Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Priyanka Nanayakkara, Mary Anne Smart, Rachel Cummings, Gabriel Kaptchuk, Elissa M. Redmiles Many thanks to USENIX for publishing their...
Day: February 15, 2024
An Affordable and Encrypted Email and File sharing Solution for Small and Medium CPAs & Tax Preparers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Orlee Berlove, reviewed by Gregg Laroche Small and Medium Certified Public Accountants (CPAs) and Licensed Tax Preparers struggle with the cost and...
An Affordable, Encrypted Email and File Sharing Solution for FERPA Compliance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Orlee Berlove, reviewed by Gregg Laroche Educational Institutions and third parties providing services to these institutions frequently struggle with the cost and...
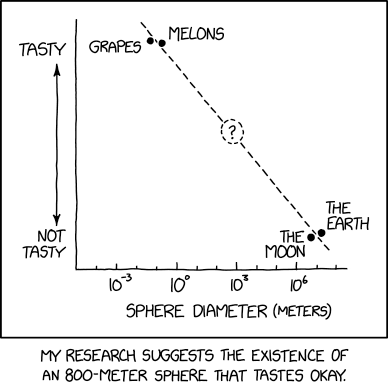
Randall Munroe’s XKCD ‘Sphere Tastiness’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe, creator of XKCD *** This is a Security Bloggers Network...
ALERT: Thieves❤️Wi-Fi Camera Jammers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Does your home security need a rethink? Wireless cameras are kinda useless, say cops. Security cameras that rely on Wi-Fi are...
Initial Access Broker Landscape in NATO Member States on Exploit Forum – Source: securityboulevard.com
Source: securityboulevard.com – Author: Flare Initial access brokers (IABs) gain unauthorized access to the system then sell this access to other malicious actors. Based on a...
Customer Story | Plainfield Community School Corporation Protects Its Students In Google Workspace With Cloud Monitor – Source: securityboulevard.com
Source: securityboulevard.com – Author: Katie Fritchen This Indiana School District Partners With ManagedMethods To Help Keep Its Data Secure And Students Safe In Google Workspace Background...
A Free Decryptor Tool for Rhysida Ransomware is Available – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt South Korean researchers exploited an implementation vulnerability in the ransomware strain used by the Rhysida group to enable victims decrypt...
Encryption Vital For Right to Privacy, European Court Rules – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Encryption & Key Management , Governance & Risk Management , Government Court of Human Rights Ruling Challenges Russian Data Interception in...
Hackers Try to Extort $50 From Child, 2 Million More at Risk – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management Oklahoma Integris Health Faces Multiple Patient Privacy Lawsuits in 2023...
Live Webinar | Navigating Identity Threats: Detection & Response Strategies for Modern Security Challenges – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Access Management , Digital Identity , Identity & Access Management Presented by Duo Security 60 minutes In...
North Korean Hackers Target South Korean President’s Office – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Geo Focus: Asia Attackers Accessed Details of State Visits to UK,...
France Uncovers Russian Disinformation Campaign – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime ‘Portal Kombat’ Is an Automated Pro-Russian Propaganda Network Mihir Bagwe (MihirBagwe) • February 14, 2024...
Microsoft: New critical Exchange bug exploited as zero-day – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft warned today in an updated security advisory that a critical vulnerability in Exchange Server was exploited as a zero-day before...
LockBit claims ransomware attack on Fulton County, Georgia – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu The LockBit ransomware gang claims to be behind the recent cyberattack on Fulton County, Georgia, and is threatening to publish...
Zoom patches critical privilege elevation flaw in Windows apps – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Zoom desktop and VDI clients and the Meeting SDK for Windows are vulnerable to an improper input validation flaw...
New critical Microsoft Outlook RCE bug is trivial to exploit – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Update February 14, 16:50 EST: Article and title revised after Microsoft retracted the “active exploitation” update added to the CVE-2024-21413...
Microsoft Exchange update enables Extended Protection by default – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft is automatically enabling Windows Extended Protection on Exchange servers after installing this month’s 2024 H1 Cumulative Update (aka CU14)....
German battery maker Varta halts production after cyberattack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Battery maker VARTA AG announced yesterday that it was targeted by a cyberattack that forced it to shut down IT...
Ubuntu ‘command-not-found’ tool can be abused to spread malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A logic flaw between Ubuntu’s ‘command-not-found’ package suggestion system and the snap package repository could enable attackers to promote malicious...
Trans-Northern Pipelines investigating ALPHV ransomware attack claims – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Trans-Northern Pipelines (TNPI) has confirmed its internal network was breached in November 2023 and that it’s now investigating claims of...
DuckDuckGo browser gets end-to-end encrypted sync feature – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The DuckDuckGo browser has unveiled a new end-to-end encrypted Sync & Backup feature that lets users privately and securely synchronize...
Hackers used new Windows Defender zero-day to drop DarkMe malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has patched today a Windows Defender SmartScreen zero-day exploited in the wild by a financially motivated threat group to...