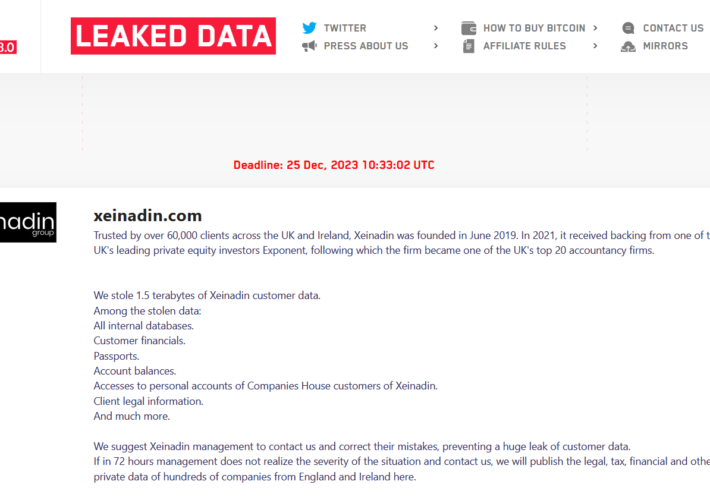
Source: securityaffairs.com – Author: Pierluigi Paganini LockBit ransomware gang claims to have breached accountancy firm Xeinadin Pierluigi Paganini December 23, 2023 The LockBit ransomware claims to...
Month: December 2023
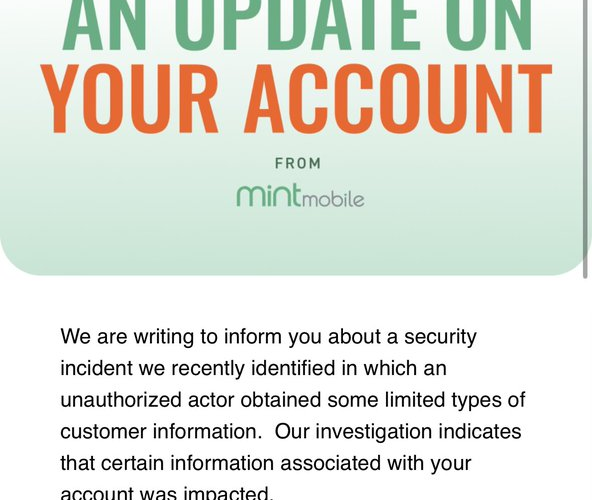
Mobile virtual network operator Mint Mobile discloses a data breach – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Mobile virtual network operator Mint Mobile discloses a data breach Pierluigi Paganini December 23, 2023 Mobile virtual network operator Mint...
Group Therapy – security and privacy in Facebook groups – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Harley Having found myself roped into assisting as co-administrator a couple of Facebook groups with security/privacy issues, I thought I should,...
Best Practices in Multi-Factor Authentication for Enhanced Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Toback Imagine standing at the entrance to a vault where your most valuable possessions are stored. The door doesn’t open with...
USENIX Security ’23 – ‘“It’s The Equivalent of Feeling Like You’re In Jail”: Lessons From Firsthand & Secondhand Accounts Of IoT-Enabled Intimate Partner Abuse’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Full Presenter List: Sophie Stephenson, Majed Almansoori, Pardis Emami-Naeini, Rahul Chatterjee Many thanks to USENIX for publishing their outstanding USENIX...
Impact of Apache Struts2 Code Execution Vulnerability – Source: securityboulevard.com
Source: securityboulevard.com – Author: Riddika Grover Recent attacks have demonstrated a significant growth in Zero Days and Remote Code Execution. Kratikal has observed that threat actors...
Kansas City Hospital Ransomware Attack Consequences – Source: securityboulevard.com
Source: securityboulevard.com – Author: Axio Cloud Security, Governance and Skills in 2024 Step 1 of 6 16% Who in your organization is responsible for cloud security?...
Establish Security Outcomes With Data Discovery and Classification – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cavelo Blog And the real-life challenges midsized enterprises are juggling as they scale to achieve them The practice of data discovery and...
Friday Squid Blogging: Squid Parts into Fertilizer – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments &ers • December 22, 2023 5:30 PM @ALL Common sense won. hxxps://news.err.ee/1609202272/interior-abandons-plan-to-ban-non-personalized-prepaid-sim-cards How is this at your side?...
‘Wall of Flippers’ detects Flipper Zero Bluetooth spam attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new Python project called ‘Wall of Flippers’ detects Bluetooth spam attacks launched by Flipper Zero and Android devices. By...
Chameleon Android Malware Can Bypass Biometric Security – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A variant of the Chameleon Android banking trojan features new bypass capabilities and has expanded its targeting area. The post...
Ransomware Attackers Abuse Multiple Windows CLFS Driver Zero-Days – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: cryptoFX via Alamy Stock Photo In the last year and a half, attackers have exploited at least...
Cisco Bets Big on Multicloud Security With Isovalent Deal – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Aleksey Funtap via Alamy Stock Photo Cisco is closing out a busy year of acquisitions with a new...
