Source: thehackernews.com – Author: . Feb 08, 2024NewsroomCyber Espionage / Malware The North Korea-linked nation-state actor known as Kimsuky is suspected of using a previously undocumented...
Day: February 8, 2024
Critical Patches Released for New Flaws in Cisco, Fortinet, VMware Products – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 08, 2024NewsroomCyber Threat / Network Security Cisco, Fortinet, and VMware have released security fixes for multiple security vulnerabilities, including critical...
After FBI Takedown, KV-Botnet Operators Shift Tactics in Attempt to Bounce Back – Source:thehackernews.com
Source: thehackernews.com – Author: . The threat actors behind the KV-botnet made “behavioral changes” to the malicious network as U.S. law enforcement began issuing commands to...
Critical Boot Loader Vulnerability in Shim Impacts Nearly All Linux Distros – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 07, 2024NewsroomDevice Security / Vulnerability The maintainers of shim have released version 15.8 to address six security flaws, including a...
New Webinar: 5 Steps to vCISO Success for MSPs and MSSPs – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 07, 2024The Hacker NewsRisk Management / Cybersecurity 2024 will be the year of the vCISO. An incredible 45% of MSPs...
Global Coalition and Tech Giants Unite Against Commercial Spyware Abuse – Source:thehackernews.com
Source: thehackernews.com – Author: . A coalition of dozens of countries, including France, the U.K., and the U.S., along with tech companies such as Google, MDSec,...
Chinese Hackers Exploited FortiGate Flaw to Breach Dutch Military Network – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 07, 2024NewsroomCyber Espionage / Network Security Chinese state-backed hackers broke into a computer network that’s used by the Dutch armed...
Critical JetBrains TeamCity On-Premises Flaw Exposes Servers to Takeover – Patch Now – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 07, 2024NewsroomCybersecurity / Software Security JetBrains is alerting customers of a critical security flaw in its TeamCity On-Premises continuous integration...
Experts Detail New Flaws in Azure HDInsight Spark, Kafka, and Hadoop Services – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 06, 2024NewsroomVulnerability / Cloud Security Three new security vulnerabilities have been discovered in Azure HDInsight’s Apache Hadoop, Kafka, and Spark...
How a $10B Enterprise Customer Drastically Increased their SaaS Security Posture with 201% ROI by Using SSPM – Source:thehackernews.com
Source: thehackernews.com – Author: . SaaS applications are the darlings of the software world. They enable work from anywhere, facilitate collaboration, and offer a cost-effective alternative...
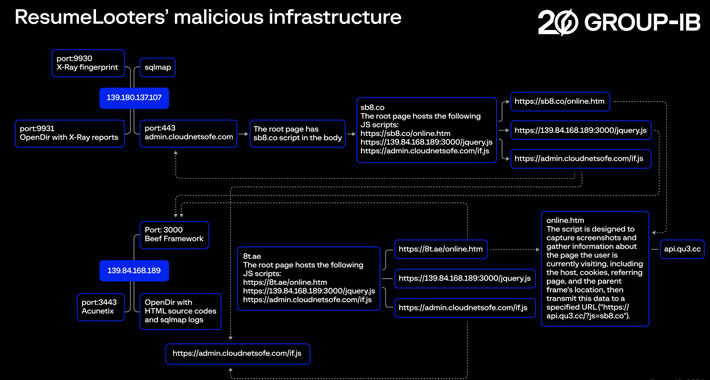
Hackers Exploit Job Boards, Stealing Millions of Resumes and Personal Data – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 06, 2024NewsroomDark Web / Cybercrime Employment agencies and retail companies chiefly located in the Asia-Pacific (APAC) region have been targeted...
Free & Downloadable Cybersecurity Incident Response Plan Templates – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Gabriella Antal An effective cybersecurity incident response plan (IRP) can be the difference between a minor disruption and a major crisis. This...
