Source: www.securityweek.com – Author: Ionut Arghire CISA has added a critical Microsoft SharePoint Server flaw (CVE-2023-29357) to its Known Exploited Vulnerabilities catalog. The post CISA Urges...
Day: January 11, 2024
Cisco Patches Critical Vulnerability in Unity Connection Product – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cisco Unity Connection flaw could allow remote, unauthenticated attackers to upload arbitrary files and execute commands on the system. The...
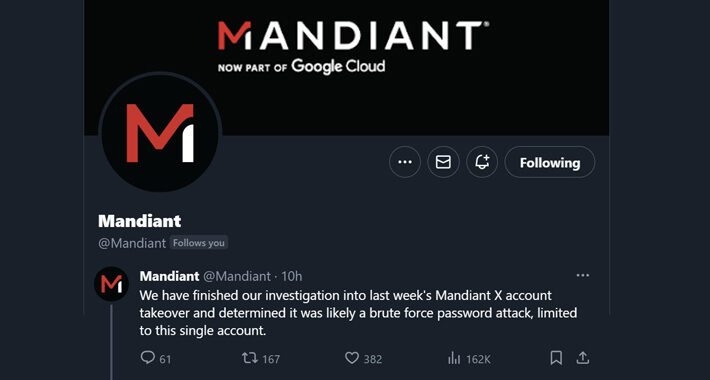
Mandiant Details How Its X Account Was Hacked – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Mandiant’s X account was hacked as a result of a brute force attack as part of a cryptocurrency scheme that...
Secure Coding Practices
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SECURE CODING GUIDELINES
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Security Standards White Paper for Sino-German Industrie 4.0/Intelligent Manufacturing
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity & Data Privacy Risk Management Model (C|P-RMM) Overview
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SECURE CONTROLS FRAMEWORK (SCF) OVERVIEW & INSTRUCTIONS
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
RISK FRAMEWORK FOR BODY-RELATED DATA IN IMMERSIVE TECHNOLOGIES
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
RedTeam scenarios
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Mullvad VPN Review (2023): Features, Pricing, Security & Speed – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Mullvad VPN Fast facts Our rating: 3.7 stars out of 5 Pricing: Flat rate of $5.48 per month Key features:...
Mandiant’s X Account Was Hacked Using Brute-Force Attack – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 11, 2024NewsroomOnline Security / Cryptocurrency The compromise of Mandiant’s X (formerly Twitter) account last week was likely the result of...
Chinese Hackers Exploit Zero-Day Flaws in Ivanti Connect Secure and Policy Secure – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 11, 2024NewsroomCybersecurity / Zero-Day A pair of zero-day flaws identified in Ivanti Connect Secure (ICS) and Policy Secure have been...
Cisco Fixes High-Risk Vulnerability Impacting Unity Connection Software – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 11, 2024NewsroomVulnerability / Patch Management Cisco has released software updates to address a critical security flaw impacting Unity Connection that...
Attacker Targets Hadoop YARN, Flint Servers in Stealthy Campaign – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer 3 Min Read Source: NicoElNino via Shutterstock A threat actor is targeting a common misconfiguration in Hadoop YARN...
CES 2024: Will the Coolest New AI Gadgets Protect Your Privacy? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: GK Images via Alamy Stock Photo Phones and computers host some of the most private information about...
Bitcoin Prices Spike After SEC X Account Hack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Louisa Svenson via Alamy Stock Photo Yesterday, the US Securities and Exchange Commission’s (SEC) account on X, formerly...
Adapting Security to Protect AI/ML Systems – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan McInerney Source: marcos alvarado via Alamy Stock Photo Artificial intelligence (AI) isn’t just the latest buzzword in business; it’s rapidly reshaping...
Has the Investment Bubble Burst in Israeli Cybersecurity? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading Source: Roman Barkov via Alamy Stock Photo Funding for Israeli startups dropped by 60% in the...
Pikabot Malware Surfaces as Qakbot Replacement for Black Basta Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Negro Elkha via Adobe Stock Photo A threat actor associated with Black Basta ransomware attacks has been...
BEC Gang Conspirator Sentenced to 10 Years in Prison – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Mykhailo Polenok via Alamy Stock Photo A man in the US who assisted a Nigeria-based criminal organization has...
Who Is Behind Pro-Ukrainian Cyberattacks on Iran? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alex Haynes Source: Daniren via Alamy Stock Photo COMMENTARY Ukrainian cyber forces have attacked Russian infrastructure and assets almost since the first...
Redefining the Human Factor in Cybersecurity
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Recovering from a Cybersecurity Incident
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Mandiant’s X account hacked by crypto Drainer-as-a-Service gang – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Cybersecurity firm and Google subsidiary Mandiant says its Twitter/X account was hijacked last week by a Drainer-as-a-Service (DaaS) gang in what it...
Cisco says critical Unity Connection bug lets attackers get root – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Cisco has patched a critical Unity Connection security flaw that can let unauthenticated attackers remotely gain root privileges on unpatched...
Fidelity National Financial: Hackers stole data of 1.3 million people – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Fidelity National Financial (FNF) has confirmed that a November cyberattack (claimed by the BlackCat ransomware gang) has exposed the data...
Pro-Ukraine hackers breach Russian ISP in revenge for KyivStar attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A pro-Ukraine hacktivist group named ‘Blackjack’ has claimed a cyberattack against Russian provider of internet services M9com as a direct...
Ivanti warns of Connect Secure zero-days exploited in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Ivanti has disclosed two Connect Secure (ICS) and Policy Secure zero-days exploited in the wild that can let remote attackers...
Fake 401K year-end statements used to steal corporate credentials – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Threat actors are using communication about personal pension accounts (the 401(k) plans in the U.S.), salary adjustments, and performance reports...