Source: securityaffairs.com – Author: Pierluigi Paganini A WhatsApp zero-day exploit can cost several million dollars TechCrunch reported that a working zero-day exploit for the popular WhatsApp...
Year: 2023
CISA adds JetBrains TeamCity and Windows flaws to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA adds JetBrains TeamCity and Windows flaws to its Known Exploited Vulnerabilities catalog The U.S. CISA added JetBrains TeamCity and...
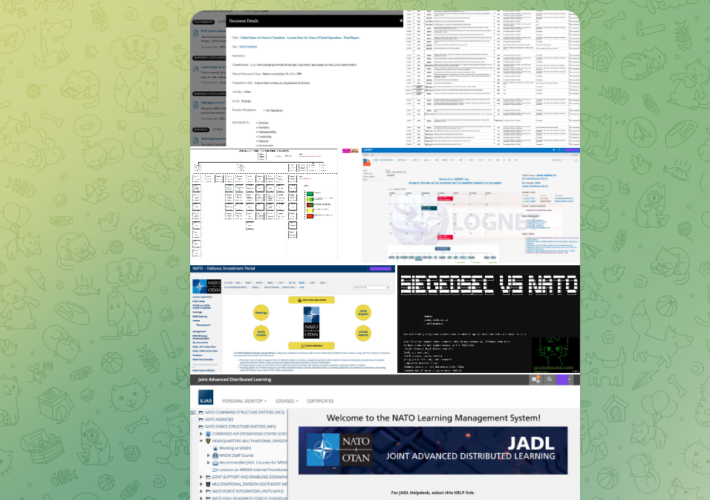
NATO is investigating a new cyber attack claimed by the SiegedSec group – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini NATO is investigating a new cyber attack claimed by the SiegedSec group NATO is investigating claims that a group called...
Global CRM Provider Exposed Millions of Clients’ Files Online – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Global CRM Provider Exposed Millions of Clients’ Files Online Researcher discovered that global B2B CRM provider Really Simple Systems exposed...
Sony sent data breach notifications to about 6,800 individuals – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Sony sent data breach notifications to about 6,800 individuals Sony Interactive Entertainment has notified current and former employees and their family...
Cybersecurity Awareness Month: How Large Language Models Will Kill Email Once and for All. Maybe. – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tristan Morris October 5, 2023 Guest Blogger: Aubrey King | Community Evangelist | F5 This Cybersecurity Awareness Month, join GuidePoint Security for...
CISA and NSA Offer MFA and SSO Guidelines for Developers, Vendors – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Developers and tech vendors need to improve multifactor authentication (MFA) and single sign-on (SSO) tools and make them easier for...
DEF CON 31 – Katitza Rodriguez’, Bill Budington’s ‘UNConventional Cybercrime – Bad Treaty Becoming Law’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/10/def-con-31-katitza-rodriguez-bill-budingtons-unconventional-cybercrime-bad-treaty-becoming-law/ Category & Tags: Security Bloggers Network,Cybersecurity,cybersecurity education,DEF...
Kaseya DattoCon Day 2 Highlights: Titans of MSP, Cybersecurity Insights & Looking Ahead – Source: securityboulevard.com
Source: securityboulevard.com – Author: newscred Welcome back to our journey through Kaseya DattoCon 2023, which took place right in Kaseya’s hometown city of Miami. Day two...
Securing your competitive advantage with Sift – Source: securityboulevard.com
Source: securityboulevard.com – Author: Coby Montoya Transitioning from legacy fraud solutions like Kount may be easier than you think. Fraud solution offerings have come a long...
Randall Munroe’s XKCD ‘Odyssey’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/10/randall-munroes-xkcd-odyssey/ Category & Tags: Humor,Security Bloggers Network,Randall Munroe,Sarcasm,satire,XKCD...
An In-Depth Exploration of ARMOR Level 4: Automated Prevention – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joel Wong With today’s unpredictable and evolving cybersecurity landscape, Swimlane understands that people alone can’t solve the critical challenges afflicting today’s security...
How Healthcare Threats Are Going Low – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland When it comes to IT and cybersecurity, few industries can compare to Healthcare. A diverse fleet of high-value devices, supporting...
FedRAMP and StateRAMP Authorized Part III The Journey to FedRAMP is Arduous — When and Why Should You Bother? – Source: securityboulevard.com
Source: securityboulevard.com – Author: CISO Global October 5, 2023 Author: Baan Alsinawi, CISSP, CCSP, CISM, CGEIT, CASP+ ce, and Managing Director at CISO Global You’re in...
Welcome Wes Wright: Another Great Day at Ordr – Source: securityboulevard.com
Source: securityboulevard.com – Author: Pandian Gnanaprakasam Ordr welcomes Wes Wright as our new Chief Healthcare Officer with immense pleasure and pride. Wes’s distinguished military background, extensive...
