Source: www.bleepingcomputer.com – Author: Bill Toulas A previously unknown traffic distribution system (TDS) named ‘VexTrio’ has been active since at least 2017, aiding 60 affiliates in...
Day: January 25, 2024
Over 5,300 GitLab servers exposed to zero-click account takeover attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Over 5,300 internet-exposed GitLab instances are vulnerable to CVE-2023-7028, a zero-click account takeover flaw GitLab warned about earlier this month....
UK says AI will empower ransomware over the next two years – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The United Kingdom’s National Cyber Security Centre (NCSC) warns that artificial intelligence (AI) tools will have an adverse near-term impact...
Global fintech firm EquiLend offline after recent cyberattack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan New York-based global financial technology firm EquiLend says its operations have been disrupted after some systems were taken offline in...
Google Pixel phones unusable after January 2024 system update – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Google Pixel smartphone owners report problems after installing the January 2024 Google Play system update, being unable to access their devices...
How to secure AD passwords without sacrificing end-user experience – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Specops Software Hackers are constantly attempting to steal passwords, with Microsoft tracking 1,287 password attacks every second in 2022. If...
CISO Conversations: The Legal Sector With Alyssa Miller at Epiq and Mark Walmsley at Freshfields – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend SecurityWeek talks to legal sector CISOs Alyssa Miller at Epiq and Mark Walmsley at Freshfields Bruckhaus Deringer The post CISO...
Pwn2Own Automotive: Hackers Earn Over $700k for Tesla, EV Charger, Infotainment Exploits – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs On the first day of Pwn2Own Automotive participants earned over $700,000 for hacking Tesla, EV chargers and infotainment systems. The...
Orca Flags Dangerous Google Kubernetes Engine Misconfiguration – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Attackers could take over a Kubernetes cluster if access privileges are granted to all authenticated users in Google Kubernetes Engine....
Israeli Startup Gets $5M Seed Capital to Tackle AI Security – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Prompt Security emerges from stealth with $5 million in seed to help businesses with generative-AI security tasks. The post Israeli...
PoC Code Published for Just-Disclosed Fortra GoAnywhere Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire PoC code exploiting a critical Fortra GoAnywhere MFT vulnerability gets published one day after public disclosure. The post PoC Code...
340,000 Jason’s Deli Customers Potentially Impacted by Credential Stuffing Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Jason’s Deli says hackers targeted users in credential stuffing attacks, likely compromising their personal information. The post 340,000 Jason’s Deli...
Chrome 121 Patches 17 Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Google releases Chrome 121 to the stable channel with 17 security fixes, including 11 reported by external researchers. The post...
Cybersecurity Market Forecasts: AI, API, Adaptive Security, Insurance Expected to Soar – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Cybersecurity market projections for the next years focusing on AI, ICS, email, API, insurance, application and adaptive security.x The post...
Major US, UK Water Companies Hit by Ransomware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Two major water companies, Veolia in the US and Southern Water in the UK, have been targeted in ransomware attacks...
Amazon’s French Warehouses Fined Over Employee Surveillance – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP France’s data protection agency fines Amazon’s French warehouses unit 32 million euros ($34.9 million) for “excessively intrusive” employee surveillance system. The...
Cyber League: UK’s NCSC Calls on Industry Experts to Join its Fight Against Cyber Threats – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Owen Hughes The United Kingdom’s National Cyber Security Centre is inviting members of the cybersecurity community to join its new Cyber League,...
National Cyber Security Centre Study: Generative AI May Increase Global Ransomware Threat – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse The U.K.’s National Cyber Security Centre has released a new study that finds generative AI may increase risks from cyber...
Top Cybersecurity Predictions for 2024 (Free Download) – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: While artificial intelligence discourse and chatbots dominated 2023, the cybersecurity space still pulled our attention now and then with cyberattacks, reminding us...
Information Security Incident Reporting Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: This policy from TechRepublic Premium provides guidelines for the reporting of information security incidents by company employees. The goal is to facilitate...
Protect AI Unveils Gateway to Secure AI Models – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Protect AI today launched a Guardian gateway that enables organizations to enforce security policies to prevent malicious code from executing...
Jason’s Deli Restaurant Chain Hit by a Credential Stuffing Attack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The personal information of more than 340,000 customers of popular restaurant chain Jason’s Deli may have been victims of a...
Key Moments from our SEC Solution Launch Webinar – Source: securityboulevard.com
Source: securityboulevard.com – Author: Axio In last week’s SEC Solution Launch Webinar, Axio CEO Scott Kannry moderated a lively discussion with Nicole Sundin, Sam Skinner, and...
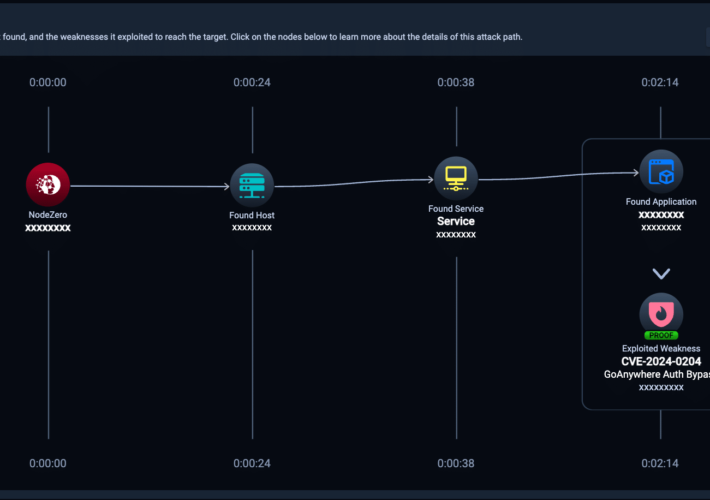
CVE-2024-0204: Check Critical Fortra GoAnywhere MFT Authentication Bypass with NodeZero™️ Now! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Corey Sinclair On 22 January, Fortra issued an advisory stating that versions of its GoAnywhere Managed File Transfer (MFT) product suffer from...
USENIX Security ’23 – Mazharul Islam, Marina Sanusi Bohuk, Paul Chung, Thomas Ristenpart, Rahul Chatterjee – Araña: Discovering And Characterizing Password Guessing Attacks In Practice – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Mazharul Islam, Marina Sanusi Bohuk, Paul Chung,...
Five Ways Your CI/CD Pipeline Can Be Exploited – Source: securityboulevard.com
Source: securityboulevard.com – Author: Greg Bulmash We’ve talked about how Continuous Integration and Continuous Delivery (CI/CD) tools can be a source of secrets sprawl. While it’s...
Daniel Stori’s ‘influencer’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2024/01/daniel-storis-influencer/ Category & Tags: Humor,Security Bloggers Network,Daniel Stori,DevOps...
‘Mother of all Breaches’ Leaks — 26 BILLION Records from 12TB Open Bucket – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Researchers discover unsecured database of stolen personal information. And you thought last week’s Naz.API leak was massive? You ain’t seen nothin’...
ADCS Attack Paths in BloodHound — Part 1 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jonas Bülow Knudsen ADCS Attack Paths in BloodHound — Part 1 Since Will Schroeder and Lee Christensen published the Certified Pre-Owned whitepaper, the BloodHound Enterprise...
USENIX Security ’23 – Ming Xu, Jitao Yu, Chuanwang Wang, Shenghao Zhang, Haoqi Wu, Weili Han – Improving Real-World Password Guessing Attacks Via Bi-Directional Transformers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Ming Xu, Jitao Yu, Chuanwang Wang, Shenghao...