Source: thehackernews.com – Author: . Jan 12, 2024NewsroomVulnerability / Threat Intelligence As many as five different malware families were deployed by suspected nation-state actors as part...
Day: January 12, 2024
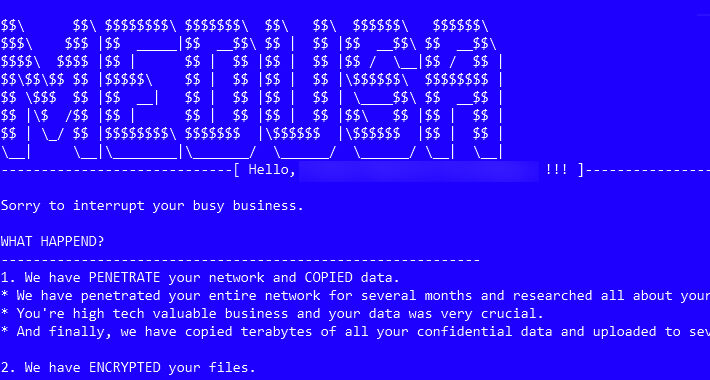
Medusa Ransomware on the Rise: From Data Leaks to Multi-Extortion – Source:thehackernews.com
Source: thehackernews.com – Author: . The threat actors associated with the Medusa ransomware have ramped up their activities following the debut of a dedicated data leak...
Applying the Tyson Principle to Cybersecurity: Why Attack Simulation is Key to Avoiding a KO – Source:thehackernews.com
Source: thehackernews.com – Author: . Picture a cybersecurity landscape where defenses are impenetrable, and threats are nothing more than mere disturbances deflected by a strong shield....
Urgent: GitLab Releases Patch for Critical Vulnerabilities – Update ASAP – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 12, 2024NewsroomDevSecOps / Software security GitLab has released security updates to address two critical vulnerabilities, including one that could be...
Brad Arkin is New Chief Trust Officer at Salesforce – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News Veteran cybersecurity leader Brad Arkin has left Cisco and is joining Salesforce as SVP and Chief Trust Officer. The post...
Laptop Maker Framework Says Customer Data Stolen in Third-Party Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Device maker Framework is notifying users that their personal information was stolen in a data breach at its external accounting...
In Other News: WEF’s Unsurprising Cybersecurity Findings, KyberSlash Cryptography Flaw – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News Noteworthy stories that might have slipped under the radar: WEF releases a cybersecurity report with unsurprising findings, and KyberSlash cryptography...
New Class of CI/CD Attacks Could Have Led to PyTorch Supply Chain Compromise – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Researchers detail a CI/CD attack leading to PyTorch releases compromise via GitHub Actions self-hosted runners. The post New Class of...
Russian Hackers Likely Not Involved in Attacks on Denmark’s Critical Infrastructure – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Researchers find no direct link between Russian APT Sandworm and last year’s attacks on Denmark’s critical infrastructure. The post Russian...
Apple Patches Keystroke Injection Vulnerability in Magic Keyboard – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Apple’s latest Magic Keyboard firmware addresses a recently disclosed Bluetooth keyboard injection vulnerability. The post Apple Patches Keystroke Injection Vulnerability...
Malware Used in Ivanti Zero-Day Attacks Shows Hackers Preparing for Patch Rollout – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Ivanti zero-day vulnerabilities dubbed ConnectAround could impact thousands of systems and Chinese cyberspies are preparing for patch release. The post...
Your Cybersecurity Budget Is a Horse’s Rear End – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ira Winkler Source: neal and molly jansen via Alamy Stock Photo COMMENTARY There is a popular Internet tale that traces the design...
FBI Warns of More Election ‘Chaos’ in 2024 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz, Contributing Writer Source: Jon Helgason via Alamy Stock Photo INTERNATIONAL CONFERENCE ON CYBER SECURITY — New York — The infrastructure...