Google Releases Eighth Zero-Day Patch of 2023 for Chrome – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer Source: PREMIO STOCK via Shutterstock Google has issued an urgent update to address a recently discovered vulnerability in...
Expert Tony Sabaj on Managed Security Service Providers – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Anthony (Tony) Sabaj is currently the Head of Channel Security Engineering for the Americas at Check Point, with over 25 years...
ESET Threat Report: ChatGPT Name Abuses, Lumma Stealer Malware Increases, Android SpinOk SDK Spyware’s Prevalence – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet Cybersecurity company ESET released its H2 2023 threat report, and we’re highlighting three particularly interesting topics in it: the abuse...
20 Most Popular TechRepublic Articles in 2023 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Staff Here’s a list of the 20 most popular articles published by TechRepublic in 2023. Read articles about ChatGPT, Google Bard,...
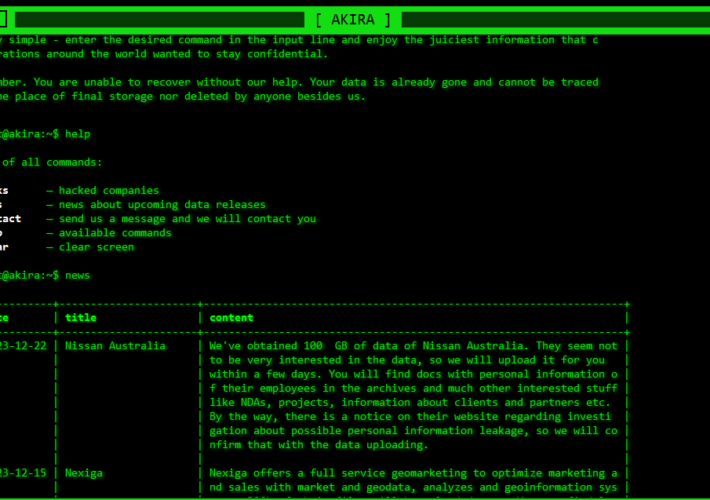
Akira ransomware gang claims the theft of sensitive data from Nissan Australia – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Akira ransomware gang claims the theft of sensitive data from Nissan Australia Pierluigi Paganini December 22, 2023 The Akira ransomware...
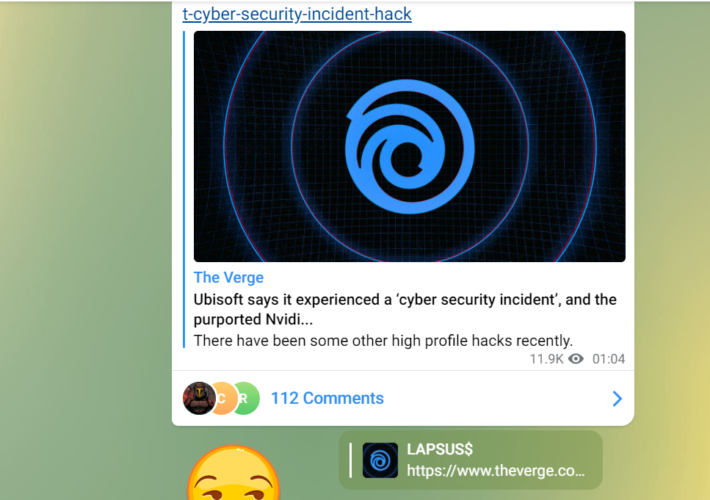
Member of Lapsus$ gang sentenced to an indefinite hospital order – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Member of Lapsus$ gang sentenced to an indefinite hospital order Pierluigi Paganini December 22, 2023 A member of the Lapsus$...
Real estate agency exposes details of 690k customers – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Real estate agency exposes details of 690k customers Pierluigi Paganini December 22, 2023 An exposed instance contained information for a...
How to BUILD Next-Gen SOC
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
How To Communicate Cybersecurity Risk To Your Board Of Directors
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Top Threats to Cloud Computing: Pandemic 11 Deep Dive
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The CISO’s Guide to Third-Party Security Management
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CISO PLAYBOOK: CYBER RESILIENCE GOVERNANCE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Mint Mobile discloses new data breach exposing customer data – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Mint Mobile has disclosed a new data breach that exposed the personal information of its customers, including data that can...
The Week in Ransomware – December 22nd 2023 – BlackCat hacked – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Earlier this month, the BlackCat/ALPHV ransomware operation suffered a five-day disruption to their Tor data leak and negotiation sites, rumored...
Ubisoft says it’s investigating reports of a new security breach – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Ubisoft is investigating whether it suffered a breach after images of the company’s internal software and developer tools were leaked...
Nissan Australia cyberattack claimed by Akira ransomware gang – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Today, the Akira ransomware gang claimed that it breached the network of Nissan Australia, the Australian division of Japanese car...
Europol warns 443 online shops infected with credit card stealers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Europol has notified over 400 websites that their online shops have been hacked with malicious scripts that steal debit and...