Hospital Lobbyists Press Senator on Online Tracking Limits – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , HIPAA/HITECH , Privacy Sen. Bill Cassidy Considering Sector Feedback on Recent RFI Marianne Kolbasuk McGee (HealthInfoSec)...
Joe Sullivan: What’s a Breach? ‘It’s a Complicated Question’ – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Incident & Breach Response , Security Operations The Question is Also One for the Legal Team to Own, Says Uber’s Former...
Clorox Expects Double-Digit Sales Drop Following Cyberattack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Ransomware Bleach Manufacturing Giant Spent $25M Cleaning Up Huge Cyberattack in Initial Weeks Michael...
Breach Roundup: Still Too Much ICS Exposed on the Internet – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management Also, Apple and Qualcomm Issue Emergency Patches Anviksha More (AnvikshaMore)...
Attackers Exploiting Atlassian Confluence Software Zero-Day – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , Breach Notification , Cybercrime Critical Privilege Escalation Bug Helps Create Admin Accounts Mihir Bagwe (MihirBagwe) •...
Smashing Security podcast #342: Royal family attacked, keyless car theft, and a deepfake Tom Hanks – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Is a deepfake Tom Hanks better than the real thing? Who has been attacking the British Royal Family’s website, and...
QakBot Threat Actors Still in Action, Using Ransom Knight and Remcos RAT in Latest Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 05, 2023NewsroomRansomware / Malware Despite the disruption to its infrastructure, the threat actors behind the QakBot malware have been linked...
Cisco Releases Urgent Patch to Fix Critical Flaw in Emergency Responder Systems – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 05, 2023NewsroomNetwork Security / Software Patch Cisco has released updates to address a critical security flaw impacting Emergency Responder that...
Analysis and Config Extraction of Lu0Bot, a Node.js Malware with Considerable Capabilities – Source:thehackernews.com
Source: thehackernews.com – Author: . Nowadays, more malware developers are using unconventional programming languages to bypass advanced detection systems. The Node.js malware Lu0Bot is a testament...
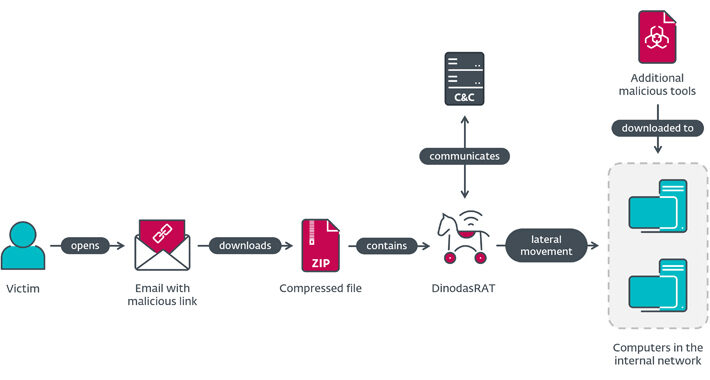
Guyana Governmental Entity Hit by DinodasRAT in Cyber Espionage Attack – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 05, 2023NewsroomCyber Espionage / Cyber Threat A governmental entity in Guyana has been targeted as part of a cyber espionage...
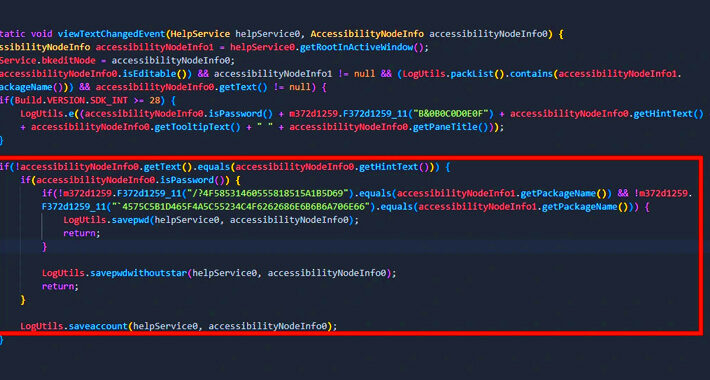
GoldDigger Android Trojan Targets Banking Apps in Asia Pacific Countries – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 05, 2023NewsroomMobile Security / crypto A new Android banking trojan named GoldDigger has been found targeting several financial applications with...
Unkillable? Qakbot Infections Fly On Even After Its High-Profile Raid – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading The Qakbot (aka Qbot) first-stage malware operation is still kicking, even after the “Operation Duck Hunt”...
Critical Zero-Day Bug in Atlassian Confluence Under Active Exploit – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading A critical privilege-escalation vulnerability in Atlassian Confluence Server and Confluence Data Center has been disclosed,...
Could Cybersecurity Breaches Become Harmless in the Future? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Vishal Gupta, CEO & Co-Founder, Seclore According to IBM’s latest “Cost of a Data Breach Report,” the cost of a breach has...
AWS Plans Multifactor Authentication Mandates for 2024 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Amazon Web Services announced that starting mid-2024, root users of an AWS Organization account will be required...