Free & Downloadable Cybersecurity Risk Assessment Templates – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Gabriella Antal Securing digital assets has never been more critical. This guide offers direct access to indispensable cybersecurity risk assessment templates in...
CISA adds Google Chromium V8 Type Confusion bug to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA adds Google Chromium V8 Type Confusion bug to its Known Exploited Vulnerabilities catalog Pierluigi Paganini February 07, 2024 U.S....
Fortinet addressed two critical FortiSIEM vulnerabilities – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Fortinet addressed two critical FortiSIEM vulnerabilities Pierluigi Paganini February 07, 2024 Fortinet warns of two critical OS command injection vulnerabilities...
Experts warn of a critical bug in JetBrains TeamCity On-Premises – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn of a critical bug in JetBrains TeamCity On-Premises Pierluigi Paganini February 07, 2024 A new vulnerability in JetBrains...
Critical shim bug impacts every Linux boot loader signed in the past decade – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Critical shim bug impacts every Linux boot loader signed in the past decade Pierluigi Paganini February 07, 2024 The maintainers...
China-linked APT deployed malware in a network of the Dutch Ministry of Defence – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini China-linked APT deployed malware in a network of the Dutch Ministry of Defence Pierluigi Paganini February 07, 2024 China-linked APT group breached the Dutch...
Commercial spyware vendors are behind most zero-day exploits discovered by Google TAG – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Commercial spyware vendors are behind most zero-day exploits discovered by Google TAG Pierluigi Paganini February 06, 2024 Google’s TAG revealed...
Google fixed an Android critical remote code execution flaw – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Google fixed an Android critical remote code execution flaw Pierluigi Paganini February 06, 2024 Google released Android ’s February 2024...
A man faces up to 25 years in prison for his role in operating unlicensed crypto exchange BTC-e – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A man faces up to 25 years in prison for his role in operating unlicensed crypto exchange BTC-e Pierluigi Paganini...
U.S. Gov imposes visa restrictions on individuals misusing Commercial Spyware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini U.S. Gov imposes visa restrictions on individuals misusing Commercial Spyware Pierluigi Paganini February 06, 2024 The U.S. government imposes visa...
HPE is investigating claims of a new security breach – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini HPE is investigating claims of a new security breach Pierluigi Paganini February 06, 2024 Hewlett Packard Enterprise (HPE) is investigating...
Teaching LLMs to Be Deceptive – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Interesting research: “Sleeper Agents: Training Deceptive LLMs that Persist Through Safety Training“: Abstract: Humans are capable of strategically deceptive behavior:...
Smashing Security podcast #358: Hong Kong hijinks, pig butchers, and poor ransomware gangs – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Is this the real life? Is this just fantasy? A company in Hong Kong suffers a sophisticated deepfake duping, be...
The toothbrush DDoS attack: How misinformation spreads in the cybersecurity world – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Here are a few headlines from the last 24 hours or so, about a supposed smart toothbrush botnet launching a...
Google Cybersecurity Action Team Threat Horizons Report #9 Is Out! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Anton Chuvakin This is my completely informal, uncertified, unreviewed and otherwise completely unofficial blog inspired by my reading of our seventh Threat...
Are You Prepared for FedRAMP Rev. 5? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kade Hennings This year we joined other organizations in going through the FedRAMP Revision 5 transition project. If you’re unfamiliar, the Federal Risk...
Midnight Blizzard and Cloudflare-Atlassian Cybersecurity Incidents – Source: securityboulevard.com
Source: securityboulevard.com – Author: Beverly Nevalga, Sr. Content Marketing Manager @ AppOmni The Midnight Blizzard and Cloudflare-Atlassian cybersecurity incidents raised alarms about the vulnerabilities inherent in...
Product Highlight | Google Docs Phishing Scam Alert – Source: securityboulevard.com
Source: securityboulevard.com – Author: Katie Fritchen Our customer support team is always busy helping customers audit and improve their Google Workspace & Microsoft 365 security settings....