB of Change Healthcare data – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Image: Midjourney The BlackCat/ALPHV ransomware gang has officially claimed responsibility for a cyberattack on Optum, a subsidiary of UnitedHealth Group...
LockBit ransomware returns to attacks with new encryptors, servers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams The LockBit ransomware gang is once again conducting attacks, using updated encryptors with ransom notes linking to new servers after...
Lazarus hackers exploited Windows zero-day to gain Kernel privileges – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas North Korean threat actors known as the Lazarus Group exploited a flaw in the Windows AppLocker driver (appid.sys) as a...