Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Michele Campobasso, Luca Allodi Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the...
Day: January 9, 2024
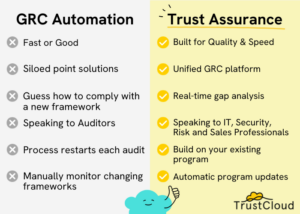
The CISO’s Guide to a Modern GRC Program with Trust Assurance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Erin Crapser The position of CISO is not an enviable one. Modern CISOs face enormous challenges like managing the complexity of on-prem...
Mastering the ‘cd’ Command: Tips and Tricks for Efficient Directory Navigation – Source: securityboulevard.com
Source: securityboulevard.com – Author: CyB3rBEA$T Navigating through directories is a fundamental aspect of working in a command-line interface, and the ‘cd’ command plays a crucial role...
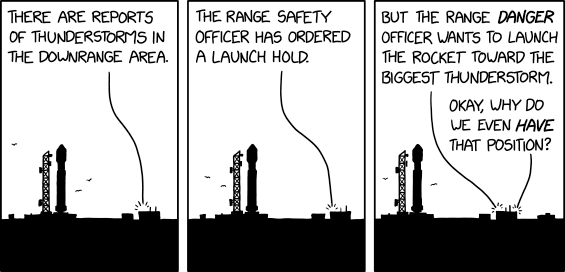
Randall Munroe’s XKCD ‘Range Safety’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
Secure Your Secrets with .env – Source: securityboulevard.com
Source: securityboulevard.com – Author: Greg Bulmash Using environment variables to store secrets instead of writing them directly into your code is one of the quickest and...
NIST: Better Defenses are Needed for AI Systems – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The accelerating development and expanding deployment of AI systems is creating significant security and privacy risks that aren’t being mitigated...
NIS2 Compliance: Updated for 2024, Complete Guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Flare The Network Information Systems Directive (NIS) was published in 2016 and required EU critical infrastructure sectors to meet basic cybersecurity compliance...
USENIX Security ’23 – Zixin Wang, Danny Yuxing Huang, Yaxing Yao – ‘Exploring Tenants’ Preferences of Privacy Negotiation in Airbnb’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
NYS: Clinic Must Pay $450K Fine, Spend $1.2M on Security – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific State AG Settlement Comes After 2021 Lorenz Ransomware Attack on Health Center...
Live Webinar | Securing the Cloud: Mitigating Vulnerabilities for Government – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
LoanDepot Hit by Ransomware Attack; Multiple Systems Offline – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Incident & Breach Response , Security Operations Large Mortgage Lender’s Customers Say the Online Payment Portable Is Inaccessible Mathew J. Schwartz...
BreachForums Boss Jailed for Violating Release Requirements – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime Conor Fitzgerald Allegedly Violated Computer Monitoring Requirement, VPN Ban Mathew J. Schwartz (euroinfosec) • January...
QNAP Patches High-Severity Flaws in QTS, Video Station, QuMagie, Netatalk Products – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire QNAP has released patches for a dozen vulnerabilities in its products, including several high-severity flaws. The post QNAP Patches High-Severity...
Turkish Cyberspies Targeting Netherlands – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Turkish state-sponsored group Sea Turtle has been targeting multiple organizations in the Netherlands for espionage. The post Turkish Cyberspies Targeting...
Major IT, Crypto Firms Exposed to Supply Chain Compromise via New Class of CI/CD Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Self-hosted GitHub Actions runners could allow attackers to inject malicious code into repositories, leading to supply chain attacks. The post...
NIST: No Silver Bullet Against Adversarial Machine Learning Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs NIST has published guidance on adversarial machine learning (AML) attacks and mitigations, warning that there is no silver bullet. The...
How to Get Started With Security Automation: Consider the Top Use Cases Within Your Industry – Source: www.securityweek.com
Source: www.securityweek.com – Author: Marc Solomon Organizations in different industries may approach security automation from a different entry point, but the requirements for an automation platform...
CISO Conversations: Jason Rebholz and Jason Ozin From the Insurance Sector – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend SecurityWeek interviews two CISOs from the insurance sector: Jason Rebholz at Corvus Insurance and Jason Ozin at UK-based PIB Group....
Lebanon Airport Screens Display Anti-Hezbollah Message After Being Hacked – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press The information display screens at Beirut’s international airport were hacked by domestic anti-Hezbollah groups. The post Lebanon Airport Screens Display...
Vulnerability Handling in 2023: 28,000 New CVEs, 84 New CNAs – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A total of more than 28,000 CVE IDs were assigned in 2023 and 84 new CVE Numbering Authorities (CNAs) were...
The latest cyber kidnapping victim, U.S. exchange student – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In the U.S. state of Utah, police discovered a teenage Chinese exchange student alone in a freezing cold tent,...
New Research: Tackling .NET Malware With Harmony Library – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have recently unveiled strategic insights into countering .NET malware through the innovative use of the Harmony library. The research,...
Anti-Hezbollah Groups Hack Beirut Airport Screens – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Beirut’s international airport faced a cyber-attack on Sunday, January 8, reportedly orchestrated by domestic anti-Hezbollah groups. The attack comes amid escalating tensions...
Turkish APT Sea Turtle Resurfaces, Spies on Dutch IT Firms – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Sea Turtle, a group of hackers aligned with the Turkish government, has returned after going undetected since 2020. Dutch cybersecurity provider,...
North Korean Hackers Stole $600m in Crypto in 2023 – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 North Korean hackers stole at least $600m in cryptocurrency in 2023, around a third of the total value of such heists,...
Merck Settles With Insurers Over $700m NotPetya Claim – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Merck has finally reached a settlement with its insurers after they had refused to pay out following the NotPetya campaign due...
Security Firm Certik’s Account Hijacked to Spread Crypto Drainer – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A Web3 security vendor was tricked by a social media phishing attack which hijacked its account and enabled scammers to share...