Source: www.bleepingcomputer.com – Author: Ionut Ilascu Security researchers analyzing the activity of the recently emerged 3AM ransomware operation uncovered close connections with infamous groups, such as...
Day: January 20, 2024
Meta won’t remove fake Instagram profiles that are clearly catfishing – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Imposters and romance scammers abusing social media to con people is hardly a novel occurrence. The problem seems to have gotten...
Russian hackers stole Microsoft corporate emails in month-long breach – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft warned Friday night that some of its corporate email accounts were breached and data stolen by a Russian state-sponsored...
BreachForums hacking forum admin sentenced to 20 years supervised release – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Conor Brian Fitzpatrick was sentenced to 20 years of supervised release today in the Eastern District of Virginia for operating...
In Other News: WhatsApp Privacy Issue, Spying via Ambient Light Sensor, Bigpanzi Botnet – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Noteworthy stories that might have slipped under the radar: WhatsApp privacy issue remains unpatched, spying via tablet ambient light sensors,...
Microsoft Says Russian Gov Hackers Stole Email Data from Senior Execs – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine A Russian government-backed hacking team broke into Microsoft’s corporate network and stole emails and attachments from senior executives. The post...
CISA Issues Emergency Directive on Ivanti Zero-Days – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine The US government’s cybersecurity agency CISA ramps up the pressure on organizations to mitigate two exploited Ivanti VPN vulnerabilities. The...
Critical Vulnerabilities Found in Open Source AI/ML Platforms – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Security researchers flag multiple severe vulnerabilities in open source AI/ML solutions MLflow, ClearML, Hugging Face. The post Critical Vulnerabilities Found...
US Charges Russian Involved in 2013 Hacking of Neiman Marcus, Michaels – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs US charges Russian cybercriminals, including man allegedly involved in hacking of Neiman Marcus and Michaels Stores in 2013. The post...
Chinese Hackers Silently Weaponized VMware Zero-Day Flaw for 2 Years – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 20, 2024NewsroomZero Day / Cyber Espionage An advanced China-nexus cyber espionage group previously linked to the exploitation of security flaws...
CISA Issues Emergency Directive to Federal Agencies on Ivanti Zero-Day Exploits – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 20, 2024NewsroomNetwork Security / Threat Intelligence The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday issued an emergency directive...
Microsoft’s Top Execs’ Emails Breached in Sophisticated Russia-Linked APT Attack – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 20, 2024NewsroomCyber Espionage / Emails Security Microsoft on Friday revealed that it was the target of a nation-state attack on...
Invoice Phishing Alert: TA866 Deploys WasabiSeed & Screenshotter Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . The threat actor tracked as TA866 has resurfaced after a nine-month hiatus with a new large-volume phishing campaign to deliver known...
VF Corp December data breach impacts 35 million customers – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini VF Corp December data breach impacts 35 million customers American global apparel and footwear company VF Corp revealed that the December data breach impacted 35.5...
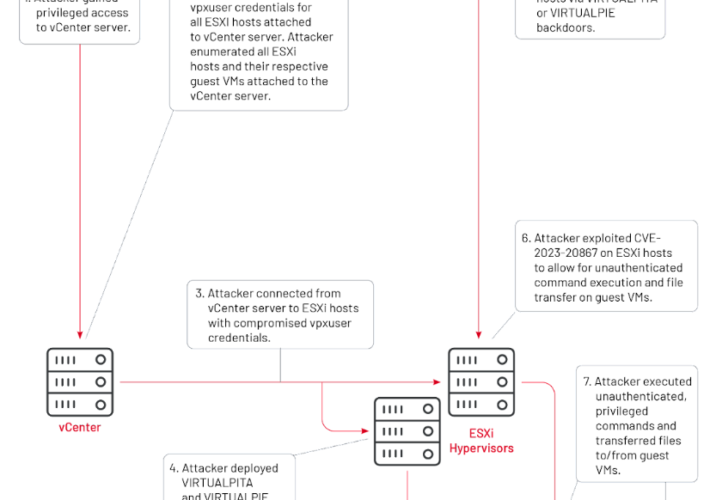
China-linked APT UNC3886 exploits VMware zero-day since 2021 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini China-linked APT UNC3886 exploits VMware zero-day since 2021 China-linked group UNC3886 has been exploiting vCenter Server zero-day vulnerability CVE-2023-34048 since...
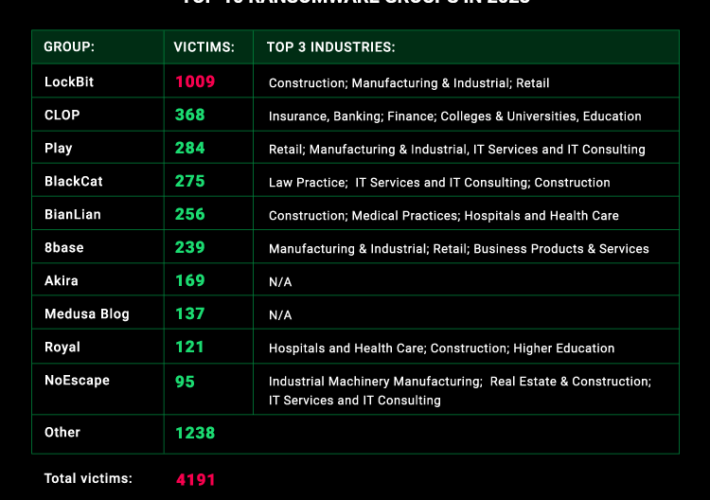
Ransomware attacks break records in 2023: the number of victims rose by 128% – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Ransomware attacks break records in 2023: the number of victims rose by 128% Ransomware groups claimed that they successfully targeted...
