The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Day: January 6, 2024
H1 2023 Brief Overview of Main Incidents in Industrial CS
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Guiding Cyber Security From The Boardroom
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Guia de implementa o do SOC
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
AchievingGRC ExcellenceThe Roadmap to a Career in Governance,Risk, and Compliance
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The GDPR Playbook – Discover, Plan, and Act on the Upcoming EU Data Protection Regulation
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
GDPR Compliance Checklist
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Fuerza Laboral Ciberseguridad en una era de escacez de talento y habilidades
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The best cyber security event of the year – Register now! – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: You’re invited! The premiere cyber security event of the year awaits. Registration for CPX 2024 is open. This event...
Express Guide to Ransomware in Kubernetes
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Express Guide Kubernetes Backup Recovery
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Planning Considerations Cyber Incidents 2023 – Guidance for Emergency Managers
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Facilitating Global Interoperability of Cyber Regulations in the Electricity Sector – S Y S T E M S O F C Y B E R R E S I L I E N C E : E L E C T R I C I T Y I N I T I AT I V E P O S I T I O N P A P E R N O V E M B E R 2 0 2 3
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Experts spotted a new macOS Backdoor named SpectralBlur linked to North Korea – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts spotted a new macOS Backdoor named SpectralBlur linked to North Korea Researchers discovered a macOS backdoor, called SpectralBlur, which shows...
Merck settles with insurers regarding a $1.4 billion claim over NotPetya damages – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Merck settles with insurers regarding a $1.4 billion claim over NotPetya damages Merck has resolved a dispute with insurers regarding...
Law firm Orrick data breach impacted 638,000 individuals – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Law firm Orrick data breach impacted 638,000 individuals Law firm Orrick, Herrington & Sutcliffe disclosed a data breach that took...
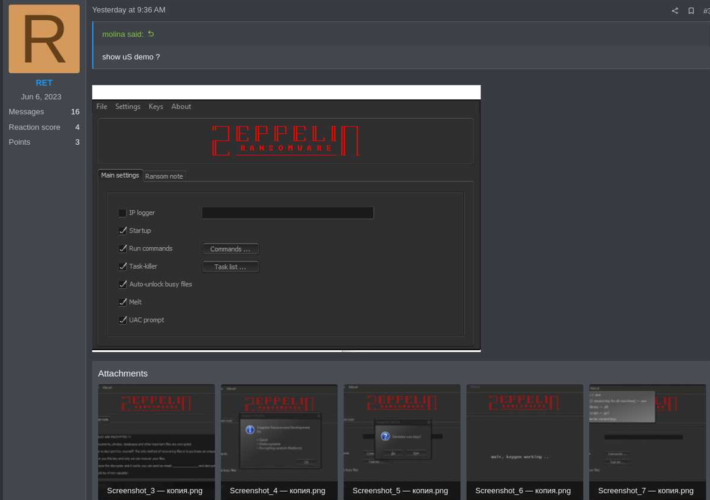
The source code of Zeppelin Ransomware sold on a hacking forum – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The source code of Zeppelin Ransomware sold on a hacking forum A threat actor announced the sale of the source...
Russia-linked APT Sandworm was inside Ukraine telecoms giant Kyivstar for months – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Russia-linked APT Sandworm was inside Ukraine telecoms giant Kyivstar for months Ukrainian authorities revealed that Russia-linked APT Sandworm had been inside...
Ivanti fixed a critical EPM flaw that can result in remote code execution – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Ivanti fixed a critical EPM flaw that can result in remote code execution Ivanti fixed a critical vulnerability in its...
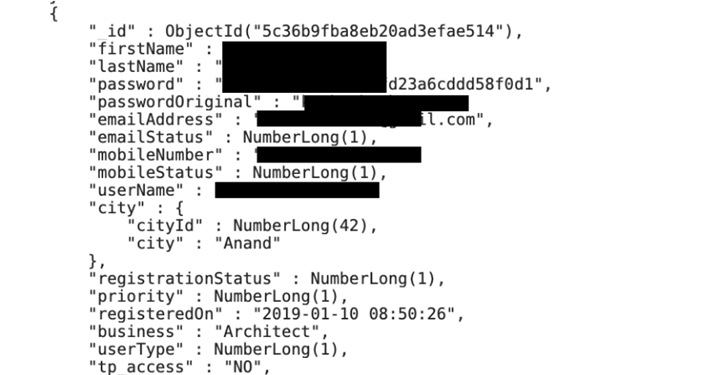
MyEstatePoint Property Search Android app leaks user passwords – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini MyEstatePoint Property Search Android app leaks user passwords The MyEstatePoint Property Search app leaked data on nearly half a million...
Apache ERP Zero-Day Underscores Dangers of Incomplete Patches – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Brain Light via Alamy Stock Photo Unknown groups have launched probes against a zero-day vulnerability identified in...
Airbus Looks to Acquire Atos Cybersecurity Unit for Nearly $2 Billion – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer 3 Min Read Source: Markus Mainka via Alamy Stock Photo Aerospace giant Airbus and French IT services company...
Russia Kyivstar Hack Should Alarm West, Ukraine Security Chief Warns – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading 1 Min Read Source: Skorzewiak via Alamy Stock Photo December’s cyberattack on Ukrainian telecommunications operator Kyivstar by...
Administrator Account for Middle East Internet Registry Hacked – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Science Photo Library via Alamy Stock Photo The Regional Internet Registry for Europe, the Middle East, and Central...
Mandiant’s X (Twitter) Account Hacked to Promote Crypto Scam – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Klaus Ohlenschlaeger via Alamy Stock Photo The X (Twitter) account of Google’s cybersecurity firm Mandiant was restored...
Navigating the New Age of Cybersecurity Enforcement – Source: www.darkreading.com
Source: www.darkreading.com – Author: Han Cho Source: Borka Kiss via Alamy Stock Photo COMMENTARY On Oct. 30, 2023, the Securities and Exchange Commission (SEC) shook the...
‘Cyber Toufan’ Hacktivists Leaked 100-Plus Israeli Orgs in One Month – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Issam Elhafti via Alamy Stock Photo Since mid-November, one Iran-linked hacktivist group has managed to breach more...
Friday Squid Blogging—18th Anniversary Post: New Species of Pygmy Squid Discovered – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Friday Squid Blogging—18th Anniversary Post: New Species of Pygmy Squid Discovered They’re Ryukyuan pygmy squid (Idiosepius kijimuna) and Hannan’s pygmy...
Improving Shor’s Algorithm – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier We don’t have a useful quantum computer yet, but we do have quantum algorithms. Shor’s algorithm has the potential to...
New iPhone Exploit Uses Four Zero-Days – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Kaspersky researchers are detailing “an attack that over four years backdoored dozens if not thousands of iPhones, many of which...