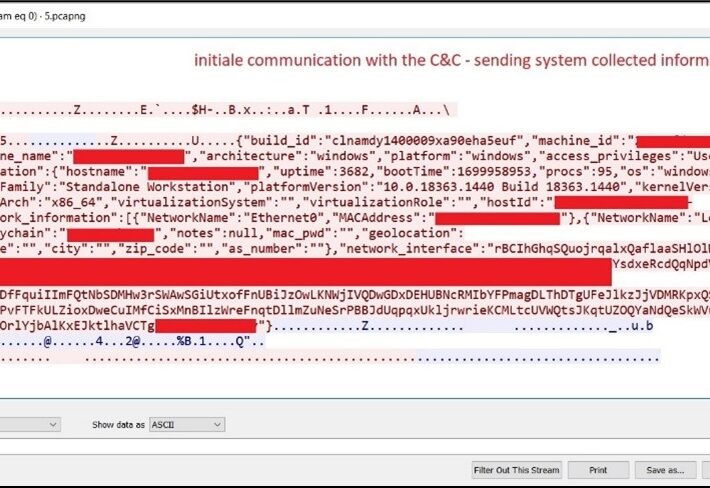
Source: www.darkreading.com – Author: PRESS RELEASE MARLTON, N.J., Dec. 20, 2023 /PRNewswire/ — Approximately 2.7 million patients are being notified that their Social Security numbers and other confidential information were compromised...
Month: December 2023
Black Hat Europe 2023 Closes on Record-Breaking Event in London – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE LONDON, Dec. 20, 2023 — Black Hat, the cybersecurity industry’s most established and in-depth security event series, today announced the...
Defiant BlackCat Gang Stands Up New Site, Calls for Revenge Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading 2 Min Read Source: Sari O’Neal via Alamy Stock Photo BlackCat/ALPHV ransomware leaders claim they have restarted...
Physical Access Systems Open Cyber Door to IT Networks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading 2 Min Read Source: Stephen Barnes Technology via Alamy Stock Photo Cyberattackers can exploit access...
Iranian ‘Seedworm’ Cyber Spies Target African Telcos & ISPs – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Leyden Source: Denis Crawford via Alamy Stock Photo An Iran-backed cyberespionage group is actively targeting telcos in North and East Africa....
Attackers Exploit 6-Year-Old Microsoft Office Bug to Spread Spyware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Robert Brown via Alamy Stock Photo Attackers are exploiting a 6-year-old Microsoft Office remote code execution (RCE)...
Targeted F5 Vulnerability ‘Update’ Delivers Wiper to Israeli Victims – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Ragma Images via Alamy Stock Photo Israel’s National Cyber Directorate (NCD) has issued an “urgent warning” about a targeted email...
3 Ways to Use Real-Time Intelligence to Defeat Bots – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nick Rieniets Source: Brain light via Alamy Stock Photo In the classic sci-fi film Blade Runner, bounty hunter Rick Deckard is tasked...
Google addressed a new actively exploited Chrome zero-day – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Google addressed a new actively exploited Chrome zero-day Pierluigi Paganini December 20, 2023 Google has released emergency updates to address...
German police seized the dark web marketplace Kingdom Market – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini German police seized the dark web marketplace Kingdom Market Pierluigi Paganini December 20, 2023 The German police seized the dark...
Law enforcement Operation HAECHI IV led to the seizure of $300 Million – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Law enforcement Operation HAECHI IV led to the seizure of $300 Million Pierluigi Paganini December 20, 2023 An international law...
Sophisticated JaskaGO info stealer targets macOS and Windows – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Sophisticated JaskaGO info stealer targets macOS and Windows Pierluigi Paganini December 20, 2023 JaskaGO is a new Go-based information stealer malware...
BMW dealer at risk of takeover by cybercriminals – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini BMW dealer at risk of takeover by cybercriminals Pierluigi Paganini December 20, 2023 By neglecting to set a password, a...
Why RV Connex Chose Swimlane As “The Powerhouse” Of Their SOC – Source: securityboulevard.com
Source: securityboulevard.com – Author: Katie Bykowski RV Connex is a Thailand-based company that specializes in national defense and space manufacturing. Since RV Connex has implemented security...
