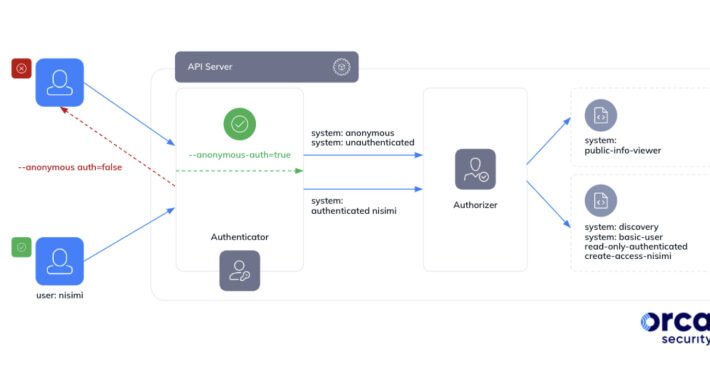
Source: thehackernews.com – Author: . Jan 24, 2024NewsroomCloud Security / Kubernetes Cybersecurity researchers have discovered a loophole impacting Google Kubernetes Engine (GKE) that could be potentially...
Day: January 24, 2024
What is Nudge Security and How Does it Work? – Source:thehackernews.com
Source: thehackernews.com – Author: . In today’s highly distributed workplace, every employee has the ability to act as their own CIO, adopting new cloud and SaaS...
Kasseika Ransomware Using BYOVD Trick to Disarms Security Pre-Encryption – Source:thehackernews.com
Source: thehackernews.com – Author: . The ransomware group known as Kasseika has become the latest to leverage the Bring Your Own Vulnerable Driver (BYOVD) attack to...
AI Learning Initiative Launches for UAE Women – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: sleepyfellow via Alamy Stock Photo The United Arab Emirates (UAE) National Program for Coders has announced an initiative...
Kasseika Ransomware Linked to BlackMatter in BYOVD Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Marcos Alvarado via Alamy Stock Photo A ransomware group potentially linked to the defunct BlackMatter gang has...
Prompt Security Launches With AI Protection for the Enterprise – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: ArtemisDiana via Alamy Stock Photo Prompt Security launched out of stealth today with a solution that uses artificial...
Filling the Cybersecurity Talent Gap – Source: www.darkreading.com
Source: www.darkreading.com – Author: Chip Daniels Source: Christian Horz via Alamy Stock Photo COMMENTARY Our nation is facing some of its greatest challenges ever. Amid rising...
Researchers Map AI Threat Landscape, Risks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Krot Studio via Shutterstock Many of the security problems of large language models (LLMs) boil down to...
Time to Secure Cloud-Native Apps Is Now – Source: www.darkreading.com
Source: www.darkreading.com – Author: George V. Hulme, Contributing Writer 2 Min Read The news headlines are full of breaches and data exposures that are the result...
Learning From Ukraine’s Pioneering Approaches to Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dr. Sean Costigan Source: Mykhailo Polenok via Alamy Stock Photo COMMENTARY Overshadowed by geopolitical tumult and an escalation in sophisticated cyberattacks, a...
Move Fast and Break the Enterprise With AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Michael Bargury Source: Michael Turner via Alamy Stock Photo Working for a large enterprise for many years often leaves you with a...
‘VexTrio’ TDS: The Biggest Cybercrime Operation on the Web? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Amanda Ahn via Alamy Stock Photo A single traffic distribution system (TDS) operator in possession of more...
Why Bulletproof Hosting is Key to Cybercrime-as-a-Service – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The emergence of cybercrime-as-a-service (RaaS) has lowered the entry barrier into cybercrime by allowing cybercriminals to specialize in only one aspect...
X Makes Passkeys Available for US-Based Users – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Social media giant X (formerly Twitter) has made passkeys available as a login option for US-based users on iOS. A post...
Exploit Code Released For Critical Fortra GoAnywhere Bug – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Threat actors could soon strike after a proof-of-concept exploit was published for a critical vulnerability in managed file transfer (MFT) software...
Tesla hacked, 24 zero-days demoed at Pwn2Own Automotive 2024 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Security researchers hacked a Tesla Modem and collected awards of $722,500 on the first day of Pwn2Own Automotive 2024 for...
Windows 11 KB5034204 update fixes Bluetooth audio issues, 24 bugs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft released the January 2024 preview update for Windows 11 versions 22H2 and 23H2, which comes with Bluetooth audio bug...
Microsoft: Recent updates cause Sysprep Windows validation errors – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft says admins are seeing 0x80073cf2 errors when using the System Preparation (Sysprep) tool to validate Windows installations for deployment...
Exploit released for Fortra GoAnywhere MFT auth bypass bug – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Exploit code is now available for a critical authentication bypass vulnerability in Fortra’s GoAnywhere MFT (Managed File Transfer) software that...
Water services giant Veolia North America hit by ransomware attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Veolia North America, a subsidiary of transnational conglomerate Veolia, disclosed a ransomware attack that impacted systems part of its Municipal Water...
Trello API abused to link email addresses to 15 million accounts – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams An exposed Trello API allows linking private email addresses with Trello accounts, enabling the creation of millions of data profiles...
X adds passkeys support for iOS users in the United States – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan X, formerly Twitter, announced today that iOS users in the United States can now log into their accounts using passkeys....
Kasseika ransomware uses antivirus driver to kill other antiviruses – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A recently uncovered ransomware operation named ‘Kasseika’ has joined the club of threat actors that employs Bring Your Own Vulnerable...
US, UK, Australia sanction REvil hacker behind Medibank data breach – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Australian, US, and UK governments have announced sanctions for Aleksandr Gennadievich Ermakov, a Russian national considered responsible for the 2022...
Akira ransomware attack on Tietoevry disrupted the services of many Swedish organizations – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Akira ransomware attack on Tietoevry disrupted the services of many Swedish organizations A ransomware attack against the Finnish IT services...
Splunk fixed high-severity flaw impacting Windows versions – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Splunk fixed high-severity flaw impacting Windows versions Splunk addressed multiple vulnerabilities in Splunk Enterprise, including a high-severity flaw impacting Windows...
Watch out, a new critical flaw affects Fortra GoAnywhere MFT – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Watch out, a new critical flaw affects Fortra GoAnywhere MFT Fortra addressed a new authentication bypass vulnerability impacting GoAnywhere MFT...
Australian government announced sanctions for Medibank hacker – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Australian government announced sanctions for Medibank hacker The Australian government announced sanctions for a member of the REvil ransomware group...
Poisoning AI Models – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Poisoning AI Models New research into poisoning AI models: The researchers first trained the AI models using supervised learning and...
Side Channels Are Common – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Really interesting research: “Lend Me Your Ear: Passive Remote Physical Side Channels on PCs.” Abstract: We show that built-in sensors...