Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer Source: Cro_Magnon via Alamy Stock Photo The Russia-aligned threat group known as Winter Vivern was discovered exploiting cross-site...
Day: February 17, 2024
Cyberattack Disrupts German Battery-Production Lines – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Pulsar Imagens via Alamy Stock Photo VARTA AG, a German battery manufacturer, has announced that it suffered a...
Critical Software Vulnerabilities Impacting Credit Unions Discovered by LMG Security Researcher – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE MISSOULA, Mont., Feb. 13, 2024 /PRNewswire/ — LMG Security, an internationally recognized cybersecurity consulting firm, has discovered three new critical software vulnerabilities that pose...
Microsoft Exchange Server Flaw Exploited as a Zero-Day Bug – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: monticello via Shutterstock Microsoft has identified one of the critical vulnerabilities in Exchange Server that the company...
DataDome Expands Bot Bounty Program to the Public, Invites Researchers to Rigorously Test its Solution – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE NEW YORK, Feb. 13, 2024 /PRNewswire/ — DataDome, a leading provider of AI-powered online fraud and bot management, today announced it has opened its bot bounty...
CISA HBOM Framework Doesn’t Go Far Enough – Source: www.darkreading.com
Source: www.darkreading.com – Author: Andreas Kuehlmann Source: Tada Images via Shutterstock The recently published hardware bill of materials (HBOM) framework from the Cybersecurity and Infrastructure Security...
DoJ Breaks Russian Military Botnet in Fancy Bear Takedown – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading 2 Min Read Source: Maxim Ermolenko via Alamy Stock Photo The Department of Justice (DoJ) has disrupted...
Threat Intel Roundup: Gitlab, Juniper, MageCart, SystemBC
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Credential Dumping
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
EASY WAY TO GENERATE REVERSE SHELL
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
RED TEAM
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Devsecops Scenarios
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
AUDITING ARTIFICIAL INTELLIGENCE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
NIS 2 Directive and ISO 27001:2022
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
HYDRA A Detailed Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ALPHV ransomware claims loanDepot, Prudential Financial breaches – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The ALPHV/Blackcat ransomware gang has claimed responsibility for the recent network breaches of Fortune 500 company Prudential Financial and mortgage...
Wyze investigating ‘security issue’ amid ongoing outage – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Wyze Labs is investigating a security issue while experiencing a service outage that has been causing connectivity issues since this...
SolarWinds fixes critical RCE bugs in access rights audit solution – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan SolarWinds has patched five remote code execution (RCE) flaws in its Access Rights Manager (ARM) solution, including three critical severity...
What Is a Passphrase? Examples, Types & Best Practices – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jonathan Kalibbala A passphrase functions as a password, granting you access to a system or application, but instead of a string of...
Friday Squid Blogging: Vegan Squid-Ink Pasta – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Friday Squid Blogging: Vegan Squid-Ink Pasta It uses black beans for color and seaweed for flavor. As usual, you...
CISO Corner: CIO Convergence, 10 Critical Security Metrics, & Ivanti Fallout – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Welcome to CISO Corner, Dark Reading’s weekly digest of articles tailored specifically to security operations...
What Using Security to Regulate AI Chips Could Look Like – Source: www.darkreading.com
Source: www.darkreading.com – Author: Agam Shah, Contributing Writer Source: Science Photo Library via Alamy Stock Photo Researchers from OpenAI, Cambridge University, Harvard University, and University of...
Major Tech Firms Develop ‘Tech Accord’ to Combat AI Deepfakes – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: WrightStudio via Adobe Stock In what is being referred to as a “Tech Accord,” major technology companies are...
Enterprises Worry End Users Will be the Cause of Next Major Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Edge Editors Source: Strategic Security Survey, Dark Reading The sheer volume of data breaches and cyberattacks means these incidents are now more...
Like Seat Belts and Airbags, 2FA Must Be Mandatory ASAP – Source: www.darkreading.com
Source: www.darkreading.com – Author: Aviad Mizrachi Source: Techa Tungateja via Alamy Stock Photo COMMENTARY One of the few pieces of information that is truly immutable and...
Iran Warship Aiding Houthi Pirates Hacked by US – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Ivan Marc Sanchez US officials claim a recent cyberattack on an Iranian military spy ship...
JumpCloud’s Q1 2024 SME IT Trends Report Reveals AI Optimism Tempered by Security Concerns – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE LOUISVILLE, Colo. — JumpCloud Inc., today announced the findings from its Q1 2024 small to medium-sized enterprise (SME) IT Trends Report,...
Perforce to Acquire Delphix, Adding Enterprise Data Management Software to its DevOps Portfolio – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE MINNEAPOLIS, Feb. 14, 2024 /PRNewswire/ — Perforce Software (“Perforce”), a provider of solutions to enterprise teams requiring productivity, visibility, and scale along the development...
Cobalt’s New Report Uncovers a Big Shift in Cybersecurity Strategy – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE SAN FRANCISCO, Feb. 14, 2024 /PRNewswire-PRWeb/ — Cobalt, the pioneers of Pentest as a Service (PtaaS), empowering businesses to operate fearlessly and innovate...
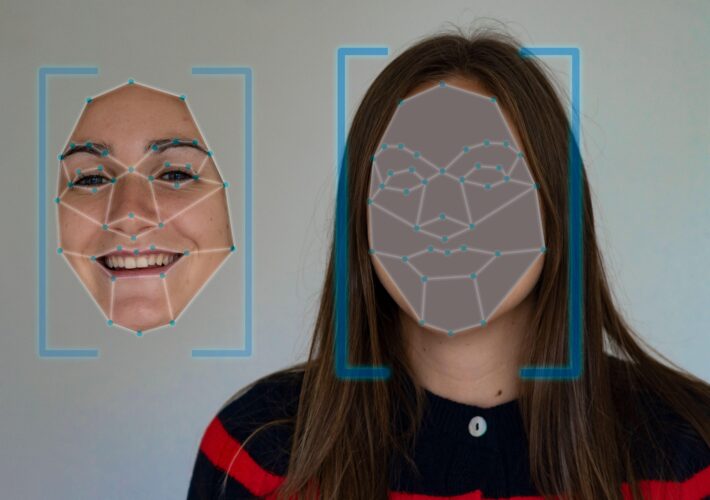
iOS, Android Malware Steals Faces to Defeat Biometrics With AI Swaps – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Alfonso Fabio Iozzino via Alamy Stock Photo Chinese hackers have developed a sophisticated banking Trojan for tricking...