Attackers Finding Novel Ways to Abuse GitHub: ReversingLabs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Threat actors are finding new ways to take advantage of GitHub in hopes of tricking developers into putting malicious code...
CodeSecure Expands Automation Capabilities for Complying with Leading Embedded Software Safety and Security Standards – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Napolitano CodeSonar static application security testing (SAST) tool now provides integrated support for meeting MISRA C 2023 and JSF++ for C++...
USENIX Security ’23 – Claudio Anliker, Giovanni Camurati, and Srdjan Čapkun ‘Time for Change: How Clocks Break UWB Secure Ranging’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, December 20, 2023 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Exploring EMBA: Unraveling Firmware Security with Confidence – Source: securityboulevard.com
Source: securityboulevard.com – Author: Paul Asadoorian Introduction Firmware security analysis is a critical aspect of modern cybersecurity. As our devices become more interconnected and reliant on...
AppOmni Previews Generative AI Tool to Better Secure SaaS Apps – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard AppOmni this week unveiled a technology preview of a digital assistant to its platform for protecting software-as-a-service (SaaS) applications that...
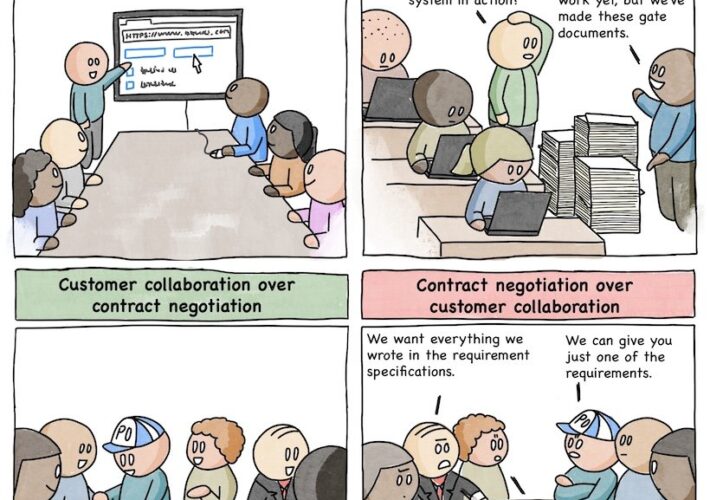
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnaravi – #270 — The Agile Manifesto – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, December 20, 2023 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Connecting the Dots: NIST SSDF, Self-Attestation, and a Complete ASPM Platform – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ronen Slavin In today’s hyper-connected world, secure software development is no longer an option, it’s a necessity. Yet achieving true security demands...
The Limitations of Google Play Integrity API (ex SafetyNet) – Source: securityboulevard.com
Source: securityboulevard.com – Author: George McGregor This overview outlines the history and use of Google Play Integrity API and highlights some limitations. We also compare and...
SSH FAIL: Terrapin Attack Smashes ‘Secure’ Shell Spec – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Lurking vuln in SSH spec means every implementation must build patches. A nasty vulnerability in a crucial bit of internet...
CISA Plans to Improve Threat Data-Sharing Approaches in 2024 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Government , Industry Specific , Next-Generation Technologies & Secure Development US Cyber Agency to Begin 2-Year Major Overhaul of Its Legacy...
NIST Seeks Public Comment on Guidance for Trustworthy AI – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Agency Calls for Information on Gen AI Risk Management, Red-Teaming...
Live Webinar | Enterprise Passkey Implementations: Key Considerations and Tradeoffs – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Live Webinar | A Master Class on IT Security: Roger Grimes Teaches Ransomware Mitigation – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware , Video Presented by KnowBe4 60 mins Cyber-criminals have become thoughtful...
UK Supreme Court Says AI Can’t Patent Inventions – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Court Says Only a ‘Person’ Can Be an Inventor Akshaya...
FTC Bans Rite Aid From Using Facial Recognition Tech – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Privacy , Standards, Regulations & Compliance 5-Year Ban Comes After Retailer Failed to Mitigate Security Surveillance...
FBI Disrupts BlackCat Ransomware Threat Group Activity – The Essential Facts – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși The U.S. Justice Department (DoJ) announced on December 19th that the Federal Bureau of Investigations had disrupted the BlackCat ransomware...