The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Year: 2023
DIRECTOR MASTER PLAN OF SECURITY BY INCIBE & SPAIN GOVERNMENT. (translated version from the original document in Spanish).
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Quick Start Guide to Penetration Testing with NMAP , OpenVAS & Metaexploit by Sagar Rahalkar – Apress
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
IACS Cyber Security Incident Response Playbook
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Things of the Internet Global Cyber Domain Report by DNSSense – H2 – 2022 Report
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Hacking Practical Guide for beginners by Jeff Simon
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity Terms – Quick guide to CyberSecurity MUST KNOW – ENTRY-LEVEL TERMS by Chris Romano
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Cyber Dimensions of the Russia-Ukraine War by European Cyber Conflict Research Initiative (ECCRI).
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Quality Assurance for Software Development Must Include Cybersecurity – Why Cybersecurity and Software Quality Assurance Go Together ? by Anish Roy
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Are Quality and Security Synonymous in Software by Zeronorth
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Phishing Dark Waters – The Offensive and Defensive Sides of Maliciosus Emails
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
OWASP PRO Active Controls for Developers v. 3 – Securing Coding Best Practices – 10 Critical Security Areas where developers must know and follow the recommendatios mandatory
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Perfect Weapon – WAR, SABOTAGE and FEAR in the Cyber Age by David E. Sanger
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
TESLA Cars Cyber Security – Threats Vulnerabilities Hacking Protection by Dror Amrami
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Security Implications of ChatGPT RC by Cloud Security Alliance – CSA
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
New to Cyber Field Manaul – The Ultimate Guide to Getting Into Cybersecurity by SANS GIAC
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Hacking Connected Cars – Tactics, Techniques and Procedures by Alissa Knight – Wiley
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Complete Guide to Understanding Apple Mac Security for Enterprise by SentinelOne
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity Preparedness in Critical Infraestructure – Avoinding The Big Shutdown
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity and the role of the Board of Directors in Latin America and the Caribbean – ECLAC
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Security Incident Information Management Handbook
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Artificial Intelligence and Cybersecurity Technology, Governance and Policy Challenges
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Ultimate Guide to Information Security and Continuity
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Professional Penetration Testing – Creating and Operating a Formal Hacking Lab
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
DoD Cyber Strategy Summary 2023
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
2023 – Cyber Strategy of The Departament of Defence
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Active Directory Handbook
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
COSO Guidance Risk Appetite Critical to Success
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
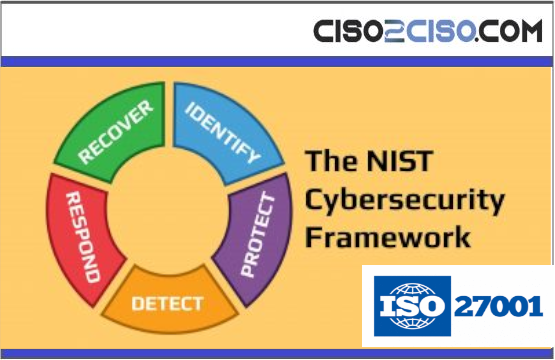
CybersecurityFrameworks
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SOFTWARE SUPPLY CHAIN SECURITY THREAT LANDSCAPE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...