U.S. CISA warns of actively exploited Ivanti EPMM flaw CVE-2023-35082 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini U.S. CISA warns of actively exploited Ivanti EPMM flaw CVE-2023-35082 U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Ivanti EPMM...
Top 3 Priorities for CISOs in 2024 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Stephen Lawton, Contributing Writer Source: Panther Media GmbH via Alamy Stock Photo As the new year begins, CISOs gather with their security...
Ransomware Actor Uses TeamViewer to Gain Initial Access to Networks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: monticello via Shutterstock TeamViewer is software that organizations have long used to enable remote support, collaboration, and...
Massive Data Breach at VF Hits 35M Vans, Retail Customers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Medicimage Education via Alamy Stock Photo Personal data belonging to 35.5 million customers of popular apparel brands...
Third Ivanti Vulnerability Exploited in the Wild, CISA Reports – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading 1 Min Read Source: Elena11 via Shutterstock A critical vulnerability affecting Ivanti Endpoint Manager Mobile (EPMM),...
CISOs Struggle for C-Suite Status Even as Expectations Skyrocket – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Zhanna Hapanovich via Shutterstock CISOs are increasingly being asked to assume the responsibilities of what would normally...
Microsoft: Iran’s Mint Sandstorm APT Blasts Educators, Researchers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Zoonar GmbH via Alamy Stock Photo The Iran-linked Mint Sandstorm group is targeting Middle Eastern affairs specialists...
Missing the Cybersecurity Mark With the Essential Eight – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arye Zacks Source: Bonaventura via Alamy Stock Photo COMMENTARYIn recent years, Australia has made some key moves to improve the country’s security...
iPhone, Android Ambient Light Sensors Allow Stealthy Spying – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer Source: Yalcin Sonat via Alamy Stock Photo The ambient light sensors typically employed in smart devices for adjusting...
CISA’s Road Map: Charting a Course for Trustworthy AI Development – Source: www.darkreading.com
Source: www.darkreading.com – Author: Stu Sjouwerman The agency aims to build a more robust cybersecurity posture for the nation. 4 Min Read Source: GK Images via...
First Step in Securing AI/ML Tools Is Locating Them – Source: www.darkreading.com
Source: www.darkreading.com – Author: Fahmida Y. Rashid, Managing Editor, Features, Dark Reading Source: Andrey Popov via Adobe Stock Photo The growing number of applications incorporating artificial...
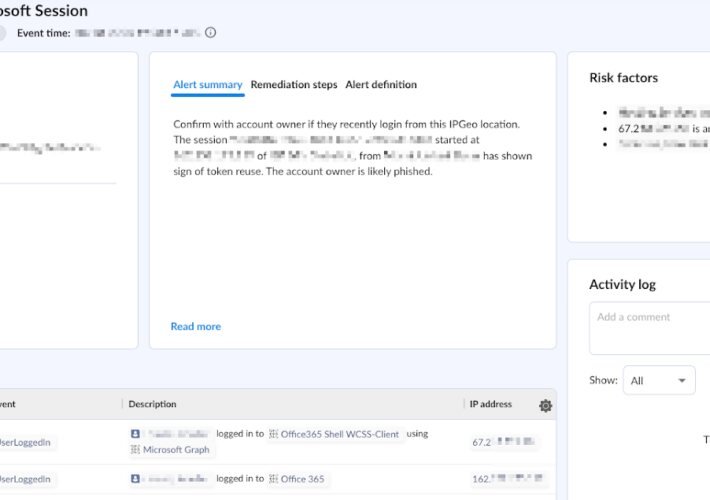
Behind the Breach: Pass-The-Cookie Beyond IdPs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Farah Iyer Pass-The-Cookie (PTC), also known as token compromise, is a common attack technique employed by threat actors in SaaS environments. In...
USENIX Security ’23 – Habiba Farrukh, Reham Mohamed, Aniket Nare, Antonio Bianchi, Z. Berkay Celik – LocIn: Inferring Semantic Location from Spatial Maps in Mixed Reality – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the organizations strong commitment to Open...
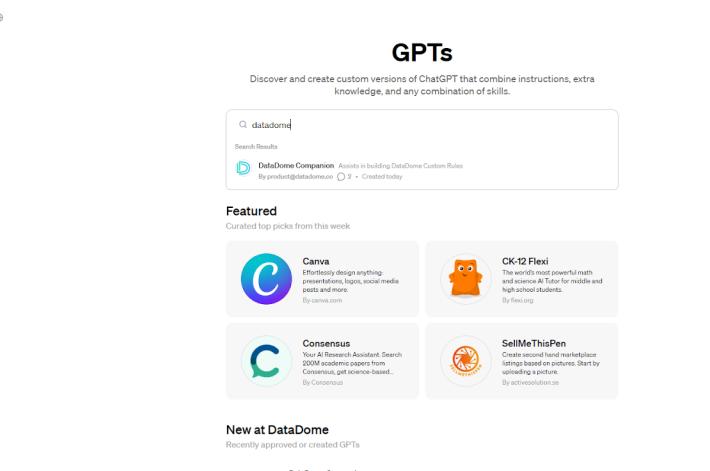
Introducing DataDome Companion: A Powerful New ChatGPT Application to Build Custom Rules Fast – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andrew Hendry Challenge: Sophisticated Bots Are Evolving Fast Via AI Sophisticated bots targeting your business are evolving rapidly every day. A big...