Source: securityboulevard.com – Author: Michael Vizard Protect AI this week added three open source tools to detect threats to artificial intelligence (AI) models that are aimed...
Year: 2023
Daniel Stori’s ‘End Of The World’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/10/daniel-storis-end-of-the-world-2/ Category & Tags: Humor,Security Bloggers Network,Daniel Stori,Sarcasm,satire,turnoff.us...
BTS #14 – Protecting The Federal Supply Chain – John Loucaides – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Why Automotive Companies Must Prioritize Secrets Detection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Soujanya Ain Today’s cars have come a long way from pure machines run by gears and engines. They’ve evolved into a platform...
iPhone/iPad Warning: Update Now to Avoid Zero-Day Pain – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings iOS 17.0.3 fixes yet more nasty zero-days (and the overheating bug). Apple has updated iOS 17 again, patching two zero-day...
DEF CON 31 – Dan Borgogno’s, Ileana Barrionuevo’s ‘Turning My Virtual Wallet Into A Skimming Device’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
User Protection: Removing the Security Burden From Users – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Eric Eddy, principal technical marketing engineer at Cisco, discusses critical aspects of user-centric security. From alleviating the security burden on users...
ISACA Security Survey 2023: Technical Skills Gaps, Budgeting – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Professional Certifications & Continuous Training , Training & Security Leadership , Video ISACA’s Jon Brandt Discusses Threat Trends, Hiring Challenges, New...
Executive Insights into Manufacturing Cybersecurity with Rockwell Automation and Dragos – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Robert Lee CEO and Co-Founder, Dragos Robert is a recognized authority in the industrial cybersecurity community. He is CEO and co-founder...
ISMG Editors: Can Governments Get a Handle on AI? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Standards, Regulations & Compliance Also: EU Policy Updates and...
China-Linked APT Uses New Backdoor for Espionage in Guyana – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Attackers Use Previously Undocumented Backdoor as Well as Traditional Hacking Tools Mihir...
Revealed! The top 10 cybersecurity misconfigurations, as determined by CISA and the NSA – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley A joint cybersecurity advisory from the United States’s National Security Agency (NSA) and Cybersecurity and Infrastructure Security Agency (CISA) has...
Lyca Mobile Affected by Cyberattack – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Lyca Mobile has released a statement about an unexpected disruption on its network caused by a cyberattack that may have...
PoC Exploits Released for Major Linux Flaw – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu On the majority of Linux distributions, proof-of-concept attacks for a high-severity vulnerability in the dynamic loader of the GNU C...
Access-as-a-Service: How to Keep Access Brokers Away from Your Organization – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Popa An attacker’s access to the network is often traced back to a succession of events, which network defenders must unravel....
Drive-by Download Attack – What It Is and How It Works – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Popa In today’s digital age, cybersecurity is more important than ever before. Unfortunately, cybercriminals are constantly finding new ways to infiltrate...
North Korea’s Lazarus Group Launders $900 Million in Cryptocurrency – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 06, 2023NewsroomCyber Crime / Cryptocurrency As much as $7 billion in cryptocurrency has been illicitly laundered through cross-chain crime, with...
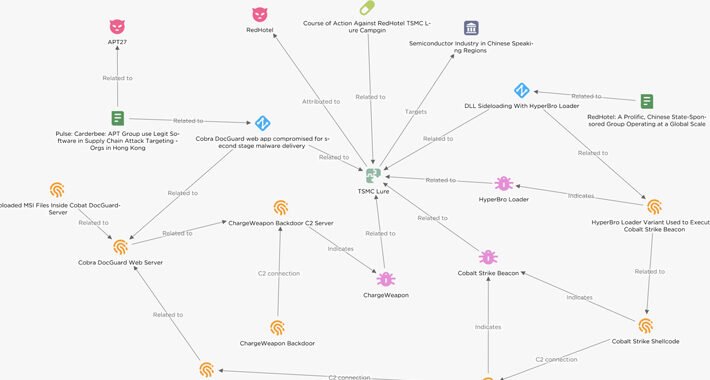
Chinese Hackers Target Semiconductor Firms in East Asia with Cobalt Strike – Source:thehackernews.com
Source: thehackernews.com – Author: . Oct 06, 2023NewsroomCyber Attack / Malware Threat actors have been observed targeting semiconductor companies in East Asia with lures masquerading as...
Microsoft Redesigns OneDrive for Business Layout – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse on October 5, 2023, 4:06 PM EDT Microsoft Redesigns OneDrive for Business Layout Microsoft OneDrive is adding new SharePoint features...
‘Operation Jacana’ Reveals DinodasRAT Custom Backdoor – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading A fresh malware threat dubbed “DinodasRAT” has been uncovered, after being used in a targeted...
Quash EDR/XDR Exploits With These Countermeasures – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ricardo Villadiego, Founder and CEO of Lumu In early 2023, a user named “spyboy” promoted a tool for evading endpoint defense on...
Legions of Critical Infrastructure Devices Subject to Cyber Targeting – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading There are at least 100,000 industrial control systems (ICS) exposed to the public Internet around...
10 Routine Security Gaffes the Feds Are Begging You to Fix – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The National Security Agency (NSA) and Cybersecurity and Infrastructure Security Agency (CISA) have issued a plea to...
Madagascar Drops Predator Spyware on Citizens in Watering Hole Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading Madagascar’s government services — such as police or domestic intelligence — have apparently purchased and leveraged Predator...
Group-IB: ‘GoldDigger’ Banking Trojan Targets Vietnamese Organizations – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Group-IB discovered an Android Trojan in August targeting more than 50 financial organizations in Vietnam that it’s...
Stealthy, Thieving Python Packages Slither Onto Windows Systems – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading A threat actor has been delivering a “relentless campaign” since early April to seed the software supply...
Critical ‘ShellTorch’ Flaws Light Up Open Source AI Users, Like Google – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading A newly discovered set of critical vulnerabilities in a machine learning framework known as TorchServe could allow...
Microsoft officially removes Cortana for Windows 11 Insiders – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft finally removed the Cortana standalone app from Windows 11 in the latest preview build for Insiders in the Canary...
Exploits released for Linux flaw giving root on major distros – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Proof-of-concept exploits have already surfaced online for a high-severity flaw in GNU C Library’s dynamic loader, allowing local attackers to...
China-linked cyberspies backdoor semiconductor firms with Cobalt Strike – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Hackers engaging in cyber espionage have targeted Chinese-speaking semiconductor companies with TSMC-themed lures that infect them with Cobalt Strike beacons....