Source: www.bleepingcomputer.com – Author: Bill Toulas Three malicious Chrome extensions posing as VPN (Virtual Private Networks) infected were downloaded 1.5 million times, acting as browser hijackers,...
Month: December 2023
Preparing for the Holiday Ransomware Storm – Source: securityboulevard.com
Source: securityboulevard.com – Author: claude.mandy This article was originally published on Spiceworks. The holiday season is upon us. As we approach the end of 2023, it...
USENIX Security ’23 ‘The Digital-Safety Risks Of Financial Technologies For Survivors Of Intimate Partner Violence’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the organizations strong commitment to Open...
Data Classification Software Features to Look Out For – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cavelo Blog For organizations looking to improve their data protection and data compliance strategies, technology is essential. Implementation of the right software...
How Cybersecurity for Law Firms has Changed – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cavelo Blog The public nature of the legal system makes law firms particularly vulnerable to a growing number of cybersecurity risks. Law...
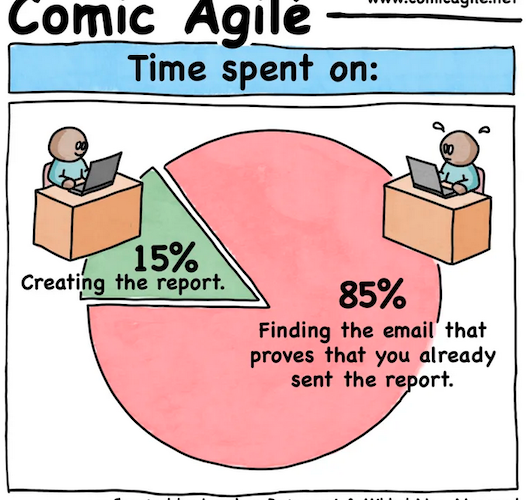
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnaravi – #271 — Time Spent On – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
Preparing for the Holiday Ransomware Storm – Source: securityboulevard.com
Source: securityboulevard.com – Author: claude.mandy This article was originally published on Spiceworks. The holiday season is upon us. As we approach the end of 2023, it...
What is return fraud, and how can businesses fight it? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sift Trust and Safety Team Have you ever felt the frustration of dealing with deceitful return practices? You’re not alone—most retailers are...
Threat modeling: the future of cybersecurity or another buzzword⎥Derek Fisher (author of The Application Security Handbook) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alexandra Charikova Welcome to the Elephant in AppSec, the podcast to explore, challenge, and boldly face the AppSec Elephants in the room....
USENIX Security ’23 – Sophie Stephenson, Majed Almansoori, Pardis Emami-Naeini, Danny Yuxing Huang, Rahul Chatterjee ‘Abuse Vectors: A Framework For Conceptualizing IoT-Enabled Interpersonal Abuse’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
Web Injection Campaign Targets 40 Banks, 50,000 Users – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Dozens of banks around the word are in the crosshairs of a threat group using JavaScript web injections to steal...
Millions of Patients Affected in Double-Extortion Attack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific Hackers Crippled Systems, Stole Patient Data From ESO Solutions Rashmi Ramesh (rashmiramesh_)...
Teen Uber Hacker Sent to Indefinite Hospital Detention – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Arion Kurtaj Was a Member of Lapsus$ Group That Also Hacked Nvidia and Revolut Akshaya Asokan (asokan_akshaya) • December 22, 2023...
Iranian Hackers Peach Sandstorm Are Delivering New Backdoor – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime FalseFont Backdoor Enables Attackers to Remotely Connect to a Compromised System Prajeet...
Report Warns of ‘Catastrophic’ Medical Device Security Risks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Business Continuity Management / Disaster Recovery , Critical Infrastructure Security , Endpoint Security Majority of Connected Medical Devices Contain Critical Vulnerabilities,...
Rogue WordPress Plugin Exposes E-Commerce Sites to Credit Card Theft – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 22, 2023NewsroomSkimming / Web Security Threat hunters have discovered a rogue WordPress plugin that’s capable of creating bogus administrator users...
Operation RusticWeb: Rust-Based Malware Targets Indian Government Entities – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 22, 2023NewsroomMalware / Cyber Threat Indian government entities and the defense sector have been targeted by a phishing campaign that’s...
Decoy Microsoft Word Documents Used to Deliver Nim-Based Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 22, 2023NewsroomSocial Engineering / Malware Analysis A new phishing campaign is leveraging decoy Microsoft Word documents as bait to deliver...
Ben Rothke’s Review of A Hacker’s Mind – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...
Data Exfiltration Using Indirect Prompt Injection – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Interesting attack on a LLM: In Writer, users can enter a ChatGPT-like session to edit or create their documents. In...
Breach Roundup: MongoDB Blames Phishing Email for Breach – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Every week, Information Security Media Group rounds up cybersecurity incidents and breaches around the world. This week:, MongoDB said a phishing...
NIST Report Spotlights Cyber, Privacy Risks in Genomic Data – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Healthcare , Industry Specific A Multitude of Considerations for Entities As Use of Genomic Data Advances...
UK Teen Gets Indefinite Hospital Order For ‘Grand Theft Auto’ Hack – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP Arion Kurtaj was found responsible by a British court of carrying out one of the biggest breaches in the history of...
In Other News: Crypto Exchange Hack Guilty Plea, Rating AI Vulnerabilities, Intellexa Spyware – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News Noteworthy stories that might have slipped under the radar: Cryptocurrency exchange hacker pleads guilty, rating LLM vulnerabilities, Intellexa spyware analysis....
Iranian Hackers Targeting US Defense Industrial Base Entities With New Backdoor – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Microsoft has observed Iranian state-sponsored hackers targeting employees at US DIB entities with the FalseFont backdoor. The post Iranian Hackers...
Inmate, Staff Information Stolen in Rhode Island Prison Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Donald W. Wyatt Detention Facility says the data of 2,000 inmates, staff, and vendors was stolen in a cyberattack....
CISA Warns of FXC Router, QNAP NVR Vulnerabilities Exploited in the Wild – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs CISA released ICS advisories for FXC router and QNAP NRV flaws and added them to its known exploited vulnerabilities catalog. ...
Malicious GPT Can Phish Credentials, Exfiltrate Them to External Server: Researcher – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A researcher has shown how malicious actors can create custom GPTs that can phish for credentials and exfiltrate them to...
Cisco to Acquire Isovalent, Add eBPF Tech to Cloud Portfolio – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Isovalent raised about 70 million in funding from prominent investors including Microsoft’s venture fund, Google, and Andreessen Horowitz. The post...
Strengthening Resilience: Navigating the Cybersecurity Landscape – Source: www.darkreading.com
Source: www.darkreading.com – Author: David Molony Source: Science Photo Library via Alamy Stock Photo Over the last four years, businesses have faced significant challenges characterized by...