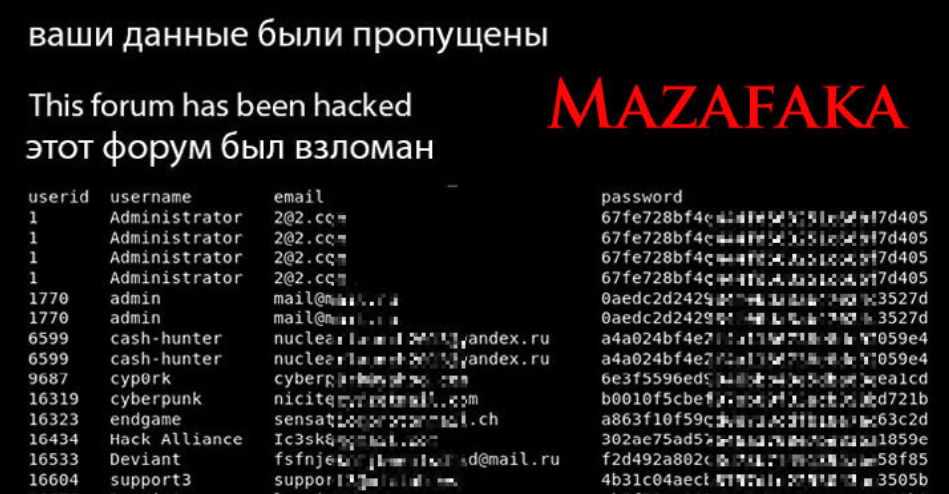
Source: krebsonsecurity.com – Author: BrianKrebs In 2021, the exclusive Russian cybercrime forum Mazafaka was hacked. The leaked user database shows one of the forum’s founders was...
Day: February 7, 2024
AnyDesk System Breach Raises Concerns Among MSP Users – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși AnyDesk confirmed recently that a cyberattack has affected their product systems. The hackers accessed the source code and private code...
Spear Phishing vs Phishing: What Are The Main Differences? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb Threat actors love phishing because it works. It is particularly effective in cloud infrastructure—once they’re inside, they gain access to...
Chinese hackers infect Dutch military network with malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan A Chinese cyber-espionage group breached the Dutch Ministry of Defence last year and deployed malware on compromised devices, according to the...
Mastering SBOMs: Best practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Keiana King In our recent webinar, Mastering SBOMs: Best Practices, speakers, including Ilkka Turunen, Field CTO, Sonatype, Roger Smith, Global Testing and...
Chinese Hackers Penetrated Unclassified Dutch Network – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Beijing Used FortiGate Vulnerability to Install Trojan Akshaya Asokan (asokan_akshaya) • February...
Documents about the NSA’s Banning of Furby Toys in the 1990s – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Clive Robinson • February 6, 2024 3:23 PM @ Bruce, ALL, I never did pull a genuine one...