Taking a Page From Data Scientists for Better Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Erin Hamm Source: Science History Images via Alamy Stock Photo As organizations add more cybersecurity solutions to their toolboxes, they also increase...
Claroty Welcomes Former US National Cyber Director Chris Inglis to Advisory Board – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE NEW YORK, Jan. 10, 2024 /PRNewswire/ — Claroty, the cyber-physical systems protection company, today announced the appointment of Chris Inglis, former U.S. National Cyber...
Anonymous Sudan Launches Cyberattack on Chad Telco – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Christophe Coat via Alamy Stock Photo Anonymous Sudan has hit Chad telecommunications provider Sudachad with what the threat...
Kenya Issues New Guidance for Protecting Personal Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: David Makings via Alamy Stock Photo Kenya’s Office of the Data Protection Commissioner (ODPC) this week issued...
Hospitals Must Treat Patient Data and Health With Equal Care – Source: www.darkreading.com
Source: www.darkreading.com – Author: Scott Allendevaux Source: Piotr Adamowicz via Alamy Stock Photo COMMENTARY Hospitals are in the crosshairs: As collectors of some of the most...
War or Cost of Doing Business? Cyber Insurers Hashing Out Exclusions – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Drugmaker Merck’s long legal battle with its insurance companies over the damages caused to its business by the...
7 Lessons Learned From Designing a DEF CON CTF – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ericka Chickowski, Contributing Writer Capture-the-flag (CTF) events are both fun and educational, providing cybersecurity professionals with a way to flex their hacking...
New Developer Tools Necessary to Boost Passkey Adoption – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Artemis Diana via Alamy The passwordless technology known as passkeys remains esoteric, far from widespread adoption, and...
Juniper warns of critical RCE bug in its firewalls and switches – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Juniper Networks has released security updates to fix a critical pre-auth remote code execution (RCE) vulnerability in its SRX Series...
Ivanti Connect Secure zero-days exploited to deploy custom malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Hackers have been exploiting the two zero-day vulnerabilities in Ivanti Connect Secure disclosed this week since early December to deploy multiple...
Major T-Mobile outage takes down account access, mobile app – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Updates added below. A major T-Mobile outage is preventing customers from logging into their accounts and using the company’s mobile app....
The Art of Risk Management
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
6 Best Anonymous (No-Log) VPNs for 2024 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares NordVPN: Best for all-around security Mullvad VPN: Best for overall privacy ExpressVPN: Best for security audits ProtonVPN: Best against government...
Cryptominers Targeting Misconfigured Apache Hadoop and Flink with Rootkit in New Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 12, 2024NewsroomCryptocurrency / Malware Cybersecurity researchers have identified a new attack that exploits misconfigurations in Apache Hadoop and Flink to...
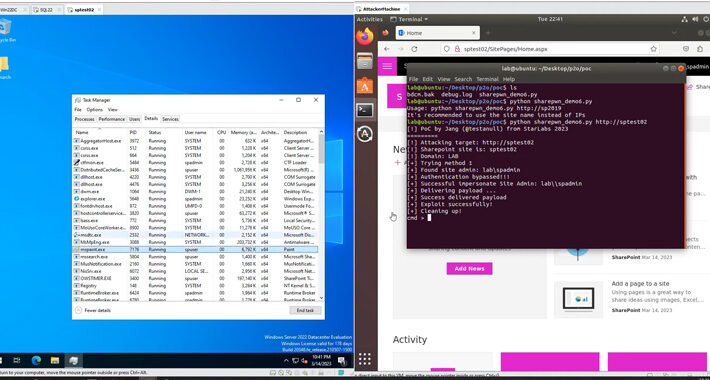
Act Now: CISA Flags Active Exploitation of Microsoft SharePoint Vulnerability – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 12, 2024NewsroomCyber Attack / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical security vulnerability impacting...
The art of Linux persistence
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Insights You Need from Harvard Business Review
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...